Configuring Basic IP Dialup Services
| Up to this point, we have been examining the IOS software's routing protocol and IP packet-switching capabilities. The IOS software also enables remote access in the routers and access servers. The remote access capability is available as both asynchronous dialup via external and integrated modem modules, and via ISDN. Remote access provides both remote users and remote routers with the capability to connect to IP network services when they are not connected directly to a network via a LAN or WAN interface. Numerous IOS-based products support IP remote access services. These products offer many configuration options in both their hardware and IOS software feature configurations. As with other complex topics discussed in this chapter, entire books are devoted to the discussion of remote access services. We have chosen to present two of the common configurations for basic IP remote access that support dialup workstation users. Many of these commands and the configuration concepts are also applicable to the implementation of router-to-router remote access, which is known as dial-on-demand routing. For a discussion of the issues and the configuration of dial-on-demand routing, we recommend referring to the following Cisco Systems case studies. You can find Dial-on-Demand Routing and Scaling Dial-on-Demand Routing on CCO at http://www.cisco. com/univercd/cc/td/doc/cisintwk/ics/cs002.htm and http://www.cisco. com/univercd/cc/td/doc/cisintwk/ics/cs012.htm, respectively. To ensure the reliability of the connection over a dialup service, such as a modem or ISDN, IP is transported on a link layer protocol over the dialup service. Several data link layer protocols are supported on dialup services, including PPP, HDLC, SLIP (Serial Line IP), and Frame Relay. At the time of this writing, PPP is the predominant choice as a data link layer protocol for dialup service. Configuration of remote access services can be broken down into three major areas:
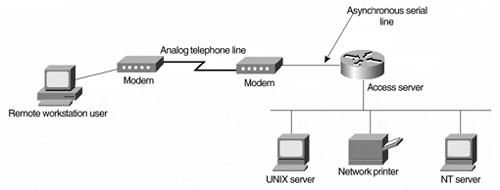
Each of these is examined for both asynchronous and ISDN dialup scenarios on the ZIP network access servers located in Singapore . The asynchronous services are provided on a Cisco 2511 that supports 16 async lines. The ISDN services are provided on a Cisco 4500 with integrated ISDN BRI interfaces. Configuring Asynchronous DialupAsychronous dialup (async for short) involves the use of analog modems to convert data into streams of information that can be carried over phone lines. These modems may be either integrated into the product, as with the Cisco AS5200 AccessServer and 3600 router, or attached externally, as with the 2511 AccessServer and the auxiliary port of most Cisco routers. Figure 4-9 shows a typical dialup scenario for a remote workstation user accessing a network via an access server with external modems. Figure 4-9. Remote Dialup Access to an Access Server Via Modems Regardless of whether there are physical async serial lines attached to the modems or virtual lines inside the integrated modem modules, the lines and modems must be configured properly to ensure proper communication. The speed of the line, the flow control method, the direction of the dialup, and the type of modem attached are some of the most important aspects that must be set up. Chapter 7 discusses the configuration of virtual terminal lines (vty) for the purposes of controlling remote access to the router via the IOS major configuration command line. We also use line commands to configure characteristics of the physical async lines (tty) used for connecting the modems. To set the speed at which the access server communicates with the modems, use the IOS line configuration subcommand speed . The command takes as a parameter an integer that represents the speed as the number of bits per second to transmit and receive. The speed should be set to the highest speed supported by the data port on the modem (the highest speed supported on the access server is 115,200 bps). To set the method used to control the flow of information from the access server to the modems, use the IOS line configuration subcommand flowcontrol . The command takes as a parameter the keyword hardware or software . These keywords represent the two types of flow control supported. With speeds of more than 9,600 bps, it is recommended that hardware flow control be used. The following is an example of configuring all 16 async lines on the ZIP Singapore access server to use hardware flow control at a speed of 115,200 bps. Note the use of the line major configuration command to reference async lines 1 through 16 that the subcommands are applied to: Sing2511# configure Configuring from terminal, memory, or network [terminal]? Enter configuration commands, one per line. End with CNTL/Z. Sing2511(config)# line 1 16 Sing2511(config-line)# speed 115200 Sing2511(config-line)# flowcontrol hardware