Understanding Modern Encryption Techniques
Modern cryptosystems use advanced mathematical algorithms to encode data, rather than simple transposition or mechanical encryption. Because computers can perform complex calculation of large numbers almost instantaneously, cryptographers have been able to develop incredibly strong encryption.
Encryption performs, or enables, two vitally important functions on computer networks: authentication and securing data. Some networking systems implement encryption to authenticate data packets and ensure that they originated from an authorized host. Other systems, including Virtual Private Networks (VPNs), go a step further and encrypt the contents of each data packet to prevent unauthorized persons from reading it.
Regardless of the particular cryptosystem, most employ some form of symmetric (secret) key or asymmetric (public key) cryptography.
Failings of secret key cryptography
As I mentioned earlier, secret key encryption systems were plagued by a common problem: distributing the key to everyone who needed it without revealing it to adversaries. This is the sort of stuff spy movies are based on — agent X must get the codes through to agent Y, or all will be lost.
In reality, distribution of secret keys actually was, and sometimes still is, a huge problem for intelligence agencies and military forces. As more business and organizations began to conduct business electronically through telecommunications or computer networks, the problem became an even bigger issue.
If your business relies on information remaining secure or being authenticated, such as in financial transactions, then it needs to be encrypted. How then, do you get the proper key to every node on your network? If you simply transmit the key in-the-clear, anyone who has access to your network could intercept it and use it to decipher your transactions.
The answer is to encrypt the secret key and then transmit it. Of course, if you encrypt the key, then you need to transmit another key for deciphering the first, and so on. It seems like a paradox; you must encrypt a key to protect a key, but then that key must be encrypted to protect it, and so on. Another encryption technology, called public key cryptography solved this problem.
Understanding public key cryptography
Public Key Cryptography (PKC), also called asymmetric key cryptography, was invented by Martin Hellman, Whitfield Diffie, and Ralph Merkle in 1976. Public key cryptography solved some of the problems associated with secret key systems. Chief among these problems was key distribution. You can use PKC to encrypt a secret key and distribute it to the appropriate persons.
In a public key system, encryption and decryption require two different keys, a public key to encrypt the plaintext and a private key to decrypt it. A public key is just that, public. Everyone can know your public key, and it will not compromise your encrypted communication. Only you have access to your private key, as it can decrypt all messages encrypted with your public key.
For example using a public key cryptosystem, Alice wants to send Bob a secure message. Alice uses Bob’s public key to encrypt the message to Bob; she can then e-mail or transmit the ciphertext that will remain secure against prying eyes. When he receives the message, Bob uses his private key to decrypt the ciphertext into readable plaintext (see Figure 10-5).
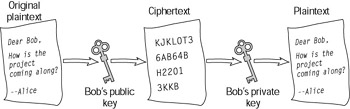
Figure 10-5: Using a public key system to encrypt and decrypt a message
Even though the whole world knows Bob’s public key, it can’t be used to decrypt his personal messages, only to encrypt them. It’s also extremely unlikely that anyone will be able to use his public key to determine his private key because of the extremely difficult mathematical process involved in creating each key.
| Note | Notice that I said it would be “extremely unlikely,” but not impossible to discover a private key from a known public key. It depends on the particular cryptosystem involved. You may read that it would take “every computer in the world a million years to defeat encryption system X.” Often, these claims are based on the sheer number of possible keys for a particular system. Advances in mathematics and computing power are making it possible to defeat more cryptosystems every year. Even systems that tout high-bit strength (128-bit, 1024-bit, and so on) have weaknesses unrelated to the size of the key. Ultimately, the security of any system is determined by its overall design and not by the strength of a particular key alone. |
One application that uses PKC to protect your e-mail is Pretty Good Privacy (PGP). At the end of this chapter, I briefly discuss PGP and where you can download it.
Examining hybrid systems
Many modern cryptosystems use a combination of secret and public key cryptography. Because they only use one key, secret key systems tend to be faster than public systems. Because of this, a combination of both secret and public cryptography is often used in different networking cryptosystems.
The problem of key distribution is solved by using a public key system to encode and distribute the secret key, which is then used to secure further communications (see Figure 10-6). This technique is sometimes referred to as a digital envelope. This is common in financial networks, including Automated Teller Machine (ATM) systems, and in secure E-commerce systems.
