ANNOYING AND DECEPTIVE SOFTWARE: SPYWARE, ADWARE, AND SPAM
| | ||
| | ||
| | ||
Most users are familiar with software that behaves (mostly) transparently and according to expectations. Anyone who's read this chapter is also familiar with software that undeniably performs activities that no sane user would authorize (and if you haven't gotten your fill yet, wait ˜til our upcoming discussion of malware). Somewhere between these two extremes sits a category that we call annoying and deceptive software . Annoying and deceptive software is composed of programs that may perform some activities with the consent of the user, and others that do not. Annoying and deceptive software includes spyware, adware, and spam (although not all adware is deceptive). The key differentiator between annoying and deceptive software and the outright malicious is intent. Annoying and deceptive software is not out to compromise your system just for the sake of itunauthorized access is simply a means to an end (usually economically motivated, such as selling online advertisements).
Briefly, spyware is designed to surreptitiously monitor user behavior, usually for the purposes of logging and reporting that behavior to online tracking companies, which in turn sell this information to advertisers or online service providers. Corporations, private investigators , law enforcement, intelligence agencies, suspicious spouses, and so on have also been known to use spyware for their own purposes, both legitimate and not. A key example of the former type of spyware is the Gator Advertising Information Network (GAIN), a network of advertisers who deliver ads through Gator's adware agent (although we have to say that GAIN is getting much better about asking users' consent before installing their software nowadays). Adware is broadly defined as software that inserts unwanted advertisements into your everyday computing activities. The best example of adware is those annoying pop-up ads that can overwhelm you browser when you visit a site with abusive advertising practices. Last but not least, spam is unsolicited commercial e-mail (also called UCE). Unless you've been living off the grid for the last decade , you know exactly what spam is and how annoying it can be.
Numerous resources are available on the Internet that catalog and describe annoying and malicious software. Some of our favorites include:
-
http://www.junkbusters.com
-
http://www.spywareinfo.com
-
http://www.spywareguide.com
-
http://www. pestpatrol .com/pestinfo
-
http://ww.microsoft.com/spyware
The rest of our discussion will cover common spyware, adware, and spam insertion techniques, and how to rid yourself of these pests.
Common Insertion Techniques
Spyware and adware typically insert themselves via one or more of the following techniques:
-
By installing an executable file to disk and referencing it via an autostart extensibility point (ASEP)
-
By installing add-ons to web browser software
Spam, of course, inserts itself into your e-mail inbox, so we won't talk much about that in this section (we'll spend more time discussing how to deflect spam in the next section). Let's take a look at each of these techniques in more detail.
Autostart Extensibility Points
We've already referenced autostart extensibility points (ASEPs) in our discussion of Internet client hacking history. The importance of ASEPs in the proliferation of annoying, deceptive, and even downright malicious software cannot be underestimatedin our opinion, ASEPs account for 99 percent of the hiding places used by these miscreants. A good list of ASEPs can be found at http://www.pestpatrol.com/PestInfo/AutoStartingPests.asp. You can also examine your own system's ASEPs using the msconfig tool on Windows XP (click the Start button, select Run, and enter "msconfig."). Figure 13-12 shows the msconfig tool enumerating startup items on a typical Windows XP system.
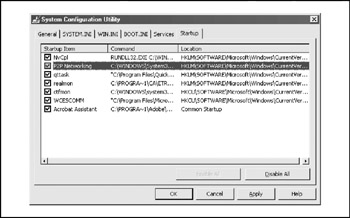
Figure 13-12: The msconfig utility enumerates autostart extensibility points on Windows XP. Note the peer-to-peer networking software program highlighted here.
ASEPs are numerous, and they are generally more complex than the average user wishes to confront ( especially considering that uninformed manipulation of ASEPs can result in system instability), so we don't recommend messing with them yourself unless you really know what you are doing. Use an automated tool such as the ones we will recommend shortly.
Web Browser Add-Ons
Right up there with ASEPs in popularity are web browser add-ons, a mostly invisible mechanism for inserting annoying or deceptive functionality into you web browsing experience. One of the most insidious browser add-on mechanisms is the Internet Explorer Browser Helper Object (BHO) feature (see http://msdn.microsoft.com/library/en-us/dnwebgen/html/bho.asp for technical information on BHOs, and see http://www.spywareinfo.com/articles/bho for a shorter explanation). Up until Windows XP SP2, BHOs were practically invisible to users, and they could perform just about any action feasible with IE. Talk about taking a good extensibility idea too farBHOs remind us of Frankenstein's monster. Fortunately, in XP SP2, the Add-On Manager feature (under Tools Manage add-ons) now will at least enumerate and control BHOs running within IE. You'll still have to manually decide whether to disable them, which can be a confusing task because some deceptive software provides little information with which to make this decision within the IE user interface. Alternatively, you can use one of the third-party tools we recommend in our upcoming section about blocking, detecting, and cleaning such miscreants.