Sing2511(config-line)# ^Z After the speed and flow control methods are selected, the access server must be supplied with information about the attached modem type and dialup direction information. Supplying information about the modem type eases the dialup configuration task by eliminating the need to configure the modem settings manually. Additionally, the access server can reset the modem settings after each call to ensure the proper operation of the dialup pool. Dialup direction information instructs the access server how to react to the signals sent to it by the modem during call establishment. The IOS line configuration subcommand modem is used to configure both the attached modem type and the dialup direction. For configuring the modem type, use the modem autoconfigure command. This command takes as a parameter either the keyword discovery or the keyword type . The keyword discovery instructs the access server to try to determine the type of attached modem for selecting the modem settings. The keyword type , followed by one of the predefined or user-defined modem types, instructs the access server to select the modem settings of the named type. The IOS software supports a number of popular modem types, including the U.S. Robotics Courier, the U.S. Robotics Sportster, and the Telebit T3000. If the type is not predefined, the user can establish additional types and the corresponding settings via the IOS configuration command modemcap . For establishing the dialup direction, the keyword parameter dialin or inout is used with the modem command. The following is an example of configuring the ZIP Singapore access server to use the modem settings associated with the U.S. Robotics Courier modem. The dialup direction is configured as dialin : Sing2511# configure Configuring from terminal, memory, or network [terminal]? Enter configuration commands, one per line. End with CNTL/Z. Sing2511(config)# line 1 16 Sing2511(config-line)# modem autoconfigure type usr_courier Sing2511(config-line)# modem dialin Sing2511(config-line)# ^Z Tip Even if the async lines are used only for dial-in, we recommend that you set the lines for inout operation during initial configuration and troubleshooting. This allows virtual terminal access via the Telnet protocol directly to the async line for manual modem configuration and verification. This virtual terminal access method, which is known as reverse Telnet, is described in more detail in the Configuring Modems tip on CCO at http://www.cisco.com/univercd/cc/td/doc/product/software/ios113ed/dsqcg/qcmodems.htm. With the async line configuration complete, access server security is the next step in the configuration process. As discussed in the section "Basic Access Control" in Chapter 7 , access security is broken into two steps. The first step is the authentication process, the process of identifying who is attempting access. The second step is authorizing the identified user to perform specific tasks or to give the user access to specific services. For the purposes of dialup IP, we introduce an authentication type and an authorization type that makes use of locally configured user information, which is not discussed in Chapter 7. These authentication and authorization commands make use of locally configured user information. Optionally, a security server such as a TACACS+ or a RADIUS server could be used in lieu of locally configured information, as discussed in Chapter 7. For authenticating users who attempt to access IP services via PPP, AAA authentication type ppp is used. It is enabled via the IOS configuration command aaa authentication ppp . The command takes as parameters an authentication list name or the keyword default and one or more authentication methods, such as local or, in this case, TACACS+. After a PPP user is identified, that user must be authorized to use network services (of which PPP is one). Use of network services is authorized by the aaa authorization network command. This command takes as a parameter of one or more authorization types. The following is an example of configuring the ZIP Singapore access server to authenticate PPP users with locally configured user information and to authorize the use of network services for all users who pass authentication: Sing2511# configure Configuring from terminal, memory, or network [terminal]? Enter configuration commands, one per line. End with CNTL/Z. Sing2511(config)# aaa authentication default ppp local Sing2511(config)# aaa authorization network default if-authenticated Sing2511(config)# ^Z Authentication information for the PPP users is being configured locally, so the actual usernames and passwords used for authentication must be configured. This information is configured via the IOS global configuration command username . The command takes as parameters the user ID to be used for authentication, the keyword password , and the password to be used