Lesson 4: Implementing Digital Signature and Encryption Capabilities
This lesson describes digital signatures and encryption and then explains how these capabilities enhance Exchange Server 2003 security. The lesson explains how public key infrastructure (PKI) is used to send digitally signed and encrypted e-mail messages. It also describes PKI components. Finally, the lesson describes how the enrollment process enables digital signature and encryption capabilities.
After this lesson, you will be able to
-
Explain what digital signature and encryption capabilities are
-
Explain what a PKI is
-
Describe the PKI components that enable digital signature and encryption capabilities
-
Describe how the enrollment process enables digital signature and encryption capabilities
-
Describe the process of creating and deploying digital signature and encryption certificates
-
Configure Outlook digital signature and encryption capabilities
Estimated lesson time: 30 minutes
Digital Signature and Encryption
Digital signature and encryption enable you to secure your messaging system by protecting e-mail messages from modification and inspection by malicious third parties as they are transmitted from the sender to the receiver.
A digital signature is a code attached to an e-mail message that ensures that the individual who is sending the message is really who he or she claims to be. The code is linked to the message content so that any modification of the content of the message during transit will result in an invalid signature.
You can protect e-mail messages against inspection by using encryption. Encryption is a cryptographic technique that translates the contents of an e-mail message into an unreadable format. There are many different types of encryption. Exchange implements public key encryption, which uses a public key that is known to everyone and a private key that is known only to the recipient of the message.
For example, when Don Hall wants to send a secure message to Kim Akers, Don uses Kim's public key to encrypt the message. Kim then uses her private key, known only by her, to decrypt Don's message. If a public key is used to encrypt messages, only the corresponding private key can be used to decrypt those messages. It is almost impossible to deduce a private key, even if you know the public key.
The function of real-world security is to make it very difficult for an attacker to breach the system. Remember that there is no known limit to human ingenuity and no system is perfect. Remember also that a private key is effective only if no third party knows it. The longer a private key exists, the more likely it is to be cracked.
Exchange Server 2003 and Outlook 2003 implement digital signature and encryption capabilities by using Secure Multi-Purpose Internet Mail Extensions (S/MIME), which is the version of the MIME protocol that supports encryption.
Public Key Infrastructure
A PKI is a policy that is used to establish a secure method for exchanging information. It is also an integrated set of services and administrative tools for creating, deploying, and managing public key–based applications. It includes cryptographic methods and a system for managing the process that enables you to identify users and securely exchange data.
PKI signature and encryption capabilities enable you to strengthen the security of your Exchange Server 2003 organization by protecting e-mail from being read by anyone other than the intended recipient or from being altered by anyone other than the sender while the message is in transit, or while the message is stored either on the client in a .pst file or on the Exchange server in the mailbox store.
A PKI includes components that enable digital signature and encryption capabilities. A PKI contains the components listed in Table 11-4.
| PKI component | Description |
|---|---|
| Digital certificate | Authenticates users and computers. |
| Certificate template | Defines the content and purpose of a certificate. Typically one certificate template is created for digital signatures and another is created for encryption. However, a single certificate template can be created for both purposes. |
| Certificate revocation list (CRL) | Lists the certificates that are revoked by a CA before the certificates reach their scheduled expiration date. |
| Certificate authority (CA) | Issues certificates to users, computers, and services, and then manages these certificates. |
| Certificate publication points and CRL distribution points | Provide locations where certificates and CRLs are made publicly available. Certificates and CRLs can be made available through a directory service, such as X.500, LDAP, or through directories that are specific to the operating system and Web servers. |
| Certificate and CA management tools | Manage issued certificates, publish CA certificates and CRLs, configure CAs, import and export certificates and keys, and recover archived private keys. |
| Applications and services that are enabled by public keys | Use certificates for e-commerce and secure network access by using digital signature and encryption capabilities. |
| Certificate servers | Enable you to create, issue, and manage certificates by using Microsoft Certificate Services. Using Certificate Services on Windows Server 2003 with Exchange Server 2003 integrates all of the certificate functionality into a single service, rather than relying on multiple services, such as Microsoft Key Management Service (KMS), which was required in previous versions of Exchange. The benefits of certificate servers include the following:
|
| Tip | When a PKI is checking the validity of a certificate, one of the first things it does is to check it against a CRL. If no CRL exists, an error may be returned. Therefore, you may need to issue a certificate and then revoke it to create a CRL before a PKI will operate correctly. |
Practice: Deploying Digital Signature and Encryption Certificates
Using a certificate for digital signatures or encryption requires that you deploy the certificate in Exchange Server 2003 by using auto-enrollment settings and that you verify the Outlook configuration. Before starting this practice, you need to obtain a certificate, if you have not already done so. To do this, open Internet Explorer, access http://Server01/Certsrv and complete the wizard. If Server01 is not a CA, you need to obtain a certificate over the Internet from an external CA, such as VeriSign.
