10.3 Overview of Digital Evidence Processing Tools
10.3 Overview of Digital Evidence Processing Tools
Prior to making a bitstream copy of a disk, it may be necessary to perform a keyword search to determine if there is relevant digital evidence on the system. This is particularly useful when looking for specific items on a large number of systems. The most efficient approach to searching many computers is to boot them using an evidence acquisition boot disk and run a disk search utility from the DOS prompt. EnCase,[5] DiskSearch Pro,[6] and Linux have this keyword search capability. Once a system with useful evidence has been identified, a full bitstream copy can be made for further examination.
As noted in Chapter 2, Safeback[7] was one of the earliest DOS-based tools for copying digital evidence sector-by-sector. Booting from a floppy disk, Safeback can make an exact copy of a drive in a way that preserves its integrity. Since then, several tools have been developed to acquire evidence from a disk, including EnCase, Forensic Toolkit[8], SnapBack DatArrest,[9] and Byte Back.[10] Rather than calculating integrity checks of acquired data separately, EnCase and Safeback store acquired data along with integrity checks at regular intervals throughout their evidence files. Some believe that these proprietary formats are not an exact copy of the disk even though they contain all of the information from the disk. The crux of this argument is that data is arranged differently in the proprietary file format than on the original disk (Scott 2003). Others believe that this proprietary format is better because it maintains integrity checks throughout the file, enabling digital investigators to identify what portion of data is creating a problem if there is a problem. Whichever approach is used, courts are generally satisfied provided the evidence can be authenticated as described in Chapter 7. Also, since it is advisable to make two copies using different tools, one copy can be made in a proprietary format and the other using the de facto dd standard.
Most of these tools can either use information from the BIOS, or bypass the BIOS and access the disk directly to ensure that no false information in the BIOS causes a partial acquisition. Some of these tools contained bugs that prevented them from acquiring all of the data on some drives. For this reason, it is important to compare the amount of data that were copied with the size of the drive (Cylinders Heads Sectors per track) as described in Chapter 8.
Once digital evidence has been acquired, there are two main approaches to viewing digital evidence: physically and logically. The physical view involves examining the raw data stored on disk using a disk editor such as Norton DiskEdit or WinHex. Data are generally shown in two forms in a disk viewer: in hexadecimal form on the left and in plain text on the right. The advantage of DiskEdit is that it can run from a bootable floppy disk but WinHex has more examination and analysis capabilities such as recovering all slack or unallocated space, and comparing files to find any differences. For instance, Figure 10.2 shows WinHex being used to compare two seemingly identical Microsoft Word documents created at different times to locate internal date-time stamps discussed later in this chapter.
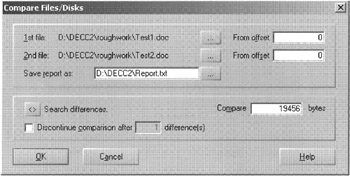
Figure 10.2: WinHex "File Manager Compare" feature.
The logical view involves examining data on a disk as it is represented by the file system. In the past digital investigators used Norton Commander (Figure 10.3) to view the file structure on a drive. Viewing the file system in this way facilitates certain types of analysis but does not show underlying information that is visible using a disk editor. Also, Norton Commander displays limited file information such as name, size, modification time, and attributes.[11]
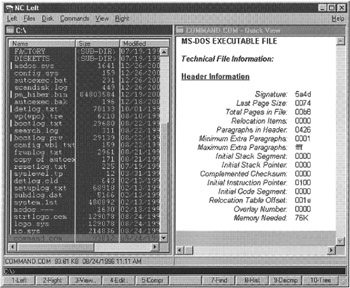
Figure 10.3: Norton Commander.
Each of the above methods of viewing a disk has limitations. For instance, when searching for a keyword, a physical sector-by-sector search will not find occurrences of the keyword that are broken across non-adjacent sectors (the sectors that comprise a file do not have to be adjacent). On the other hand, a physical examination gives access to areas of the disk that are not represented by the file system such as file slack and unallocated space. Integrated tools like EnCase and Forensic Toolkit (FTK[12]) on Windows, and The Sleuth Kit[13] on UNIX combine both of these and other features into a single tool, enabling an examiner to view a disk physically and logically. EnCase and FTK have many other capabilities that facilitate examine of digital evidence, some of which are demonstrated later in this chapter. It is critical to realize that any tool that represents data on a disk can contain bugs that misinterpret data. Therefore, verify important results using multiple tools.
Other tools exist to facilitate specialized tasks during examination such as Maresware utilities described in Chapter 24. Also, Net Threat Analyzer from NTI (www.secure-data.com) will search a binary file such as unallocated space or a swap file for Internet-related data such as e-mail addresses and Web pages (Figure 10.4).
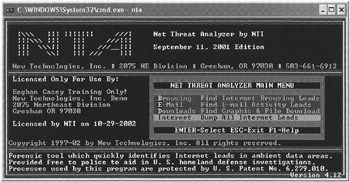
Figure 10.4: NTI Net Threat Analyzer—
No single tool is suitable for all purposes and it is advisable to verify important findings with multiple tools to ensure that all findings are accurate. In some cases, it is advisable to verify results at the lowest level using a disk editor. There is still some debate regarding the best approach to examine digital evidence - using tools from the command line or through a Graphical User Interface. Provided the forensic principles outlined in Chapter 9 are abided by, it does not matter if the tool has a Windows interface or must be run from the command line.
[5]http://www.encase.com
[6]http://www.forensics-intl.com
[7]http://www.sydex.com
[8]http://www.accessdata.com
[9]http://www.cdp.com
[10]http://www.toolsthatwork.com
[11]Some file viewing programs alter last accessed date-time stamps and should not be used on the original disk.
[12]http://www.accessdata.com
[13]http://www.sleuthkit.org
EAN: 2147483647
Pages: 279