for authenticating the user. Although the password is entered in readable clear text, it is converted to an encrypted string if password encryption is enabled, as discussed in Chapter 7. The following is an example of creating local usernames and passwords on the ZIP Singapore access server for two users, John and Jane: Sing2511# configure Configuring from terminal, memory, or network [terminal]? Enter configuration commands, one per line. End with CNTL/Z. Sing2511(config)# username john password foo Sing2511(config)# username jane password bar Sing2511(config)# ^Z The final step in configuring IP async dialup services is providing the IP protocol information that is used to establish and maintain the dialup IP session. Rather than IP protocol information being entered as line subcommands, protocol information is associated with an interface type that represents the async line, just as with any other LAN or WAN media. This interface type is called an async interface, and each async line on the access server has a corresponding async interface. IP protocol information can be entered individually on each async interface on which dialup sessions may occur, or only once via a collective async interface called the group -async interface. The group-async interface can be used to simplify configuration tasks when the same configuration commands would be applied repeatedly to multiple async interfaces. When the group-async interface is used, the IOS interface configuration subcommand group-range is used as well to identify which individual async interfaces should be included in the group structure. The following is an example of adding the description command to three async interfaces: Sing2511# configure Configuring from terminal, memory, or network [terminal]? Enter configuration commands, one per line. End with CNTL/Z. Sing2511(config)# interface async 1 Sing2511(config-if)# description dialup pool on singapore 2511 Sing2511(config-if)# interface async 2 Sing2511(config-if)# description dialup pool on singapore 2511 Sing2511(config-if)# interface async 3 Sing2511(config-if)# description dialup pool on singapore 2511 Sing2511(config-if)#^Z Here is the same configuration using a group-async interface: Sing2511# configure Configuring from terminal, memory, or network [terminal]? Enter configuration commands, one per line. End with CNTL/Z. Sing2511(config)# interface group-async 1 Sing2511(config-if)# description dialup pool on singapore 2511 Sing2511(config-if)# group-range 1 3 Sing2511(config-if)# ^Z The IP protocol information that is assigned to the async interfaces falls into three categories:
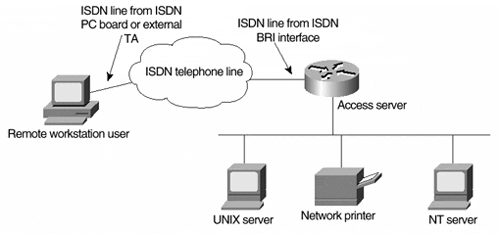
We start by examining the PPP and IP operation commands. First, the async interface must be told to use PPP as the encapsulation method for services such as IP. The IOS interface configuration subcommand encapsulation is used to specify the encapsulation type. The command takes as a parameter a keyword (for example, ppp or slip ) for the encapsulation type that is used on the interface. After PPP is configured, the network administrator has the option of configuring the async line to operate as only a dialup network services port ”that is, the user is allowed to use only the network services configured on the port, such as PPP or SLIP ”or allowing the user to receive an EXEC prompt on dialup and to choose what service to run manually. The IOS interface configuration subcommand async mode is used to specify the desired operation. The command takes as a parameter the keyword interactive or dedicated to set the desired operation. The level of expertise of the dial-in user and how the async interface is used usually determine which mode is chosen, interactive or dedicated. Configuring for dedicated operation precludes a network administrator from dialing up and being authorized to use the EXEC commands. Interactive mode can support both EXEC commands and network services. The drawback to interactive mode, however, is that inexperienced users may misconfigure their dialup software and be placed in an EXEC prompt unknowingly. When the interactive mode is used, an additional set of line commands simplifies the dialup process for the user. These commands allow the access server to determine the type of connection being attempted without requiring the user to specify the service at an EXEC prompt. This process is called autoselection. It is enabled via the IOS line configuration subcommand autoselect . This command takes as a parameter a keyword that describes the link layer protocol to be autoselected or the time the autoselect is performed (normally at user authentication time). Using autoselection when async interactive mode is configured provides the simplest method for most users to access PPP and IP services on the access server. The last PPP operations command required on the interface instructs PPP to perform