4.1 The Router on the Network
| Older network designs sometimes made extensive use of routers. To keep broadcast traffic under control routers were sometimes used to create network segments ”although bridges were more commonly used for this purpose ”and to help distribute traffic load. Newer network designs replace the routers with multilayer switches. [1] A network built around multilayer switching technology allows you to keep your network design more streamlined, and means that you only have a single router, or pair of routers, to worry about.
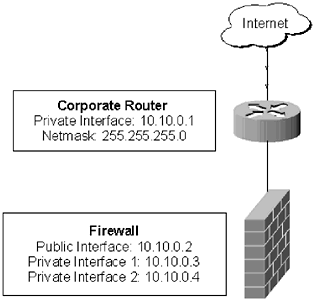
Figure 4.1 shows a typical edge network design. Figure 4.1. Typical edge network design There are several problems with this design, the most glaring of which is that it provides an attacker with a single target. Whenever possible, a network should have multiple connections to the Internet. In addition to improving WAN response to and from the network, a dual- homed connection is a lot less susceptible to a DoS attack. Of course a dual-homed design does involve some additional risk, as it requires the enabling of an Exterior Gateway Protocol (EGP), such as BGP. You will also have to enable the Virtual Router Redundancy Protocol (VRRP) [2] so the routers can share a connection internally. A new, more robust design will look more the one in Figure 4.2.
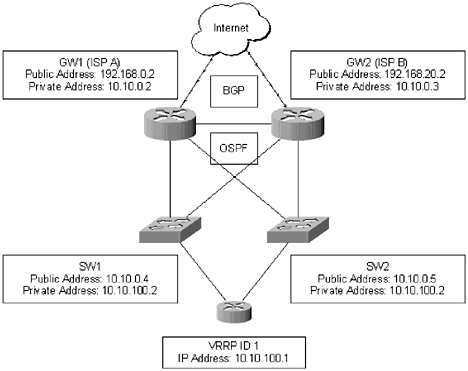
Figure 4.2. A new network design In addition to running BGP on the external network, the new design uses OSPF on the internal network. Depending on what type of switches used behind the routers, the VRRP address may be configured on a second pair of routers, instead of multilayer switches. Notice the two routers are connected to different ISPs. It is not enough to have two connections to the same ISP; a network should be as diverse as possible ”given the limitations of ythe budget. Enabling these enhanced services will be discussed in detail later in this chapter. |
EAN: 2147483647
Pages: 131