10.4 Data Recovery
10.4 Data Recovery
Although automated tools are necessary to perform routine forensic examination tasks efficiently, it is important to understand the underlying process to explain them in court or perform them manually in situations where the tools are not suitable. There are two main forms of data recovery in FAT file systems: recovering deleted data from unallocated space and recovering data from slack space.[14]
Recently deleted files can sometimes be recovered from unallocated space by reconnecting links in the chain as described in Section 10.2. For instance, to recover the deleted file named "greenfield.doc" on the aforementioned floppy diskette it is necessary to modify its entry in the root directory, replacing the sigma ("σ") with an underscore ("_") as shown here. The sigma is used on FAT file systems to indicate that a file is deleted. Notably, this recovery process must be performed on a copy of the evidentiary disk because it requires the examiner to alter data on the disk.
Name .Ext ID Size Date Time Cluster 76 A R S H D V _REENF~1 DOC Erased 19968 5-08-03 2:34 pm 275 A - - - - -
Then it is necessary to observe that the file begins at cluster 275 and its size is the equivalent of 39 clusters (19,968 bytes 512 bytes/cluster = 39 clusters). Assuming that all of these clusters are contiguous, the FAT can be modified to reconstruct the chain as shown here in bold.
[] Disk Editor Object Edit Link View Info Tools Help 0 0 0 0 0 0 0 0 185 186 187 188 189 190 191 192 193 194 195 196 197 198 199 200 201 202 203 204 205 206 207 208 209 210 211 212 213 214 215 216 217 218 219 220 221 222 223 224 225 <EOF> <EOF> <EOF> 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 276 277 278 279 280 281 282 283 284 285 286 287 288 289 290 291 292 293 294 295 296 297 298 299 300 301 302 303 304 305 306 307 308 309 310 311 312 313 <EOF> 315 316 317 318 319 320 321 322 323 324 325 326 327 328 329 330 331 332 333 334 335 336 337 338 339 340 341 FAT (1st Copy) Sector1 DriveA: Cluster 275, hex 113
Recovering fragmented files is more difficult. When a file was not stored in contiguous clusters, it requires more effort and experience to locate the next link in the chain.
Recovering deleted directories is beyond the scope of this book. The process involves searching unallocated space for an unique pattern associated with directories and is covered in the Handbook of Computer Crime Investigation, Chapter 7, pp. 143–145 (Sheldon 2002). EnCase has a useful utility for automatically recovering all deleted directories (and the files they contained) on a FAT volume.
10.4.1 Windows-Based Recovery Tools
The recovery process described above is time consuming and must be performed on a working copy of the original disk. More sophisticated examination tools like EnCase and FTK can use a bitstream copy of a disk to display a virtual reconstruction of the file system, including deleted files, without actually modifying the FAT. All of these tools recover files on FAT systems in the most rudimentary way, assuming that all clusters in a file are sequential. Therefore, in more complex situations, when files are fragmented, it is necessary to recover files manually. Windows-based tools like EnCase and FTK can also be used to recover deleted files on NTFS volumes.
10.4.2 Unix-Based Recovery Tools
Linux can be used to perform basic examinations of FAT and NTFS file systems as described in Chapter 11. Also, tools like fatback,[15] The Sleuth Kit, and SMART[16] can also be used to recover deleted files from FAT file systems. For instance, the following shows fatback being used to recover a deleted file from a FAT formatted floppy diskette.
examiner1% fatback -l biotechx.log hunter-floppy.dd Parsing file system. / (Done) fatback> dir Sun Apr 13 15:36:52 2003 0 SALES Sun May 13 11:58:10 2003 21504 SKIWAY~1.DOC skiways- getafix.doc Sun May 13 12:40:48 2003 122 TODO.TXT todo.txt Sun May 13 12:42:18 2003 122 NEWADD~1.TXT newaddress.txt Sun May 8 14:34:16 2003 19968 ?REENF~1.DOC greenfield.do Sun May 8 14:41:44 2003 0 ?PRIL/ april Sun Feb 18 12:49:16 2001 16896 CONTACTS.XLS contacts.xls fatback> copy greenfield.do /e1/biotechx/recovered
The contents of a deleted file named "greenfield.doc" was extracted and saved into a file named "/e1/biotechx/recovered" using the copy command within fatback. The Sleuth Kit, combined with the Autopsy Forensic Browser, can be used to examine FAT file systems through a Web browser interface and recover deleted files as shown in Figure 10.5.
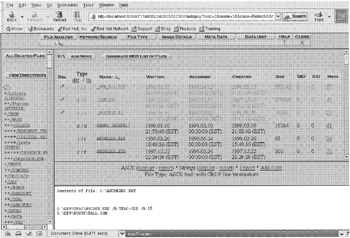
Figure 10.5: The Sleuth Kit and Autopsy Forensic Browser being used to examine a FAT file system (checkmarks indicate files are deleted).
