19.3 Investigative Reconstruction
19.3 Investigative Reconstruction
...the safecracker has been portrayed as a masked, bewhiskered, burly individual whose daring was matched only by his ruthlessness in disposing of interference. This legend undoubtedly had its origin in the facility with which the safecracker could be caricatured by cartoonists. His safe, mask, blackjack, and flashlight have come to be the picturesque symbols of the professional criminal. By this intimate association, the safe burglar has acquired in fiction the attributes of character corresponding to the physical properties of the safe itself - steely toughness of fiber and impregnability to moral suasion. Historically, this picture may have been true, but modern criminal society is far more democratic. The safecracker category, for example, includes all races, colors, and creeds: the skilled craftsman and the burglar; the timid and the bold; the lone wolf and the pack member; the professional criminal and the young amateur trying his wings; the local thug and the strong boy from a distant city. The occupation of safecracker has proved so remunerative to some practitioners, that its membership has swollen beyond the limits imposed by any of the restrictions of qualifications in the form of skill. (O'Hara 1970)
Like their predecessors (safe crackers), individuals who break into computers for profit have been stereotyped to the extreme. Despite overwhelming evidence to the contrary, computer intruders have been stereotyped as white, middle class, obsessive antisocial males between 12 and 28 years old with an inferiority complex, and a possible history of physical and sexual abuse (Casey 2002). Several other attempts have been made to create statistical profiles of computer intruders using information from media reports, offender interviews, and anecdotal observations. Although these profiles may give a general overview of past offenders and might be useful for diagnosing and treating associated psychological disorders, they have little investigative usefulness. In fact, such inductive criminal profiles can mislead investigators, causing them to jump to incorrect conclusions about an offender.
A more effective approach to learning about an offender in a given crime is to perform an investigative reconstruction as detailed in Chapter 5. By objectively analyzing available evidence, learning about the victims, and recognizing significant aspects of the crime scenes, an investigator can discern patterns of behavior and can gain a better understanding of the relationships between the victim, offender, and crime scenes, ultimately leading to a clearer understanding of the offender.
19.3.1 Parallels between Arson and Intrusion Investigations[10]
It is useful to examine well-established disciplines, such as arson investigation, to gain insight into the problems we face today in computer crime investigations. Although computer crime is a new development, there are many similarities between a computer that contains evidence and an arson crime scene. Most essentially, in all cases, people are responsible for the actions that leave behind clues. Additionally, as noted in the opening quotation of this chapter, we are dealing with evidence that has deteriorated significantly. An arson investigator's task is to recover fragmentary evidence and use it to determine what occurred.
When computer intruders make no effort to conceal their activities, investigators can obtain information about the offender's behaviors from log files and other available digital evidence. However, if significant evidence has been destroyed, it is more difficult to determine what the intruder intended and investigators must rely more heavily on crime scene characteristics and victimology to understand the incident. Arson investigators are familiar with this type of situation - similarities between arson and computer intrusions are shown in Table 19.2.
| FEATURE | ARSON | COMPUTER CRIME |
|---|---|---|
| Dimensional expansion | Evidence may be found far from the blast or may have been projected vertically onto roofs, into trees, etc. | Evidence may be located in distant hosts. Network monitoring systems may have relevant log files |
| Layering | Burnt, collapsed structures create layers of evidence | Deleted data on a computer disk are layered under active data |
| Tools | Accelerants, explosive materials, bomb fragments, and other items found at the crime scene may have class characteristics that help connect the crime to the perpetrator | Toolkits and other items found at a computer crime scene may have class characteristics that help connect the crime to the perpetrator |
| Secondary scenes | An arsonist's home or bomb maker's workshop generally have evidence that can be linked with the scene | Computers used by the offender to compile programs or launch an attack usually have evidence that can be linked to the scene |
| MO, signature, skill | The composition of an incendiary device can be unique to the offender, such as detonator or explosive mixture used, revealing the offender's skill level | Tools used by computer criminals can have unique characteristics introduced by the offender, revealing the offender's skill level |
Despite a paucity of evidence and a chaotic crime scene, arson investigators have learned to examine a scene methodically for the kinds of clues that have been most useful for solving crimes in the past. Arson investigators look for several key crime scene characteristics, related to those discussed in Chapter 5, that are applicable to computer intrusions: point of origin, method of initiation, requisite skill level, nature, and intent (Table 19.3).