Blocking, Detecting, and Cleaning Annoying and Deceptive Software
Why does annoying and deceptive software persist? For the oldest reason on the books: It makes money. Thanks to the growth of the Internet, the economics of even something as annoying and routinely discarded as spam become attractive. Consider this: An International Data Corp. (IDC) study in May of 2004 estimated that average daily volume of spam sent worldwide will jump from 4 billion in 2001 to 17 billion in 2004. If just 0.1 percent (one tenth of one percent) of these messages result in an actual transaction, that's between 4 and 17 million transactionsper day! And a study by Yahoo!, Inc., indicated that at least in the U.S., the response rates for spam actually approach closer to 20 percent. The economics of the Internet advertising market are similarly predicated on tracking the behavior of and targeting advertisements to the largest possible number of online consumers. So, regardless of whether you agree with the means by which these ends are achieved, annoying and deceptive software isn't going to go away soon.
In light of the information we just discussed, one of the best mechanisms for fighting annoying and deceptive software is at the economic level. Don't respond to spam or agree to install adware or spyware on your system in exchange for some cool new software gadget (such as peer-to-peer file sharing utilities). Yes, this requires fighting your own internal economic instincts that drive you to use a "free" ad-supported product rather than paying a flat fee or subscription for an advertising-free version, but, hey, mass culture adopted cable television and TiVo pretty readily, so we have faith that the hidden costs of advertisement will prove to be the economic loser in the long term .
The TiVo concept brings up technological solutions for filtering deceptive and annoying software. Numerous antispam programs are available today that will filter unwanted mail from your inbox (see http://www.spamfilterreview.com for a comparison, or just grab the top-rated one from download.com). Most are designed around blacklist or whitelist approaches. Blacklists are updated lists of known spam messages (based on sender, subject, and so on) that filter each message coming in. Whitelist approaches take the opposite tack, in which the user provides an "approved" list of senders or other criteria and the spam filter simply blocks everything else. Each has pluses and minuses, depending on your e-mail usage behavior. If you receive a lot of mail from diverse senders that may or may not be know to you, obviously the blacklist approach is superior .
Spam can also be filtered at the mail server, before it even reaches the e-mail client software. Almost every corporation or e-mail service provider of substance today offers some form of spam filtering. The techniques are also based on whitelists and blacklists, and new infrastructure-wide solutions such as Sender ID (see http://www.microsoft.com/senderid) are being proposed currently as well. One of the server-side filtering products we've heard good things about is Symantec's Brightmail.
For dealing with adware and spyware, Germany hosts the top two contenders: Spybot Search & Destroy, from http://www.safer-networking.org (formerly security.kolla .de), and Ad-aware from Lavasoft, at http://www.lavasoft.de. In informal testing, we give the clear edge to Spybot because it's free and found far and away more items than the free Ad-aware Personal version on our test system. We also like the "Immunize" and "Recovery" features offered by Spybot, as well as the ability to get updates via the Internet integrated within the tool. Spybot is shown scanning a system in Figure 13-13. Other top contenders include CA's Pest Patrol and Webroot's SpySweeper.
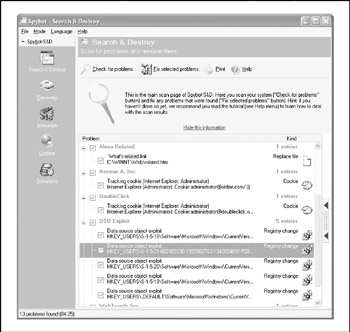
Figure 13-13: Spybot Search & Destroy finds adware and spyware on a system.
| Tip | If you want to get an idea of how infected your system is, try running the free scan at http://pestscan.com, which is hosted by Computer Associates, makers of the Pest Patrol antispyware program. |
In early 2005, Microsoft made a splash by formally confirming its long-anticipated entry into the antispyware market with the purchase of technology from GIANT Company Software. Microsoft proceeded to quickly release a beta version of the newly acquired technology on its site at http://www.microsoft.com/athome/security/spyware/software/default.mspx.
By most accounts (including our own informal testing), Microsoft's tool is a substantive entry into the market. The most glaring omission is its inability to identify cookies that might reveal inappropriate user information, which is somewhat minor in our opinion (see our earlier discussion of cookies in this chapter, where we noted that numerous tools for managing such cookies exist). Areas where Microsoft seems to be leading include real-time monitoring/protection, automatic signature downloads, and a global community inherited from GIANT called SpyNet (http://www.spynet.com) that will potentially continue to help identify new spyware threats as they arise. Microsoft's AntiSpyware Beta 1 is show in Figure 13-14.
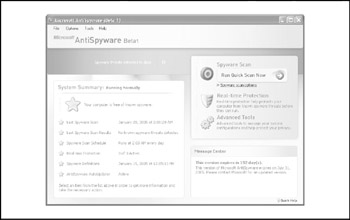
Figure 13-14: Microsoft's AntiSpyware beta, illustrating some of its best features, such as real-time monitoring/protection and automatic signature downloads
| Tip | Try running antispyware tools while running in Windows Safe Mode, which can reveal infections overlooked while running in standard mode. |
| Tip | For more detailed comparisons of the top antispyware tools, see http://spywarewarrior.com. |
For the time being, and especially as long as antispyware tools remain relatively inexpensive, it is probably a good idea to run at least two antispyware tools until the industry begins to consolidate around a more comprehensive list of what constitutes spyware and begins to integrate with traditional malware prevention/detection tools such as antivirus.
Beyond the automated hardening offered by antispyware tools, more advanced users may consider making additional, manual configuration changes to their systemfor example, configuring your hosts file to block ad servers and then making the hosts file read-only (see http://www.sc.rr.com/rrhelp/spyware.htm).
EAN: N/A
Pages: 127