authentication and authorization of dialup users before establishing PPP and IP network services. This ensures that only authorized users gain access to the network services available on the access server. This command also tells the access server which authentication protocol to use between the access server and the dialup client. Three protocols are possible ”Challenge Handshake Authentication Protocol (CHAP), Microsoft Challenge Handshake Authentication Protocol (MS-CHAP), and Password Authentication Protocol (PAP). The IOS interface configuration subcommand ppp authentication instructs the access server to perform the authentication process. The command takes as a parameter the keyword chap, ms-chap, or pap to specify the authentication protocol. A single protocol or combination of protocols may be specified in the same configuration command if dialup users are accessing with multiple authentication protocols. The command also takes an optional keyword, callin , which instructs the access server to perform the authentication challenge only on incoming dialup calls. The default is to challenge both incoming and outgoing calls. Some vendor implementations do not answer challenges if they receive an incoming call. The commands described previously are the minimum required for configuring the operation of PPP for the dialup users. With the large number of Microsoft dialup users today, the network administrator might choose to add support for Microsoft Point-to-Point Compression (MPPC), described in RFC 2118, "Microsoft Point-to-Point Compression Protocol." Compression optimizes the transmission of information over a medium such as a dialup line, which allows more information to be transmitted than would typically be possible. On relatively slow dialup lines that operate at anywhere from 28,800 bps to 53,000 bps, compression can boost the rate at which information is transmitted by as much as 1.5 times. Adding compression for the dialup users is accomplished via the IOS interface configuration subcommand compress . The compress command takes as a parameter the keyword mppc, stac, or predictor to indicate the type of compression that is to be negotiated when a dialup user is establishing a connection. The stac and predictor keywords denote using the STAC or Predictor compression algorithms. STAC is a common compression algorithm supported by many dialup clients , including Windows 95 systems, and it would be a good choice if you were supporting a large group of non-Microsoft or Windows 95 dialup users. Predictor is a much less common algorithm. Selecting Microsoft Point-to-Point Compression is accomplished via the mppc keyword. Given that Windows NT supports only MPPC, and Windows 95/98 supports both MPCC and STAC compression, selecting this compression algorithm provides the most flexibility for the network administrator supporting multiple Microsoft operating systems. At this point, let's look at an example of configuring the PPP and IP operation commands on the ZIP Singapore access server. In this example, we configure all 16 of the async lines via the group-async interface method. We establish the interfaces as PPP-encapsulated interfaces and place them in interactive mode, allowing the async lines to perform auto selection of PPP during the login process. Additionally, we configure PPP to authenticate incoming dialup calls using the CHAP, MS-CHAP, or PAP authentication protocol and then allow Microsoft compression to be negotiated: Sing2511# configure Configuring from terminal, memory, or network [terminal]? Enter configuration commands, one per line. End with CNTL/Z. Sing2511(config)# interface group-async 1 Sing2511(config-if)# group-range 1 16 Sing2511(config-if)# encapsulation ppp Sing2511(config-if)# async mode interactive Sing2511(config-if)# ppp authentication chap ms-chap pap callin Sing2511(config-if)# compress mppc Sing2511(config-if)# line 1 16 Sing2511(config-line)# autoselect ppp Sing2511(config-line)# autoselect during-login Sing2511(config-line)# ^Z With the operational mode of PPP defined, IP addressing on the async interfaces can now be performed. Normally, dialup IP users have only a single IP address associated with their workstations. Contrast this to a dialup router, which has an entire LAN segment attached and needs to perform routing with the central site for proper communications. Because each individual dialup user uses an IP address on a separate dialup connection and, therefore, a separate async interface, the actual IP address of the async interface is not important. In fact, each async interface can be treated as if it resides in the same IP address space as the attached LAN interface. These async interfaces can even be treated as if the dialup user's IP address is assigned from that address space. Looking at it from a different perspective, the dialup user is logically attached to the LAN segment via a long cable, the