| POINT OF ORIGIN | METHOD OF INITIATION | REQUISITE SKILL LEVEL | NATURE AND INTENT | |
|---|---|---|---|---|
| Arson | Warehouse window | Matches and crude fuse (cotton rag soaked in gasoline) | Low (simple Molotov cocktail - readily available materials) | Broad targeting (destroy warehouse) |
| Arson | Engine (front of car) | Electric arc (triggered by car ignition) | High (car bomb made with military grade explosives) | Narrow targeting (kill car driver) |
| Intrusion | SSH server (port 22) | Buffer overflow (CRC-32 compensation attack detector vulnerability) | Low (exploit freely available on Internet) | Targeting and intent unclear (need more details) |
| Intrusion | /tmp/.tmp (cwd of process) | Rootkit (t0rnkit) script | Medium (rootkit available on Internet) | Concealment (precautionary act) |
| Intrusion | /home/janedoe (cwd of process) | "sudo rm -rf ../johndoe/*" | Low (simple UNIX command) | Narrow targeting (delete user files) |
Let us first consider the nature and intent of the crime. Computer criminals and arsonists alike may destroy evidence to cover their tracks, to retaliate against some perceived wrong, and/or to demonstrate their power. To determine whether destruction was intended to inflict damage or simply as a precautionary act, it is helpful to consider whether the targeting was broad or narrow. Narrow targeting refers to any destruction that is designed to inflict specific, focused, and calculated amounts of damage on a specific target such as targeting "/home/janedoe" in Table 19.3. Broad targeting refers to destruction that is designed to inflict damage in a wide reaching fashion. Rather than targeting a single individual by deleting their files, an intruder might delete information that is important to the entire organization, targeting the entire organization or what it represents as in the following case example:
CASE EXAMPLE (NEW JERSEY 1996):
Tim Lloyd, the primary system administrator for Omega Engineering Corporation, was originally fired for stealing expensive equipment. In retaliation, Lloyd executed time-delayed commands on Omega's primary server that deleted all of the company's important data and programs on a specific date. Specifically the method of initiation was a modified version of the DELTREE command ("FIX /Y F:\*.*") to delete everything on the drive combined with the "PURGE F:\/ALL" command to obliterate the deleted data. A high degree of skill was required to implement this narrowly targeted attack and the intent was to destroy all of Omega's important data and programs. Lloyd also erased all related backup tapes. Experts spent years recovering pieces of information from the servers, desktops, and even computers of ex-employees. Although the damage was extensive, this attack is considered narrowly targeted because it was designed to inflict a specific damage on a specific target. (Gaudin 2000)
In this case, the nature of the crime was malicious and Lloyd's intent was to punish his former employer for perceived wrongs.
To determine if the targeting was narrow or broad, it is helpful to determine intentional versus actual damage. This means learning as much about the configuration of the target computer as possible and the amount of damage incurred by the target. For example, programs like chroot limit the damage that can be done on a system if one application (e.g. a Web server) is compromised. An intruder who was hoping to damage a wide area of the computer would be thwarted by such restrictions. If the intruder destroys everything in the restricted area, this is likely evidence of broad targeting and the intruder might not have achieved his/her goal of destroying everything on the computer. On the other hand, if the intruder deletes a few files in the restricted area, this is evidence of narrow targeting and the intruder probably achieved his/her goal.
