Discovering Common Wi-Fi Problems
Discovering Common Wi-Fi Problems
Many of the more common problems in WLANs are the result of interference or configuration errors. Included in this group are:
-
Multipath signal propagation
-
Channel overlapping
-
RF interference
Explaining multipath interference problems
Multipath interference or multipath signal propagation occurs when a signal reflects off objects in its environment, causing it to arrive at a receiving antenna from more than one direction at varying times and strengths (see Figure 8-1). The multiple signals can confuse the receiving device and cause interference.
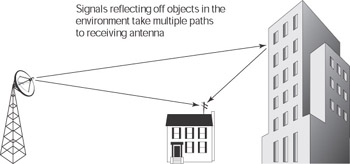
Figure 8-1: Multipath signal propagation
The interference is due, in part, to interaction of the arriving radio waves. When identical waveforms arrive at the receiver at slightly different times they can cancel each other out, which creates interference and results in lost signals (see Figure 8-2).

Figure 8-2: Multipath waveforms combining
If your TV receives its signal through anan antenna, rather than cable or a digital satellite service, you may occasionally see ghost or doubled images. This is a visual example of multipath interference (see Figure 8-3). The television signal reflects off objects in the environment, and as a result, the signal takes multiple routes to the TV receiver. Signals arriving at slightly different times result in the ghost images.

Figure 8-3: Example of a ghost image
Engineers can count the scan lines on a television image and based on the offset of the ghost image, can determine the distance to the objects creating the multipath interference.
In a WLAN environment, many objects may contribute to multipath propagation. These objects include (see Figure 8-4):
-
Solid, load-bearing walls, ceilings, and floors
-
Metal furniture and cabinets
-
Construction materials
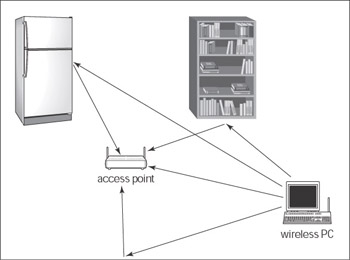
Figure 8.4: Objects causing multipath propagation in the QWLAN environment
If you suspect you are having problems with multipath interference, one way to deal with it is to use a diversity antenna system. A diversity antenna system uses dual antennas that enable the access point or adapter to get cleaner reception and avoid multipath problems.
When using a diversity antenna system, an access point doesn’t simply select the antenna with the strongest signal (an often-repeated misconception). In most Wi-Fi diversity antenna systems the antennas are mounted a few inches apart, often on either side of the access point (see Figure 8-5). The signal strength difference between the individual antennas is likely to be negligible.
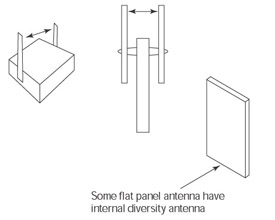
Figure 8-5: A diversity antenna system
The transceiver inside newer access points or adapters can compare and discern the difference between the signals received from either antenna. By using sophisticated technological techniques, it can filter the multipath interference and eliminate the problem.
Newer Wi-Fi standards are less susceptible to multipath problems than 802.11b systems are. The reason is that 802.11a and 802.11g use a broadcast technology called Orthogonal Frequency Division Multiplexing (OFDM), which is less susceptible to multipath problems. 802.11b uses Direct Sequence Spread Spectrum (DSSS) technology, which transmits data in a wider spectrum than OFDM. Portions of a DSSS signal reflect off objects differently, allowing for more chances for multipath propagation.
Another way to identify and prevent multipath and other WLAN issues is to conduct a site survey. A site survey is an in-depth study of the environment in which your WLAN will be operating. Its purpose is to identify potential problems and plan around them.
Theft of service may not always be intentional. Other wireless users may inadvertently connect to your network without even realizing they have done so. In areas where neighbors are physically close, such as apartment buildings, it’s becoming common for people to accidentally connect to another’s network, especially if they are using default settings on their equipment. In addition, Windows XP automatically identifies and attempts to connect to access points, which makes inadvertent connections more likely.
As an example, a friend of mine was having trouble setting up his WLAN. He didn’t realize that his neighbor also had a WLAN and was using an access point from the same manufacturer. In addition to this, they were both using the default SSID (Linksys) and the default network settings.
The signal from his neighbor’s WLAN was stronger, and his client adapter automatically connected to it. For months, he was using his neighbor’s broadband connection without even realizing it. This went on undiscovered until the neighbor went on vacation and turned off his gear. Suddenly, my friend lost his Internet connection.
Until that point, he had no idea that he was using someone else’s network and Internet connection. Technically this was theft of service, but it certainly wasn’t intentional.
If you’ve taken the steps to make your network reasonably secure, you probably won’t have to worry about theft of service.
A full-blown site survey probably isn’t necessary for a WLAN that’s going to be located in a home or small office, but you should still take the time to plan the layout of your network in advance so that you can minimize problems that you may encounter when you install your network.