telephone line. No IP address is assigned to the telephone line in the same way that a LAN workstation is attached via a 10BaseT cable. The workstation receives an IP address from the same IP network address space that is assigned to the access server's LAN interface. The access server has the responsibility to accept packets from the LAN on behalf of the dialup user. It directs those packets to the proper dialup telephone call. The access server achieves this by injecting a host route (a network route with a 32-bit network mask) into the routing table of the access server when a dialup connection is established and by answering ARP requests for the IP addresses that are assigned to dialup sessions. The async interfaces themselves do not have IP addresses when using the preceding method, so the IOS interface configuration subcommand ip unnumbered can be used to enable IP processing on the async interfaces. This command was introduced in the section "Point-to-Point WAN Interface Addressing," earlier in this chapter. It is used in the same manner as described earlier ”for specifying the LAN interface of the access server as the reference interface. The following is an example of making the async interfaces of the previously configured group-async interface unnumbered on the ZIP Singapore access server: Sing2511# configure Configuring from terminal, memory, or network [terminal]? Enter configuration commands, one per line. End with CNTL/Z. Sing2511(config)# interface group-async 1 Sing2511(config-if)# ip unnumbered ethernet 0 Sing2511(config-if)# ^Z The last step in establishing IP dialup connectivity on the async interface is configuring what IP addresses are assigned to a dialup client at the time of the connection. The IOS interface configuration subcommand peer default ip address determines the method used to assign an IP address to the dialup client. By specifying a specific IP address as the parameter to the command, individual IP addresses can be assigned to each async interface. However, this requires that each async interface be manually configured with the IP address that will be assigned to dialup clients connecting on that interface. A more flexible method is assigning IP addresses from one or more address pools that have been established on the access server with the command parameter pool . This method also gives users who have permanently assigned IP addresses the flexibility of dialing into any modem port, because the access server accepts the dialup client's suggested IP address if it falls into a predefined address pool. When the pool method is specified, it is accompanied by a specific address pool name. The address pools themselves are defined using the IOS global configuration command ip local pool . This command takes as a parameter a pool name and the starting and ending IP addresses that form the pool. The IP addresses need to be from the same IP network as the access server's LAN interface. Of course, these addresses should not be assigned to any workstations that reside on the LAN segment. The following is an example of configuring the async interfaces of the previously defined group-async structure to assign IP addresses from a local pool called modem-users on the ZIP Singapore access server. Note that the pool is defined as having only 16 addresses because only 16 modems and async interfaces exist on the access server. Sing2511# configure Configuring from terminal, memory, or network [terminal]? Enter configuration commands, one per line. End with CNTL/Z. Sing2511(config)# interface group-async 1 Sing2511(config-if)# peer default ip address pool modem-users Sing2511(config-if)# ip local pool modem-users 131.108.1.111 131.108.1.126 Sing2511(config-if)# ^Z Although address pools are the most flexible method for assigning IP addresses, no method exists for coordinating the assignment of addresses across multiple access servers. In this situation, it may be better to assign addresses from a central address authority server, such as a Dynamic Host Configuration Protocol (DHCP) server. To accommodate this method, the IOS software acts as a proxy DHCP client, requesting an IP address from the DHCP server on behalf of the dialup client. This configuration method is enabled by specifying the keyword parameter dhcp to the peer default ip address command. The access server must also be configured with the IP address of a DHCP server to query for address requests via the IOS global configuration command ip dhcp-server . The address pools defined on the DHCP server would contain addresses from the IP network address of the access server's LAN interface. The following is a configuration example of the ZIP Singapore access server configured to use DHCP to assign IP addresses to dialup clients: Sing2511# configure Configuring from terminal, memory, or network [terminal]? Enter configuration commands, one per line. End with