5.3 Crime Scene Characteristics
5.3 Crime Scene Characteristics
As investigators systematically analyze crime scenes, certain aspects and patterns of the criminal's behavior should begin to emerge. Specifically, the behaviors that were necessary to commit the crime (modus operandi oriented behavior) and behaviors that were not necessary to commit the crime (motive or signature oriented behavior) may become evident if enough evidence is available. These characteristics can be used investigatively to link crimes that may have been committed by a single offender, thus changing investigators' understanding of the crime and offender. They can also lead to additional evidence and insights. For instance, realizing that an intruder broke into multiple computers on a network can result in more evidence, and the type of information on these systems can reveal an offender's true motive.
Most investigators are familiar with the concept of MO but may not realize that it is derived from a careful reconstruction of crime scene characteristics.
Crime scene characteristics are the distinguishing features of a crime scene as evidenced by an offender's behavioral decisions regarding the victim and the offense location, and their subsequent meaning to the offender. (Turvey 2002)
Such characteristics are derived from the totality of choices an offender makes during the commission of a crime. In addition to choosing a specific victim and/or target, an offender chooses (consciously or unconsciously) a location and time to commit the crime and a method of approaching the victim/target, a method of controlling the victim/target, whether or not tools will be brought or left behind, whether or not items will be taken from the scene, a method of leaving the location, and whether or how to conceal their actions. Each of these kinds of choices, and the skill with which they are carried out, evidence characteristics that establish an offender's modus operandi.
When offenders plan their crimes, they can have in mind a specific victim (someone who has wronged them), a type of victim (someone who represents a group that has wronged them), or depend on acquiring a victim of a convenient victim (someone who they can easily find and control with limited fear of detection and subsequent consequences). The amount of planning related to victim selection, approach, and control varies depending on victim type; specific victims tend to involve the most planning and victims of opportunity tend to involve the least. The victim type becomes evident after a careful study of the location that was selected to commit the crime, as well as a careful study of the victim themselves. For example:
-
With a specific victim in mind, an offender needs to plan around a specific set of pre-established variables. To complete a successful attack, the offender must know where the victim will be at a certain time, whether or not they are prepared for an attack, and how to exploit their particular set of vulnerabilities. For example, a woman who walks the same route after work, a bank that opens its vaults at a set time, or an organization that makes certain bulk transactions every evening can all be easily targeted by someone who has observed their schedule.
-
With a general type of victim in mind, an offender may regularly troll specific types of locations. Some sexual predators frequent playgrounds and online chat rooms to acquire children and others hang out at singles bars to acquire women. Still other sexual predators will troll a location of convenience, perhaps constrained by an inability to travel, and victimize family members, a neighbor, or neighbor's child.
-
When any victim will fulfill an offender's needs, an offender might trawl a convenient or comfortable location hosting a variety of victim types until a victim happens to come along. This includes shopping malls, parking lots, public parks, and individuals simply walking on the roadside. Alternatively, the offender might, on an impulse, attack the nearest available person. In such cases, the location of choice would be a reflection of the offender's regular habits and patterns.
In all of the above scenarios, the crime scene has certain characteristics that appeal to the offender. When performing an investigative reconstruction, it is important to examine carefully these characteristics and determine why they appealed to the offender. Neglecting to analyze the characteristics of a crime scene, or failing to identify correctly the significance of a crime scene can result in overlooked evidence and grossly incorrect conclusions.
Networks add complexity to crime scene analysis by allowing offenders to be in a different physical location than their victims or targets and furthermore allow them to be in multiple places in cyberspace. In essence, criminals use computer networks as virtual locations thus adding new characteristics and dimensions to the crime scene. For example, chat rooms and news-groups are the equivalent of town squares on the Internet providing a venue for meetings, discussions, and exchanges of materials in digital form. Criminals use these areas to acquire victims, convene with other criminals, and coordinate with accomplices while committing a crime.
CASE EXAMPLE
Some groups of computer intruders meet on IRC to help each other gain unauthorized access to hosts on the Internet. If the owner of a system that has been broken into does not notice the intrusion, word gets around and other computer intruders take advantage of the compromised system. Thus, a group of computer intruders become squatters, using the host as a base of operations to experiment and launch attacks against other hosts. IRC functions as a staging area for this type of criminal activity and investigators sometimes can find relevant information by searching IRC using individualizing characteristics of the digital evidence that the intruders left at the primary crime scene; the compromised host.
