Assessing Your Vulnerability
| It is a common mistake for people to assume that switching on a firewall makes them safe. Although there's no question that switching on a firewall is an important step to take, it is not a solution and never has been. Each system has distinct security needs, and taking the time to customize its security layout will give you maximum protection and best performance. Following are the most common security mistakes people make:
After you have ruled out these common problems, you're on to the real problem. How can the bad guys attack your machine? What can people access from the outside? This comes down to the question of what applications and services face the Internet, and what ports do they run on? The best way to find answers to these questions is through the Nmap networking utility. This little tool will scan the ports of any machine on your network, or all of them, and tell you which ones are open at that moment. Any service you have installed that responds to Nmap's query is pointed out, and you may, in turn, choose to lock down ports that should not be open. SUSE Linux does not install Nmap by default, but you can install the command-line version and a GUI front-end called Nmap-gtk through YaST. Other GUIs are available at the Nmap website, http://www.insecure.org/nmap. Although you can use the shell version, it is much easier to configure and see the results of Nmap's work in the GUI (Figure 23.1). It is also better to run Nmap as the SuperUser, because you will get more information that way. To launch Nmap-gtk, log in as the SuperUser and type xnmap &. Figure 23.1. Nmap scans ports to see what is open and vulnerable.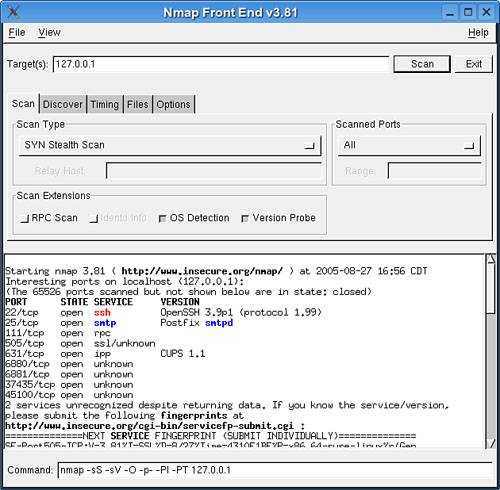 The best way to run Nmap, especially the first time, is to use the SYN Stealth scan (on by default when you launch it as SuperUser) with OS Detection and Version Probe on. By default, Nmap scans the localhost (127.0.0.1), but you can add or change targets by typing the IP address(es) into the Target(s) edit box. The first time you run Nmap, you should click the Scanned Ports box to change the scan range from a few default ports; select All from the drop-down menu. This scan takes a little longer, but gives you a more complete picture of your status. As you adjust your options in the GUI, you'll see the actual shell command being built at the bottom of the window. You could, if so inclined, copy this command to a text file and run it as a shell script later on. When you have made your selections, click Scan. Nmap tests each port to determine whether it responds. If it does, Nmap asks the application at that port for version information and displays that to the Nmap screen. You then get results like those displayed in Figure 23.1. Ideally, there will be no surprises on the list. If there are surprises, or you decide that there are some unnecessary services on the list, you can take action. You can log your Nmap scan by going to Save Log in the File menu and choosing a location from the menu. To view the log file later, go to Open Log from the File menu. If you just have one or a few machines on the network, you probably need to run Nmap only once a year, or if you suspect your system is compromised. Sysadmins of larger networks should run Nmap regularly as part of their general maintenance regimen. Caution Peer-to-peer file sharing networks such as Gnutella and BitTorrent usually require you to open ports on your firewall to speed up, or even access, the network. Recognize that you may be compromising your security when you participate in these networks. Be wary when downloading files from these sources. although as of this writing, no significant worm has propagated itself through peer-to-peer networks, it could easily happen. Not every file with a certain name contains the content you may be expecting after you get it downloaded. |
EAN: 2147483647
Pages: 332