CNTL/Z. Sing2511(config)# interface group-async 1 Sing2511(config-if)# peer default ip address dhcp Sing2511(config-if)# ip dhcp-server 131.108.21.70 Sing2511(config-if)# ^Z Many dialup client PPP implementations make use of a nonstandard method for obtaining DNS and NetBIOS/WINS nameserver IP addresses during the call establishment process. This method is described in the informational RFC 1877, "PPP Internet Protocol Control Protocol Extensions for Name Server Addresses." Although not a standard, this method has been widely implemented, most notably in the Microsoft dialup implementations. The access server can also support the methods described in RFC 1877 to supply both the DNS and NetBIOS/WINS nameserver addresses. Older implementations use the IOS global configuration command async-bootp to configure these options. When configuring the IP address(es) of DNS servers, the command takes as a parameter the keyword dns-server , followed by one or more IP addresses. When configuring the IP address(es) of NetBIOS/WINS servers, the command takes as a parameter the keyword nbns-server , followed by one or more IP addresses. The following is an example of configuring the ZIP Singapore access server to supply the IP addresses of DNS and NetBIOS/WINS nameservers according to the RFC 1877 method using the async-bootp command: Sing2511# configure Configuring from terminal, memory, or network [terminal]? Enter configuration commands, one per line. End with CNTL/Z. Sing2511(config)# async-bootp dns-server 131.108.101.34 131.108.101.35 Sing2511(config)# async-bootp nbns-server 131.108.21.70 Sing2511(config)# ^Z Note Although supplying DNS and NetBIOS/WINS nameserver addresses has little to do with BOOTP, the async-bootp command was used to enable this feature in the IOS software by adding extensions to the existing SLIP BOOTP negotiation protocol commands. This method was chosen at the time in lieu of creating separate PPP commands and mechanisms to implement a nonstandard RFC. The drawback to using the async-bootp command to supply DNS and NetBIOS/WINS server addresses is that the command is an IOS global configuration command. This results in the addresses configured via the command being supplied to all dialup users in the access server, regardless of the dialup interface to which they might be connected. This has proven to be an inflexible method for network administrators who want to support multiple types of dialup connections or different classes of users and who want to supply different server addresses for those connections or users. In newer versions of the IOS software, the IOS interface configuration subcommand ppp ipcp gives the network administrator more granular control of these options on a per-interface basis. When configuring the IP address(es) of DNS servers, the command takes as a parameter the keyword dns , followed by one or two IP addresses. When configuring the IP address(es) of NetBIOS/WINS servers, the command takes as a parameter the keyword wins , followed by one or two IP addresses. The following is an example of configuring the ZIP Singapore access server to supply the IP addresses of DNS and NetBIOS/WINS nameservers according to the RFC 1877 method using the ppp ipcp command: Sing2511# configure Configuring from terminal, memory, or network [terminal]? Enter configuration commands, one per line. End with CNTL/Z. Sing2511(config)# interface group-async 1 Sing2511(config-if)# ppp ipcp dns 131.108.101.34 131.108.101.35 Sing2511(config-if)# ppp ipcp wins 131.108.21.70 Sing2511(config-if)# ^Z ISDN DialupLike asynchronous dialup, ISDN dialup involves the use of the public telephone network to enable remote workstation users to access services of a network when they are not directly connected via a LAN or WAN interface. ISDN differs from asynchronous dialup in that the calls are transmitted using synchronous digital signals. Data is converted into streams of digital information either by integrated ISDN interfaces on the router or through the use of external ISDN attachment devices called terminal adapters (TA), as discussed in Chapter 3. Remote workstation users also use either integrated ISDN PC boards or external TAs to connect to the ISDN service. Figure 4-10 shows a typical dialup scenario for a remote workstation user accessing a network via an access server with integrated ISDN Basic Rate Interfaces (BRI). Figure 4-10. Remote Dialup Access to an Access Server via ISDN Many of the configuration tasks required to set up asynchronous IP dialup services are also required to establish ISDN IP dialup services. Unlike asynchronous configuration, however, no line commands are required because the router has a directly integrated ISDN interface or because the TA is attached directly to a synchronous serial interface. If the router has an integrated ISDN interface, any commands that control the interaction of the ISDN interface with the ISDN