6.6 Addressing Strategies
6.6 Addressing Strategies
During the requirements analysis process, you must gather information about device growth expectations so that you can avoid having to change addressing schemes and reconfiguring device addresses during the life cycle of the network.
When applying subnetting, variable-length subnetting, classful addressing, supernetting, private addressing and NAT, and dynamic addressing, we want to make sure that our network addresses and masks will scale to the sizes of the areas to which they will be assigned. We also want to establish the degrees of hierarchy in the network. To scale the network addressing, we will use the numbers of:
-
FAs within the network
-
WGs within each FA
-
Subnets within each WG
-
All the subnets (current and future) in the organization
-
All the devices (current and future) within each subnet
By establishing the scaling and hierarchies for our network, we are applying addressing, not only system-wide but also across FAs, WGs, and subnets. The intent here is to look at addressing from many perspectives so that we do not lose the detail of any particular area and do not fail to see the overall addressing picture. While each of the addressing strategies could be applied to any area of the network, there are areas where each strategy is more appropriate. Figure 6.20 shows where each strategy applies.
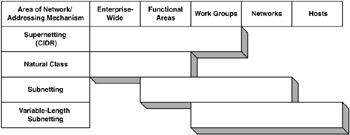
Figure 6.20: Applying various addressing strategies.
At the bottom of the hierarchy, where devices and subnets are addressed, variable-length subnetting can provide the flexibility needed to map addresses to various network/device sizes. In the middle of the hierarchy, where there are FAs and WGs, subnetting is often sufficient. At the top end of the hierarchy, where the entire network resides (as well as most external interfaces), using the natural mask for the network address or applying subnetting is usually appropriate. The hierarchies of variable-length subnetting, both internal and external to the network, are shown in Figure 6.21.
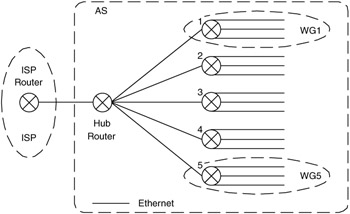
Figure 6.21: Example for variable-length subnetting.
In Figure 6.21, a hub router connects a number of WG routers to an ISP. This hub router can interconnect up to 10 networks but is currently connected to 5 networks. Each WG router should be configured to support four networks, with each network having 10 to 20 devices attached to it. We have been assigned the CIDR block 192.92.240.0/20, which we are expected to summarize to the ISP router.
We can break this network into addressing areas, based on the numbers of FAs, WG, networks, and devices. This will help us choose address mask sizes that are appropriate for the scale of our network.
In this example there are three distinct areas to address. First, the WGs have four networks, with 10 to 20 devices per network. For this area, we could assign from the CIDR block a Class C per WG, subnetted with a mask of 255.255.255.224 (or /27), which will support up to six subnets with up to 30 devices per subnet. The next area is where the WG routers connect to the hub router. If addresses need to be assigned (if the routers do not support unnumbered links), we could subnet a single Class C from the CIDR block with a mask of 255.255.255.252 (or /30), supporting 63 subnets with two devices per subnet.
These connections are point-to-point between each WG router and the hub router, so we will need to address only two devices per connection. The third area is the connection between the hub router and the ISP router. Here, we will provide the summary advertisement 192.92.240.0/20. The result is shown in Figure 6.22.
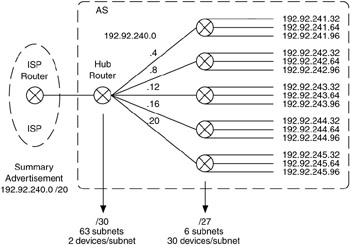
Figure 6.22: Example with variable-length subnetting applied.
EAN: 2147483647
Pages: 161