Adjacent channels overlapping
802.11b and 802.11g equipment broadcast data using one of 11 different channels within the 2.4 GHz frequency band. 802.11a uses eight channels (see Figure 8-6). As the figure illustrates, the frequency band of each channel overlaps. In other words, each channel shares some of its frequency band with adjacent channels.
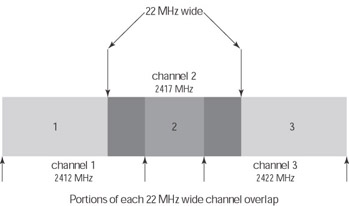
Figure 8-6: Wi-Fi channels
Because of this overlap between adjacent channels, you should only use channels 1, 6, or 11 for your equipment in order to avoid problems with nearby WLANs. Most manufacturers set their access points to one of these channels by default. Because of this, these are also the channels that your neighbors are most likely to use. If you run into interference from another network try choosing a different channel to minimize interference problems.
Identifying theft of service
One problem with wireless networking is that anyone can receive your signal, not just the people you authorize. It’s possible that neighbors or passersby could connect to your WLAN and use your Internet connection without your consent. The result could be slower Internet access for you as other people use more of your bandwidth. In some cases, you may find yourself in hot water with your ISP.
Because wireless networking has made sharing a single Internet connection — and bill — even easier, some ISPs are lobbying congress and the FCC to prevent their customers from sharing bandwidth with other users. This is partly in reaction to customers setting up hotspots and sharing service with their neighbors.
In many cases, your agreement with your ISP will specifically prohibit you from sharing service with others. Violation of the agreement constitutes theft of service, and you could lose your service or have your bandwidth reduced. It may not matter that you didn’t intentionally share the connection; your ISP may decide to take action anyway.
| Note | If your Internet connection is co-opted by the neighbors, your neighbors may be breaking the law in many states by doing so. Most states have computer crime statutes that prohibit theft of service (in many cases a misdemeanor), and existing precedents support the inclusion of theft of Wi-Fi service under these laws. |
Theft of service is hard to identify because an unauthorized user can connect without you ever realizing it. Unless your network traffic shows a dramatic increase, you may never notice that it was occurring.
One way that you can identify unauthorized connections, both inadvertent and intentional, is by using a network port scanner (see Figure 8-7). A port scanner is a software tool that you can use to scan your network and identify clients by IP address. For example, if you have three computers on your network and the port scanner identifies a fourth IP address with hosts connected, then you may have someone else connected to your WLAN.
Figure 8-7: The Windows version of the NMAP port scanner
There are many port scanners available for download on the Internet. Using a port scanner takes a certain amount of network knowledge and skill, so if you decide to experiment, take the time to read all documentation and familiarize yourself with all of the available options. Don’t worry about damaging your network. A port scanner generates network traffic, essentially knocking on doors and waiting for an answer. You won’t harm anything, but your firewall may generate alerts due to the activity.
| On The Web | NMAP, a good port scanner, is available for download at www.insecure.org. |
| Cross-Reference | Read more about securing you network in Chapter 11. |
Uncovering configuration errors
Occasionally, you may inadvertently make a mistake when setting up your WLAN hardware. Most often, configuration errors will keep your devices from operating at all, but it is possible that the source of your network problems could be something as simple as selecting the wrong channel on your access point.
Recently, a friend was having trouble with her home WLAN. Her access point would intermittently become unreachable through its Web interface. Everything appeared to be in order; all the clients were communicating with no problems. Eventually, the problem was traced to the way she was sharing her Internet connection.
She was using Windows XP Internet Connection Sharing (ICS), which has a built-in DHCP server. The XP version of ICS doesn’t allow you to configure or disable the DHCP component. She had assigned a fixed address to her access point, and although it could communicate with the clients, every time the ICS computer rebooted, it became unreachable through the Web interface. In this case, the solution was to disable ICS and connect her access point directly to her broadband modem.
If you are experiencing problems, check all of your settings before you jump to conclusions and assume that you’re having interference problems. Some places you may find configuration errors are:
-
Incorrect antenna installation
-
Incorrect SSID
-
Using the wrong channel
-
Adapters in ad hoc rather than infrastructure mode
-
Adapter set for the wrong network
-
IP address conflicts
-
Connection speed set too high
Make sure that directional antennas are facing in the correct direction and that the antenna cables you are using aren’t excessively long. Long cables can weaken the signal before it even reaches the antenna.
If you choose to assign manual IP addresses instead of using DHCP, make sure that you don’t accidentally assign the same IP address to two different devices. Also, check the SSID for typos and to ensure that your adapters are set to connect to your network.
Excess clients may also cause performance problems on your WLAN. While some equipment advertised for home and small-office use may claim to handle up to 100 clients, in practice this claim is ridiculous. I have seen consumer access points slow to a crawl with less than 10 clients connected, especially if there is heavy network traffic. On my own network, throughput drops significantly when four or more computers are in use or when my kids are gaming over the network.
If you are going to have several clients that will be using the network heavily, I suggest investing in more than one access point. In any case, it will likely improve coverage, as well as performance.
EAN: 2147483647
Pages: 145