network are applied directly to the interface. Chapter 3 shows such an example of applying ISDN SPIDs to an ISDN BRI. If the router attaches to the ISDN network via an external TA, it is configured through its own methods for proper interaction with the ISDN network. This reduces the configuration of ISDN IP dialup services to two tasks, establishing security and defining IP information. Like async interfaces, ISDN interfaces canbe configured individually or as a group. When configured as a group, the configuration commands for the multiple ISDN interfaces are associated with an interface type called a dialer interface. Individual ISDN interfaces are still configured with their ISDN-specific commands, such as SPID information. However, PPP and IP operational and protocol commands are configured on the dialer interface. Each ISDN interface included in a dialer interface structure is configured with the command dialer rotary -group . This command takes as a parameter an integer representing the dialer interface to which an interface belongs. For example, interfaces in dialer rotary-group 1 belong to interface dialer 1. The following is an example of configuring four BRI ISDN interfaces on the ZIP Singapore ISDN access server to belong to interface dialer 1: SingISDN# configure Configuring from terminal, memory, or network [terminal]? Enter configuration commands, one per line. End with CNTL/Z. SingISDN(config)# interface bri 4 SingISDN(config-if)# dialer rotary-group 1 SingISDN(config-if)# interface bri 5 SingISDN(config-if)# dialer rotary-group 1 SingISDN(config-if)# interface bri 6 SingISDN(config-if)# dialer rotary-group 1 SingISDN(config-if)# interface bri 7 SingISDN(config-if)# dialer rotary-group 1 SingISDN(config-if)# ^Z We continue by reviewing the configuration of access server security for the dialup IP network services discussed in the preceding section. As with async dialup, PPP authentication and network authorization are performed with the IOS global configuration commands aaa authentication ppp and aaa authorization network , respectively. The IOS global configuration command username is used to define the remote usernames that access the network. The following is an example of configuring the ZIP Singapore ISDN access server for PPP authentication and authorization and defining username and password pairs for remote users Jim and Janet: SingISDN# configure Configuring from terminal, memory, or network [terminal]? Enter configuration commands, one per line. End with CNTL/Z. SingISDN(config)# aaa authentication default ppp local SingISDN(config)# aaa authorization network default if-authenticated SingISDN(config)# username jim password dog SingISDN(config)# username janet password house SingISDN(config)# ^Z The IP protocol information assigned to ISDN interfaces falls into the same three categories as those of async interfaces:
We begin by recapping the PPP and IP operation commands previously discussed and introducing four new commands used with ISDN interfaces. As seen with async IP, establishing PPP as the data link layer protocol for IP on ISDN interfaces is accomplished with the IOS interface configuration subcommand encapsulation . Enabling PPP authentication before beginning IP network services and specifying the authentication protocol is accomplished with the IOS interface configuration subcommand ppp authentication . Optionally, Microsoft compression can be added with the IOS interface configuration subcommand compress mppc . The following is an example of configuring the ZIP Singapore ISDN access server to use PPP on the ISDN dialer interface, instructing the access server to use authentication and authorization for network services, and enabling Microsoft compression on the dialer interface: SingISDN# configure Configuring from terminal, memory, or network [terminal]? Enter configuration commands, one per line. End with CNTL/Z. SingISDN(config)# interface dialer 1 SingISDN(config-if)# encapsulation ppp SingISDN(config-if)# ppp authentication chap ms-chap pap callin SingISDN(config-if)# compress mppc SingISDN(config-if)# ^Z ISDN is a channelized service ”that is, it can support multiple connections over the same physical interface. This allows dialup ISDN clients to establish more than one connection at a time to an access server. This capability gives the dialup ISDN station access to twice the line capacity as using a single physical interface. Effective utilization of multiple channels is accomplished by multiplexing the data across the multiple connections using a software algorithm for PPP called multilink. Multilink PPP can be enabled via the IOS interface configuration subcommand ppp multilink . To control when ISDN channels are made operational or shut down, a list of interesting packets is defined via the IOS global configuration command dialer-list . This command takes as parameters specific network protocols