The Lloyd case example also demonstrated that, in addition to knowing the perpetrator's intent, determining who had access to the point of origin or method of initiation can lead to prime suspects. For instance, in Table 19.3 only a few people had access to the point of origin "/home/janedoe" and the method of initiation "sudo," reducing the suspect pool to Jane Doe and others with administrative privileges on the system. In the previous case example, digital evidence recovered from the damaged system immediately implicated Lloyd because he was the only individual with the requisite access to the point of origin and ability to create the destructive program.
Determining skill level can also lead to suspects. The skill level and experience of a computer criminal is usually evident in the methods and programs used to break into and damage a system. For instance, an offender who uses readily available software and chooses weak targets for little gain is generally less skilled and experienced than an offender who writes customized programs to target strong installations. A skilled computer criminal might create a time bomb specifically designed to destroy important data at a particular time or when a certain triggering event occurs as in the previous case example. Having said this, a skilled offender can successfully achieve specific goals using programs that exist on the system. Therefore, what is known about point of origin, method of initiation, and nature and intent of the destructive act should all be taken into account when assessing the offender's skill level.
Notably, precautionary acts - destroying data to conceal, damage, or destroy any items of evidentiary value - are not always very thorough. Items that an intruder intended to destroy can be examined by digital evidence examiners to exploit them for their full evidentiary potential, no matter how little debris is left behind. For example, if a small portion of a deleted file remains on a disk, this remaining digital evidence should be carefully reconstructed and examined to determine why the offender tried to destroy it.
19.3.2 Crime Scene Characteristics
In addition to being a primary crime scene, computers can be secondary scenes in the form of launch pads, listening posts, or storage sites. Intruders use launch pads to hide their identities while committing other crimes (e.g. breaking into other computers, distribute illegal materials, cyberstalking). Also, intruders often use a launch pad when the target computer is difficult to compromise from outside a network but can be compromised from another computer on the same network. Intruders use listening posts to look for other likely targets on a network, and use storage sites to keep toolkits, stolen data, and other incriminating evidence. These secondary scenes can be a rich source of digital evidence that can be associated with a particular individual.
A computer intruder's method of approach and attack can reveal a significant amount about the offender's skill level, knowledge of the target, and intent. The concept of broad versus narrow targeting can also be useful when examining the method of approach and attack. For instance, network logs may show a broad network scan prior to an intrusion, suggesting that the individual was exploring the network for vulnerable and/or valuable systems. This exploration implies that the individual does not have much prior knowledge of the network and may not even know what he/she is looking for but is simply prospecting. Conversely, intruders who have prior knowledge of their target will launch a more focused and intricate attack. For instance, if an intruder only targets the financial systems on a network, this directness suggests that the intruder is interested in the organization's financial information and knows where it is located.
So, if the targeting is very narrow — the intruder focuses on a single machine - this indicates that he/she is already familiar with the network and there is something about the machine that interests him/her. Similarly, time pattern analysis of the target's file system can show how long it took the intruder to locate desired information on a system. A short duration is a telltale sign that the intruder already knew where the data were located, whereas protracted searches of files on a system indicates less knowledge. The intruder's knowledge of the target and criminal skill can be very helpful in narrowing the suspect pool, particularly when only a few individuals possess the requisite knowledge and skills suggesting insider involvement.
The sophistication of the intrusion and subsequent precautionary acts help determine the perpetrator's skill level.
CASE EXAMPLE
An organization received a complaint that one of their Solaris workstations was being used to launch attacks against others on the Internet. The organization was not particularly concerned by the complaint since the workstation did not contain valuable information and believe that the problem could be resolved with relative ease.