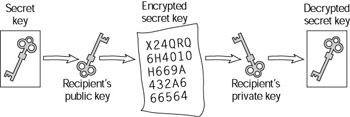
Figure 10-6: Key distribution with public key cryptography
Example applications of a hybrid system are digital signatures and digital certificates.
Digital signatures
Digital signatures provide proof that a message hasn’t been altered in transit and that it originated with the sender of the message. Digital signatures are produced with an encrypted one-way-hash of a message or binary file, combined with some application of public key cryptography (see Figure 10-7).
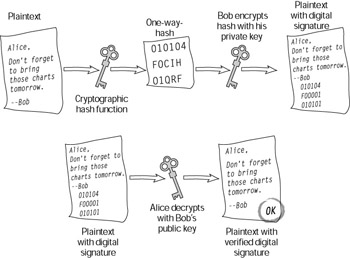
Figure 10-7: One method of using a digital signature
A one-way-hash function is an encryption technique that produces a sort of digital fingerprint, unique to the document (see Figure 10-8). It is one-way because you cannot derive the original message from the hash; you can only verify that the message is unaltered. Any change in the message changes the one-way-hash.
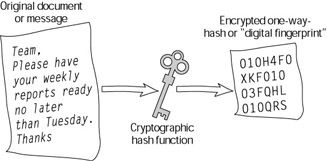
Figure 10-8: A one-way-hash of a message
While a digital signature proves that a message originated with a particular sender and that no one has altered it, it does not prove that the sender is who he says he is. If Alice receives a message with Bob’s digital signature, she only knows that it originated from someone claiming to be Bob, and that it remains unaltered. She has no way of knowing that Bob actually sent it.
Verifying the identity of a sender requires an application of cryptography called a digital certificate.
Digital certificates
A digital certificate provides third-party verification that a party to a transaction is indeed who the party claims to be. In short, a digital certificate is a sort of digitalI.D. card issued by a trusted third party called a certificate authority. One example of a certificate authority is VeriSign Corporation (www.verisign.com). VeriSign verifies the identity of an individual or organization and issues a digital certificate.
At one time or another, you have probably seen a warning about a digital certificate while surfing the Web (see Figure 10-9). These warnings indicate that your browser could not verify the identity of the Web site you are visiting. This is important, as crackers have set up fake Web sites that look like sites belonging to authentic companies, including Microsoft and Amazon.com. Usually these sites are identical to the legitimate site, but have a misspelled address (such as www.amzon.com). However, the crackers cannot forge the site’s digital certificate. If you see a warning that a certificate is not authentic, especially if it is a major site, avoid providing personal information or credit card data.
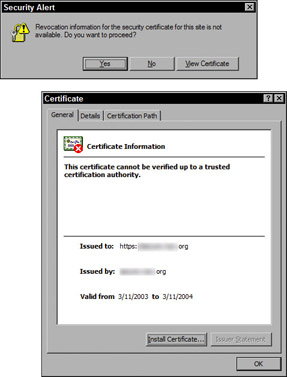
Figure 10-9: A digital certificate warning
Entropy and key strength
Advertisers like to stress key length when promoting the security of a particular cryptosystem. Usually this is expressed in bits, such as 128-bit or 64-bit encryption. Key length isn’t an indicator of security; overall design of a cryptosystem and the entropy in the key are more important than the length of the key.
In a cryptosystem, entropy is the amount of disorder or randomness present in a key or in the phrase used to generate a key. Entropy represents the number of possible patterns contained within random data. If a key has low entropy, there are fewer discernable patterns within it, and that increases the likelihood that a pattern will be identified and the key discovered (this is oversimplified, but sufficient for your purposes).
Entropy is an important concept, one worth remembering. If you place all of your faith in an “unbeatable” 128-bit encryption system, then use an eight-character password to generate a 128-bit key, you’ve just undermined your security. Systems that use short passwords or pass phrases to generate keys typically do not create enough entropy in the key to make it very secure.
Cryptosystems use different methods to generate entropy in keys. Because it’s impossible for a computer to create truly random numbers, researchers have devised ingenious ways of accomplishing this. Some methods sample environmental data (noise, temperature), while others collect random input from users (time between keystrokes, or mouse clicks).
When generating keys for your cryptosystem, always use long, nonsensical phrases or passwords to ensure that the keys you generate will contain sufficient entropy to remain secure.
EAN: 2147483647
Pages: 145