that should be considered interesting for the purposes of making (or keeping) a channel active. Additionally, access lists may be used to provide further granularity, down to specific IP addresses and transport protocol service types. The dialer-list rules are applied to an interface via the IOS interface configuration subcommand dialer-group , which specifies the list number as a parameter to the command. The following is an example of configuring the ZIP Singapore ISDN access server to support PPP multilink. The interesting packets list is defined by extended access list 102: SingISDN# configure Configuring from terminal, memory, or network [terminal]? Enter configuration commands, one per line. End with CNTL/Z. SingISDN(config)# interface dialer 1 SingISDN(config-if)# ppp multilink SingISDN(config-if)# dialer-group 1 SingISDN(config-if)# dialer-list 1 protocol ip list 102 SingISDN(config)# access-list 102 permit tcp any any eq telnet SingISDN(config)# access-list 102 permit tcp any any eq www SingISDN(config)# access-list 102 permit udp any any eq domain SingISDN(config)# access-list 102 permit tcp any any eq ftp SingISDN(config)# ^Z Note Finer control of the allocation of bandwidth through the use of multiple ISDN channels is defined in RFC 2125, "Bandwidth Allocation Control Protocol (BACP)." Bandwidth Allocation Protocol (BAP), which is a subset of BACP, provides a set of rules governing dynamic bandwidth allocation through call control ”a standards method for adding and removing links from a multilink bundle. Access servers and dialup clients negotiate the rules under which dynamic bandwidth is added or removed during a session. BACP is a feature introduced in IOS software Release 11.3. Assignment of IP addresses to the access server ISDN interfaces and remote dialup workstations works in the same manner as with async interfaces. The ISDN interfaces on the access server need not be assigned specific IP addresses when only ISDN dialup workstations are accessing those interfaces. The interface can be configured as unnumbered via the Cisco IOS interface configuration subcommand ip unnumbered . The remote dialup client IP addresses may be assigned using any of the three previously discussed methods using the peer default ip address subcommand. These methods include assigning an individual remote IP address associated with each ISDN interface, using a pool of IP addresses that will be assigned to the remote ISDN clients, or assigning IP addresses obtained from a DHCP server to the remote ISDN clients. The following is an example of configuring the ZIP Singapore ISDN access server to assign IP addresses from an address pool called isdn-users for remote clients connecting on the ISDN interfaces: SingISDN# configure Configuring from terminal, memory, or network [terminal]? Enter configuration commands, one per line. End with CNTL/Z. SingISDN(config)# interface dialer 1 SingISDN(config-if)# peer default ip address pool isdn-users SingISDN(config-if)# ip local pool isdn-users 131.108.1.91 131.108.1.106 SingISDN(config-if)# ^Z DNS and NetBIOS/WINS nameserver IP addresses can also be supplied to ISDN dialup clients using the methods in RFC 1877. As with async interfaces, ISDN clients are supplied with those addresses by configuring the IOS global configuration commands async-bootp dns-server and async-bootp nbns-server , or the IOS interface configuration subcommands ppp ipcp dns and ppp ipcp wins . Using either method, the IP addresses are supplied as parameters of the commands. The following is an example of configuring the ZIP Singapore ISDN access server to supply DNS and NetBIOS/WINS IP addresses to ISDN dialup clients using the async-bootp commands: SingISDN# configure Configuring from terminal, memory, or network [terminal]? Enter configuration commands, one per line. End with CNTL/Z. SingISDN(config)# async-bootp dns-server 131.108.101.34 131.108.101.35 SingISDN(config)# async-bootp nbns-server 131.108.21.70 SingISDN(config)# ^Z The following is an example of configuring the ZIP Singapore ISDN access server to supply DNS and NetBIOS/WINS IP addresses to ISDN dialup clients using the ppp ipcp commands: SingISDN# configure Configuring from terminal, memory, or network [terminal]? Enter configuration commands, one per line. End with CNTL/Z. SingISDN(config)# interface dialer 1 SingISDN(config-if)# ppp ipcp dns 131.108.101.34 131.108.101.35 SingISDN(config-if)# ppp ipcp wins 131.108.21.70 SingISDN(config-if)# ^Z The configuration of ISDN and other dialup services described in this chapter is by no means exhaustive. We recommend that you review the documentation contained in the Cisco Systems manual sets, including case studies such as Using ISDN Effectively in Multiprotocol Networks (on CCO at http://www.cisco. com/univercd/cc/td/doc/cisintwk/ics/cs008.htm) to enhance your understanding of deploying dialup services. |
EAN: 2147483647
Pages: 116