Examining the server revealed obvious signs of intrusion. The intruder had gained access through a vulnerability that had been widely publicized that week, added a new account, deleted log files but failed to cover tracks completely. In short, this intruder was noisy, lacked finesse, and was not interested in information on the system. These factors are consistent with a low skill intruder. However, a closer examination of the system revealed an oddity one month earlier:
# ls -altc /usr/ucb/ps | head -rwsr-xr-x 1 root sys 24356 Jun 6 17:20 ps # ls -altc /usr/sbin/inetd | head -r-xr-xr-x 1 root root 39544 Jun 6 17:20 inetd
An analysis of the ps command showed that it had been compiled using a non-Sun compiler, indicating that the vendor had not created it. There were no unusual entries in log files from that time period but searching for other files created on that date led to a sniffer that was cleverly concealed within the system:
# ls -altc /kernel -rw-r--r-- 1 root root 60 Jun 6 17:20 pssys # more /kernel/pssys 1 "./update.hme -s -o output.hme" # cd /usr/share/man/tmp # ls -altc total 156 -rw-r--r-- 1 root root 23787 Jun 12 07:52 output.hme drwxr-xr-x 2 root root 512 Jun 6 17:20 . drwxr-xr-x 40 bin bin 1024 Jun 6 17:20 .. -rwx------ 1 root root 25996 Jun 6 17:20 update.hme
The sniffer output file "output.hme" contained the following entry, indicating that the intruder could have observed legitimate users on the network accessing valuable research data on another system:
-- TCP/IP LOG -- TM: Fri Jun 11 10:28:52-- PATH: host01.corpY.com(64376) => server.corpY.com(ftp) STAT: Fri Jun 11 10:30:45, 20 pkts, 135 bytes [DATA LIMIT] DATA: USER james : :PASS smiley:)-99 : :CWD researchdata : : GET research0302.dat
This intruder left almost no trace of the intrusion and used relatively sophisticated concealment techniques, suggesting a high skill level. Without additional evidence, it was not possible to determine how the intruder had gained access to the system. The most likely hypothesis was that this intruder used the same vulnerability exploited by the second intruder but knew about it several weeks before it became widely publicized. The cautious, focused nature of the attack suggested that the intruder had a particular goal and was monitoring network traffic to achieve this goal. However, without additional evidence it was not possible to determine if the intruder was interested in the research data or something else on the organization's network.
This case example demonstrates how the choice of secondary crime scene can be significant, leading to additional insights. The intruder deliberately selected the Solaris workstation as a listening post, revealing a high skill level and a specific interest in monitoring network traffic. In other cases, an intruder may select a computer to launch an attack because the computer itself is fast, it is connected to a fast network, it is easy to break into, it is located in a different country, or it is located near the target. Alternatively, an intruder may use a particular network to launch attacks because he/she has broken into computers on the network before and is confident that he will not be caught. If the intruder has broken into other systems on the network in the past, the organization may have archived digital evidence from those systems that can help apprehend the offender.
Seemingly minor details regarding the offender can be important. Therefore, investigators should get in the habit of contemplating what the offender brought to, took from, changed, or left at the crime scene. For instance, investigators might determine that an offender took valuables from a crime scene, indicating a profit motive. Alternatively, investigators might determine that an offender took a trophy or souvenir to satisfy a psychological need. In both cases, investigators would have to be perceptive enough to recognize that something was taken from the crime scene.
Although it can be difficult to determine if someone took a copy of a digital file (e.g. a picture of a victim or valuable data from a computer), it is possible. Investigators can use log files to glean that the offender took something from a computer and might even be able to ascertain what was taken. Of course, if the offender did not delete the log files investigators should attempt to determine why the offender left such a valuable source of digital evidence. Was the offender unaware of the logs? Was the offender unable to delete the logs? Did the offender believe that there was nothing of concern in the logs? Small questions like these are key to analyzing an offender's behavior.