Exercise 1: Implement Digital Signature and Encryption Capabilities on Exchange Server 2003
To configure Exchange Server 2003 to allow users to digitally sign and encrypt messages, perform the following steps:
-
Open the Certification Authority console on Server01.
-
Expand Tailspintoys.
-
Right-click Certificate Templates, point to New, and then click Certificate Template To Issue.
-
In the Enable Certificate Templates dialog box, click Exchange User, and then click OK.
-
In the Certification Authority console, right-click Certificate Templates, and then click Manage.
-
Right-click Exchange User in the details pane of the Certificate Templates console, and then click Properties.
-
Select the Security tab in the Exchange User Properties dialog box.
-
Click Authenticated Users in the Group Or User Names box.
-
In the Permissions For Authenticated Users box, select the Allow check box for the Enroll permission, as shown in Figure 11-7, and then click OK.
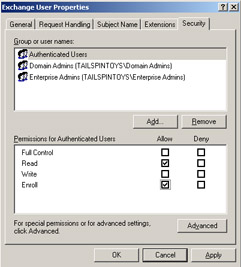
Figure 11-7: Allowing Authenticated Users Enroll permission so they can digitally sign and encrypt e-mail -
Close the Certificate Templates management list and the Certification Authority console.
Exercise 2: Configure Digital Signature and Encryption Capabilities on Outlook 2003
After you deploy the digital signing and encryption certificates, you can then configure Outlook to use the certificates to enable digital signature and encryption capabilities. This would normally be done on a client workstation. On your test network, you can do it on Server01.
To configure digital signature and encryption capabilities on Outlook, perform the following steps:
-
Open Outlook on Server01.
-
On the Tools menu, click Options.
-
On the Security tab of the Options dialog box, click Settings.
-
Type a name for the e-mail digital certificate (for example, mail-certificate) in the Security Settings Name box, or accept the default.
-
In Certificates and Algorithms in the Signing Certificate pane, click Choose beside Signing Certificate, select a signing certificate, and then in the Hash Algorithm box, select an algorithm.
-
In Certificates and Algorithms in the Signing Certificate pane, click Choose beside Encryption Certificate, select an encryption certificate, and then in the Hash Algorithm box, select an algorithm.
-
Click OK to close the Change Security Settings dialog box.
-
On the Security tab, in the Encrypted box, select or clear the check boxes as required. Figure 11-8 shows the available options.
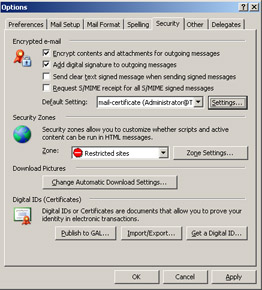
Figure 11-8: Encryption and signature options -
Click OK to close the Options dialog box.
Tip If the CA issues you a multipurpose certificate, you can designate the same certificate in both the Signing Certificate box and the Encryption Certificate box.
Lesson Review
The following questions are intended to reinforce key information presented in this lesson. If you are unable to answer a question, review the lesson materials and then try the question again. You can find answers to the questions in the "Questions and Answers" section at the end of this chapter.
-
Which PKI component defines the content and purpose of a certificate?
-
Certificate template
-
CA
-
CRL
-
Certificate publication point
-
-
Don Hall sends an encrypted message to Kim Akers. How does Don encrypt it, and how does Kim read it?
-
Kim Akers wants to send a message to Don Hall, but Don needs to be certain that the message really is from Kim. How can he verify this?
Lesson Summary
-
Encryption ensures that only the person for whom a message is intended can read it.
-
A digital signature proves the sender's identity and gives an assurance that the message has not been altered in transit.
-
Encryption and digital signatures are implemented using private and public key pairs, which are issued as certificates. Exchange Server 2003 supports this process by using a PKI.
EAN: 2147483647
Pages: 221