Unicast Versus Multicast Routing
| IP routing is needed to direct units of data known as packets through a network. In a packet-based network, a large file is broken down into packets before it is transmitted from one end of the network to the other. Routing is required in network environments where multiple segments are patched together over a large area. The segments, which can potentially be different transport media, are linked by routers. No routing is required when nodes are connected to the same network segment, such as a LAN or a point-to-point link. The following two kinds of routing are distinguishable by their different approaches to packet forwarding:
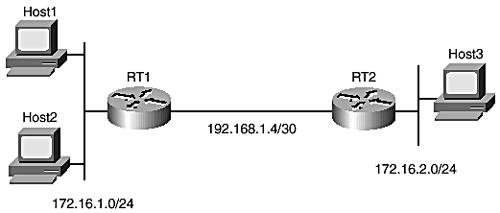
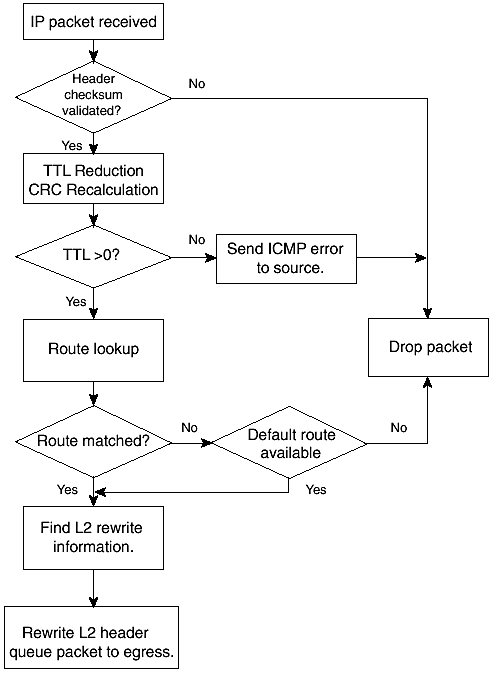
In unicast routing, packets are forwarded toward the single-host addresses in their destination fields. In multicast routing, however, the address in a packet's destination field is a multicast group address. This allows a single packet to be forwarded to multiple receivers in the multicast group , effectively forwarding the same data once to multiple hosts . The discussion so far in this chapter is biased toward unicast protocols because the objective is to provide background material for IS-IS, which is a unicast routing protocol. IP unicast forwarding is designed on a destination-based "forward-to-next- hop" paradigm. This means that each router in the path looks at the destination in a packet and forwards it to the next hop along the best known path the destination. Except in the case of special policy-based forwarding schemes, the source address of a packet is irrelevant in forwarding and exists for the two-way handshake between the origin and destination communication where necessary. In contrast, multicast forwarding inherently depends on both the source and destination addresses. A method known as reverse path forwarding ( RPF ) is used to check the multicast routing table, for the best path to the source address of a packet through the interface on which the packet was received, before the packet is accepted. The destination address in the multicast packet is a multicast group address. Each multicast group has an associated outgoing interface list (OIF) that determines the location of receivers that have joined the group. After the RPF check is done on the source, copies of the packet are forwarded to the interfaces in the OIF list associated with the group address in the packet. Examples of multicast protocols are Distance-Vector Routing Protocol (DVMRP), Protocol-Independent Multicasting (PIM), Multicast OSPF (MOSPF), and Multicast Source Discovery Protocol. Multicast routing is not further discussed in this section; for more information on multicast routing, read Developing IP Multicast Networks , Volume I (Cisco Press, 2000. ISBN: 1-57870-077-9). A recently introduced Cisco IOS security feature known as Unicast Reverse Path Forwarding (Unicast RPF) uses the concept of reverse path checking for controlling unicast forwarding in a manner that successfully addresses Internet Denial of Service (DoS) attacks based on source address spoofing. Unicast RoutingAs mentioned previously, the essence of IP unicast routing is to help routers figure out the next hop to pass on packets, along the best path to a target destination. Choice of the best path is determined by choosing the path with the lowest cost. This best path determination boils down to determination of the data-link or MAC address of the next hop. Each non-directly connected entry in the routing table consists of a prefix, the IP address of the next hop, and the outgoing interface to the next hop. Actual forwarding may involve extra steps to determine the corresponding data-link address of the next hop from the ARP table or an equivalent address map table for the specific media. If the destination is directly connected, the address resolution retrieves the data-link address of the destination; otherwise , the data-link address of the router at the next hop is obtained. During forwarding, the original destination IP address of the packet does not change, but the data-link address keeps changing as the packet traverses different links until it arrives at its destination. The data-link information that a router appends to a packet before sending it off to the next hop is referred to as the Layer 2 rewrite string (or as just the MAC rewrite in the case of LANs). IP Unicast Forwarding ExampleFigure 1-8 shows a simple IP network that consists of three network segments. Each segment is assigned a unique IP subnet. To get to destinations on the segment or same subnet, the ARP protocol is used to resolve the data-link address associated with the destination IP address. To get to a remote segment, however, routing is required. If Host1 needs to forward data to Host2, for example, it relies on ARP to obtain the corresponding MAC address of Host2. If Host1 needs to send data to Host3, which is on another segment, however, it forwards the data first to RT1, which then forwards the data on to RT2, which finally delivers the packets to Host3. Figure 1-8. Illustration of IP forwarding. In summary, routing works by finding the corresponding Layer 2 rewrite of the next hop to the destination address in the packet. The IP packet is then encapsulated in a data-link frame with the Layer 2 rewrite and forwarded on to the next hop. The next hop can be the ultimate destination of the packet or a router on the path toward the destination. Figure 1-9 shows a flowchart of IP packet-forwarding process. Figure 1-9. IP packet-routing process. Determination of the Layer 2 rewrite string is one of the most important steps in packet forwarding. Other activities related to forwarding include validation of the IP header checksum and reduction of the IP TTL value. IP packet processing also might involve policy enforcement, such as packet filtering, traffic rate limiting, congestion control, latency control through various quality-of-service queuing schemes, and setting of the type of service bits in the IP header. All of this additional packet processing takes time and processing resources, requiring the assistance of various packet-switching optimization schemes in high-speed routers to achieve line-rate forwarding at 10 gigabits per second and beyond. Cisco routers have evolved through various packet-switching mechanisms: Process, Fast, and Cisco Express Forwarding. These switching methods are briefly covered in the section "Cisco Packet-Switching Mechanisms." Longest Match RoutingIn many cases, before a router selects the best path to a destination, it might run into several similar routes that differ only in their prefix length. Recall from the previous discussion that in today's world of classless routing, routes are no longer differentiated by their classes but by their prefix length, as determined by the subnet masks. For example, the address 192.168.1.1 can match both 192.168.0.0/16 and 192.168.1.0/24 if they are both in the routing table. However, one important rule for matching routes, longest match routing, dictates that the matching route with the longest prefix length, 192.168.1.0/24, should be preferred over the less-specific entry, 192.168.0.0/16. This makes sense because the less-specific route is normally a summary route that might have lost specific details during aggregation. Therefore, the more specific entry must be preferred. This basic lookup rule is critical for a router to support VLSMs. |
EAN: 2147483647
Pages: 144