CASE EXAMPLE
An organization believed that an ex-employee stole information prior to quitting on September 16, 2002. Investigators were asked to determine if the ex-employee had taken documents from his Windows 2000 workstation, a copy of the client contact database (clients.mdb), or anything related to a sensitive project called "ProjectX" stored on a UNIX file server (192.168.2.10). Investigators preserved digital evidence on the Windows 2000 and UNIX systems by making a bitstream copy of the hard drives. Logon/logoff records from the ex-employee's workstation indicate that he used the computer on September 16, 2002, between 08:50 A.M. and 09:10 A.M.:
C:\>ntlast /ad 16/9/2002 /v Record Number: 18298 ComputerName: WKSTN11 EventID: 528 - Successful Logon Logon: Tue Sep 16 08:50:58am 2002 Logoff: Tue Sep 16 09:10:00am 2002 Details - ClientName: user11 ClientID: (0x0,0xDCF9) ClientMachine: WKSTN11 ClientDomain: CORPX LogonType: Interactive
Investigators check the building security (card swipe) records to confirm that the ex-employee was in the vicinity of the computer at the time. These records show that the suspect entered the building at 08:45 A.M.
Further examination of the ex-employee's workstation shows that the "clients.mdb" file was accessed at 08:58:30 A.M. and that a related file named "clients.xls" was created shortly after in a temporary directory. The ex-employee's e-mail outbox shows the "clients.xls" was sent to a Hotmail address. Performing a functional reconstruction of the "Send To" feature in Microsoft Access suggests that the ex-employee used this method to e-mail the database. Another file named "private.doc" was accessed at around the same time as a shortcut file (with a ".Ink" extension) associated with the floppy drive (A:), suggesting that the file was copied to a floppy disk using the "Send To" feature of Windows. The last accessed date-time stamp of another shortcut file indicated that the SSH client on the machine was launched. Additionally, the following SSH key file associated with the UNIX file server had been accessed at the same time, suggesting that a connection was made to the server at that time:
C:\Documents and Settings\user11\Application Data\SSH\ HostKeys\ key_22_192.168.2.10
Logon records on the UNIX server show a corresponding logon session from the ex-employee's computer. A sensitive file named "projectX" was found on the server and had a last access date-time consistent with the logon session:
% last user 11 user11 pts/77 wkstn11.corpx.com Sep 16 09:05-09:06 (00:01) % Is -altu -rwxr-xr-x 1 admin staff 8529583 Sep 16 09:05 projectX
A deleted copy of the "projectX" file was recovered from the ex-employee's workstation. Comparing the date-time stamps of this file with the copy on the server indicates that the file was copied from the server at 09:05 A.M. Specifically, the date-time stamps of deleted "projectX" file recovered from the ex-employee's workstation were:
Created: 09:05 A.M: Accessed: 09:07 A.M: Modified: 09/12/2002 10:07:07 A.M.
Also of note was an entry in the Registry (HKEY_USERS\<user11-sid>\Software\Windows\Explorer\RecentDocs\NetHood) indicating that a NetBIOS connection had been established between the ex-employee's workstation and a computer on a competitor's network. This Registry key had a Last Write Time of 09/13/2002 at 11:04 A.M. and network logs confirmed a connection at this time. Network logs also showed a NetBIOS connection from the ex-employee's computer to the competitor's network at 09:07 A.M. on September 16, 2002:
[**] Netbios Access [**] 09/16-09:07:03.313894 192.168.16.88:1576 → 172.16.14.3:139 TCP TTL:127 TOS:0x0 ID:61055 lpLen:20 DgmLen:231 DF ***AP*** Seq: 0x4A8908DB Ack: 0x5C6EF875 Win: 0x431B TcpLen: 20 This connection was also recorded in the following NetFlow logs:
Start End SrcIPaddress SrcP DstIPaddress DstP P Fl Pkts Octets 0916.09:07:04 0916.09:07:56 192.168.16.88 1576 172.16.14.3 139 6 3 9711 8693271
The fact that the number of bytes transferred is roughly equivalent to the size of the "projectX" file indicates that this file was transferred to the competitor's system.
This example demonstrates the usefulness of network level logs to corroborate important events. These types of corroborating evidence are especially important when investigating computer intrusions because automated toolkits enable even low skilled offenders to employ sophisticated concealment techniques on a compromised host.