Criminals choose specific virtual spaces that suit their needs and these choices and needs provide investigators with information about offenders. An offender might prefer a particular area of the Internet because it attracts potential victims or because it does not generate much digital evidence. Another offender might choose a virtual space that is associated with their local area to make it easier to meet victims in person. Conversely, an offender might select a virtual space that is far from their local area to make it more difficult to find and prosecute them (Figure 5.3).
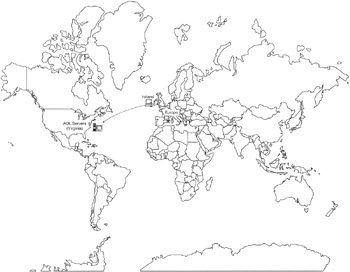
Figure 5.3: Offender in Europe, victim in the United States, crime scenes spread around the world on personal computers and servers (AOL in Virginia).
When a crime scene has multiple locations on the Internet, it is necessary to consider the unique characteristics of each location to determine their significance, such as where they are geographically, what they were used for, and how they were used. An area on the Internet can be the point of contact between the offender and victim and can be the primary scene where the crime was committed, or secondary scene used to facilitate a crime or avoid apprehension. The type of crime scene will dictate how much evidence it contains and how it will be searched. For example, a primary scene on a local area network will contain a high concentration of evidence (many bits per square inch) and can be searched thoroughly and methodically. Conversely, when secondary scenes are on the Internet, evidence might be scattered around the globe making a methodical search impractical and making any investigative direction towards a competent reconstruction all the more valuable.
5.3.1 Method of Approach and Control
How the offender approaches and obtains control of a victim or target is significant, exposing the offender's confidences, concerns, intents, motives, etc. For example, an offender might use deception rather than threats to approach and obtain control because he/she does not want to cause alarm. Another offender might be less delicate and simply use threats to gain complete control over a victim quickly.
An offender's choice of weapon is also significant. For practical or personal reasons an offender might choose a lead pipe, a gun, or a computer connected to a network to get close to and gain control over a victim or target. Criminals use computer networks like a weapon to terrorize victims and break into target computer systems. Although a criminal could visit the physical location of their victims or targets, using a network is easier and safer, allowing a criminal to commit a crime from home (for comfort) or from an innocuous Internet cafe (for anonymity).
When an offender uses a network to approach and control a victim, the methods of approach and control are predominantly verbal since networks do not afford physical access/threats. These statements can be very revealing about the offender so investigators should make an effort to ascertain exactly what the offender said or typed. The way a computer intruder approaches, attacks, and controls a target can give investigators a clear sense of the offender's skill level, knowledge of the computer, intents, and motives. Crime scene characteristics of computer intrusions are described more fully in Chapter 19.
Different offenders can use the same method of approach or control for very different reasons. Subsequently, it is not possible to make reliable generalizations based on individual crime scene characteristics. For example, one offender might use threats to discourage a victim from reporting the crime whereas another offender might simply want control over the victim regardless of the surrounding circumstances. Therefore, it is necessary to examine crime scene characteristics in unison, determining how they influence and relate to each other.
5.3.2 Offender Action, Inaction and Reaction
Seemingly minor details regarding the offender can be important. Therefore, investigators should get in the habit of contemplating what the offender brought to, took from, changed or left at the crime scene. For instance, investigators might determine that an offender took valuables from a crime scene, indicating a profit motive. Alternatively, investigators might determine that an offender took a trophy or souvenir to satisfy a psychological need. In both cases, investigators would have to be perceptive enough to recognize that something was taken from the crime scene.
Although it can be difficult to determine if someone took a copy of a digital file (e.g. a picture of a victim or valuable data from a computer), it is possible to do so. Investigators can use log files to glean that the offender took something from a computer and might even be able to ascertain what was taken. Of course, if the offender did not delete the log files investigators should attempt to determine why the offender left such a valuable source of digital evidence. Was the offender unaware of the logs? Was the offender unable to delete the logs? Did the offender believe that there was nothing of concern in the logs? Small questions like these are key to analyzing an offender's behavior.
EAN: 2147483647
Pages: 279