Section 12.2. MDB Concepts
12.2. MDB ConceptsThis section discusses the significant aspects of MDB's design and the benefits derived from this architecture. 12.2.1. Building BlocksMDB has several different types of building blocks which, when combined provide a flexible and extensible architecture. They include:
The following section describes each of these objects in more detail. 12.2.2. TargetsThe target is the program being inspected by the debugger. MDB currently provides support for the following types of targets:
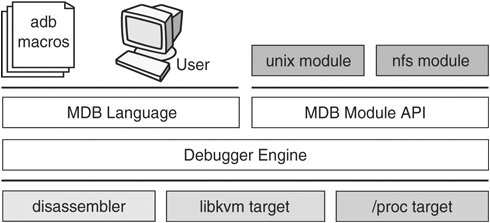
Each target exports a standard set of properties, including one or more address spaces, one or more symbol tables, a set of load objects, and a set of threads. Figure 12.1 shows an overview of the MDB architecture, including two of the built-in targets and a pair of sample modules. Figure 12.1. MDB Architecture
12.2.3. Debugger CommandsA debugger command, or dcmd (pronounced dee-command) in MDB terminology, is a routine in the debugger that can access any of the properties of the current target. MDB parses commands from standard input, then executes the corresponding dcmds. Each dcmd can also accept a list of string or numerical arguments, as shown in Section 13.2. MDB contains a set of built-in dcmds described in Section 13.2.5, that are always available. The programmer can also extend the capabilities of MDB itself by writing dcmds, using a programming API provided with MDB. 12.2.4. WalkerA walker is a set of routines that describe how to walk, or iterate, through the elements of a particular program data structure. A walker encapsulates the data structure's implementation from dcmds and from MDB itself. You can use walkers interactively or as a primitive to build other dcmds or walkers. As with dcmds, you can extend MDB by implementing additional walkers as part of a debugger module. 12.2.5. Debugger ModulesA debugger module, or dmod (pronounced dee-mod), is a dynamically loaded library containing a set of dcmds and walkers. During initialization, MDB attempts to load dmods corresponding to the load objects present in the target. You can subsequently load or unload dmods at any time while running MDB. MDB provides a set of standard dmods for debugging the Solaris kernel. 12.2.6. MacrosA macro file is a text file containing a set of commands to execute. Macro files typically automate the process of displaying a simple data structure. MDB provides complete backward compatibility for the execution of macro files written for adb. The set of macro files provided with the Solaris installation can therefore be used with either tool. 12.2.7. ModularityThe benefit of MDB's modular architecture extends beyond the ability to load a module containing additional debugger commands. The MDB architecture defines clear interface boundaries between each of the layers shown in Figure 12.2. Macro files execute commands written in the MDB or adb language. Dcmds and walkers in debugger modules are written with the MDB Module API, and this forms the basis of an application binary interface that allows the debugger and its modules to evolve independently. Figure 12.2. Example of MDB Modularity
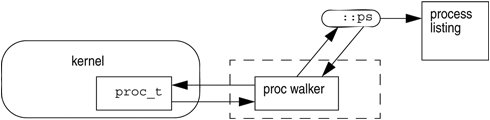
The MDB namespace of walkers and dcmds also defines a second set of layers between debugging code that maximizes code sharing and limits the amount of code that must be modified as the target program itself evolves. For example, imagine you want to determine the processes that were running when a kernel crash dump file was produced. One of the primary data structures in the Solaris kernel is the list of proc_t structures representing active processes in the system. To read this listing we use the ::ps dcmd, which must iterate over this list to produce its output.The procedure to iterate over the list is is encapsulated in the genunix module's proc walker. MDB provides both ::ps and ::ptree dcmds, but neither has any knowledge of how proc_t structures are accessed in the kernel. Instead, they invoke the proc walker programmatically and format the set of returned structures appropriately. If the data structure used for proc_t structures ever changed, MDB could provide a new proc walker and none of the dependent dcmds would need to change. You can also access the proc walker interactively with the ::walk dcmd to create novel commands as you work during a debugging session. In addition to facilitating layering and code sharing, the MDB Module API provides dcmds and walkers with a single stable interface for accessing various properties of the underlying target. The same API functions access information from user process or kernel targets, simplifying the task of developing new debugging facilities. In addition, a custom MDB module can perform debugging tasks in a variety of contexts. For example, you might want to develop an MDB module for a user program you are developing. Once you have done so, you can use this module when MDB examines a live process executing your program, a core dump of your program, or even a kernel crash dump taken on a system on which your program was executing. The Module API provides facilities for accessing the following target properties:
In addition, you can use built-in MDB dcmds to access information about target memory mappings, to load objects, to obtain register values, and to control the execution of user process targets. |
EAN: 2147483647
Pages: 180