19.3.3 Automated and Dynamic Modus Operandi
Toolkits that automate the actions required to break into a computer and destroy or conceal evidence of the intrusion provide an automated modus operandi that make multiple offenders almost indistinguishable. When every crime scene looks almost identical, it becomes more difficult to link cases committed by a single offender and to understand the unique motivations of different offenders. Although these toolkits reduce the amount of behavioral information that is available to investigators, it is possible to differentiate between automated actions and the offender's behavior.
CASE EXAMPLE
An organization became concerned when they detected an attack against a server that contained valuable intellectual property:
[**] FTP-site-exec [**] 09/14-12:27: 208.181.151.231 -> 192.168.12.54 09/14-12:28: 24.11. 120.215- -> 192.168.12.54 09/14-12:33: 64.28.102.2 -> 192.168.12.54
The digital evidence examiner noted that the server's clock was 4 hours, 40 minutes fast but did not find any signs of compromise initially. There were no entries in the wtmp or syslog files at the time of the attack, no unusual processes were visible using ps, and the Is and find commands did not reveal anything alarming. However, comparing the output of ps and Isof uncovered several discrepancies, suggesting that the system was compromised.
The digital evidence examiner made a bitstream copy of the hard drive and observed two directories that had not been visible during the initial examination: "/usr/info/.t0rn" and "/usr/src/.puta/t0rnsniff." The examiner also found a modified copy of a rootkit named "Tornkit" that the intruder had used (Figure 19.2). Searching the Internet revealed that this rootkit was being used by intruders around the world and had become common enough to warrant an advisory from CERT.[11]
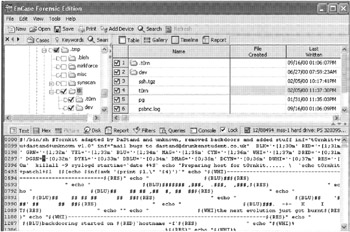
Figure 19.2: EnCase used to analyze Linux system showing rootkit installations script.
Searching unallocated space for deleted syslogs (taking into account the clock offset) uncovered the following entry showing a buffer overflow of the FTP server:

This and other recovered logs entries confirmed the source of initial intrusion. Other recovered log segments indicated that the intruder had been monitoring network traffic:
Sep 15 23:05:41 host1 kernel: device eth0 entered promiscuous mode Sep 15 23:09:37 host1 kernel: device eth0 left promiscuous mode Sep 15 23:09:39 host1 kernel: device eth0 entered promiscuous mode Sep 15 23:10:22 host1 kernel: device eth0 left promiscuous mode Sep 15 23:10:27 host1 kernel: device eth0 entered promiscuous mode
After performing an investigative reconstruction, it was concluded that the target was at high risk of intrusion and that the intruder was not aware of the valuable information on the server. The server was at high risk of intrusion because it was not protected by a firewall and was running an FTP server with a well-known vulnerability that was trivial to exploit. The intrusion was preceded by a broad scan of the network for systems with vulnerable FTP servers, suggesting that the intruder was not specifically targeting one particular server. The intruder's ignorance of the valuable contents of the server was further evident from date-time stamps on the file system - the sensitive data had not been accessed during the intrusion. Also, the intruder's primary intent was to use the compromised host to launch attacks against other systems, monitor network traffic for passwords, and connect to IRC. These activities were not consistent with a sophisticated attacker who was interested in stealing the information on the server.
