Типы осветительной аппаратуры
, , , , . , , , , , . , , . , , .
, , , , . , , . . - .
, . , , , , , - ( . 4.5). , , , - ( . 4.6) . ,
-

. 4.5. . , .
. - .
, , , , ( . 4.7, ). , . 2,5 5 , , 1250 . . ,
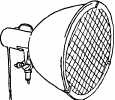
.4.6
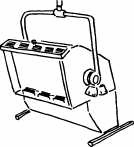

. 4.7. ( ); ( ).
- , , , .
- , . 10 , 10 .
( ), , . , . 6 2 36 ( . 4.7, ).
, , , .
- 0' . , , , , . .