More experienced intruders often have a preferred toolkit that they have pieced together over time and that have distinctive features. For instance, a compressed TAR file containing the following tools were found on several compromised machines, indicating that a single offender was responsible for all of the intrusions:
% tar tvf aniv.tar -rw-r--r-- 1 358400 Mar 8 17:02 BeroFTPD-1.3.3.tar.gz -rw-r--r-- 1 326 Mar 8 17:02 readmeformountd -rw--r--r-- 1 757760 Mar 8 17:02 root.tar.gz -rwxr-xr-x 1 8524 Mar 8 17:02 slice2 -rw-r--r-- 1 6141 Mar 8 17:02 mountd.tgz -rw-r--r-- 1 849920 Mar 8 17:02 rkb.tar.gzb
Also, some intruders personalize their toolkits with nicknames and comments. For instance, the following rootkit script recovered from several compromised Solaris systems contains the intruder's nickname and had been modified in later intrusions to use "/var/yp/..." instead of "/var/tmp/..." as a working directory:
#[*] - hacker nickname #[*] -SunOS rootkit v1 echo "creating directories" mkdir /var/yp/…/ mkdir /var/yp/…/old/ echo "switching directory…" cd stuff echo "moving files…" mv * /var/yp/…/ echo "cleaning up…" cd ‥ rm -rf stuff rm -rf s1.tar
So, in addition to being helpful for linking intrusions committed by the same individual, distinctive features of a toolkit can be viewed as both an MO- and signature-related behavior. However, keep in mind that the intruder may have been given a customized toolkit and may not have personalized it himself/herself.
In addition to the contents of a toolkit, the way a particular intruder uses a toolkit can be unique. For instance, it is sometimes possible to recover a list of the commands an intruder typed, revealing MO-related behavior as shown here:
% more .bash_history w pico /etc/passwd mkdir /lib/.loginrc cd/lib/.loginrc /usr/sbin/named ls w ls /usr/sbin/named ls cd ~ ls mv aniv.tar.gz /lib/.loginrc cd /lib/.loginrc tar zxf aniv.tar.gz ls cd aniv ls tar zxf rkb.tar.gz ls cd rkb ./install
These commands refer to a directory named "/lib/.loginrc" that was useful for linking several intrusions to the same offender.
To make case linkage even more difficult, offenders who use the Internet can change their modus operandi with relative ease. As offenders become more familiar with the Internet, they usually find new ways to make use of it to achieve their goals more effectively. An offender who uses the Internet creatively can change his modus operandi so frequently and completely that it is best described as dynamic. For instance, individuals who break into well-secured computer systems may have to develop a novel intrusion plan for each unique target. A dynamic modus operandi has also been seen when an offender is consciously trying to foil investigators.
19.3.4 Examining the Intruder's Computer
If all goes well in an investigation, the intruder's computers can be examined for evidence relating to the crime. Recalling Locard's Exchange Principle, during the commission of a crime, evidence is transferred between the offender's computer and the target. For instance, in one case the intruder's Windows NT computer contained the following digital evidence linking him with the compromised systems:
-
lists of dial-up accounts and passwords, including the one used to commit crimes;
-
nmap scans of target networks;
-
lists of compromised hosts (trophy list and memory aid);
-
list of UNIX commands executed on compromised hosts (memory aid);
-
sniffer logs from compromised hosts (digital evidence transfer);
-
directory listings from compromised UNIX hosts (digital evidence transfer);
-
stolen data from compromised hosts, including credit cards and private e-mail;
-
TAR file with class characteristics linking it to compromised UNIX host;
-
toolkits found on compromised hosts;
-
FTP and terminal emulator configuration files relating to compromised hosts;
-
IRC logs showing suspect connecting to IRC from compromised hosts;
-
IRC logs of suspect boasting about breaking into specific hosts;
-
IRC logs of suspect communicating with accomplices.
When examining an intruder's computer, begin by searching for what is known such as the time periods of the intrusions, host names, IP addresses, and stolen user accounts. Searching for online nicknames may uncover remnants of online communications with accomplices and mention of other targets. The MD5 values of files found on the compromised hosts can be used to search for identical files on the intruder's hard drive. Any files that are found can be further analyzed for class characteristics that link them to a particular host. It may also be fruitful to look for evidence transfer such as directory listings from the compromised systems (e.g. in unallocated space or a swap file).
[10]This section is adapted from Casey, E. (2003), Arson, Archaeology, and Computer Crime Investigation, Computer Fraud and Security.
[11]http://www.cert.org/incident_notes/IN-2000-10.html
EAN: 2147483647
Pages: 279