The Sleuth Kit and Autopsy Forensic Browser enable examiners to examine data at the logical and physical level and can also be used to recover files from NTFS file systems. The Sleuth Kit can also be used to recover slack space from FAT and NTFS systems using "dls -s". Although SMART has a feature to recover deleted files from FAT and NTFS volumes, it does not display them in a logical view, making the recovery process somewhat cumbersome.
10.4.3 File Carving with Windows
Another approach to recovering deleted files is to search unallocated space, swap files, and other digital objects for class characteristics such as file headers and footers. Conceptually, this process is like carving files out of the blob-like amalgam of data in unallocated space. File carving tools such as DataLifter (Figure 10.6) and Ontrack's Easy-Recovery Pro (Figure 10.7) can recover many types of files including graphics, word processing, and executable files. Also, user defined files can be carved using WinHex "File Recovery by Type" feature or EnCase E-scripts available from the EnScript library.[17] Specialized tools like NTI's Graphics Image File Extractor also exist to extract specific types of files. Some of these tools can extract images from other files such as images stored in Word documents.
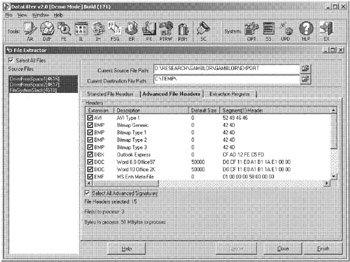
Figure 10.6: DataLifter being used to carve files from two blobs of unallocated space and one blob of file slack from a system.
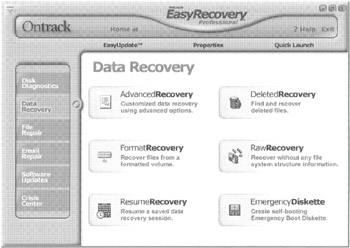
Figure 10.7: Easy-Recovery Pro from Ontrack.
One of the main limitations of these tools is that they generally rely on files having intact headers. Therefore, when file headers have been obliterated, it may be necessary to search for other class characteristics of the desired files and piece fragments together manually. Even when it is not possible to piece recovered fragments together, it may be possible to extract useful information from them. For instance, cluster 37 of the aforementioned floppy disk contains a Word document fragment with Windows date-time stamps from April 14, 2003, at around 0800 hours, shown here in bold.
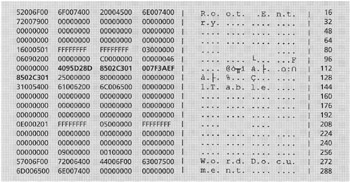
Slack space contains fragments of data that can be recovered but that can rarely be reconstituted into complete files. However, if a small file overwrote a large one, it may be possible to recover the majority of the overwritten file from slack space. It is easiest to recover textual data from slack space because it is recognizable to the human eye. Figure 10.8 shows remnants of a shopping cart on CD Universe in slack space.
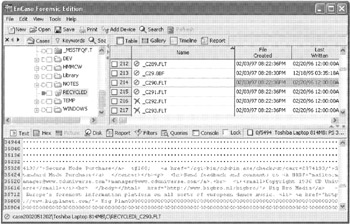
Figure 10.8: File slack of a recovered file viewed using EnCase.
Interestingly, the slack space shown in Figure 10.8 is associated with a deleted file that was recovered.
10.4.4 Dealing with Password Protection and Encryption
It is generally acceptable, and usually desirable, for digital investigators to overcome password protection or encryption on a computer they are processing. In some instances, it is possible to use a hexadecimal editor like Winhex to simply remove the password within a file. There are also many specialized tools that can bypass or recover passwords of various files. For instance, NTI sells a collection of password recovery tools that they have validated.[18] Other companies such as Lostpassword.com[19] sell password bypassing programs. Free, unvalidated tools are available from Russian Password Crackers[20] and other Web sites.
When performing a functional reconstruction using a restored clone of a Windows NT/2000/XP system, it may be necessary to bypass the logon password using a program like ntpasswd,[21] or ERD Commander.[22] In situations where the actual password is needed, tools like LC4[23] (formerly L0pht Crack) are available that attempt to guess passwords in Windows NT password files. Other tools are available to recover passwords for Windows 95/98 systems, dial-up accounts, and other programs that store passwords in PWL files.
The most powerful and versatile password recovery programs currently available are PRTK and DNA from Access Data. The Password Recovery Toolkit can recover passwords from many file types and is useful for dealing with encrypted data. Also, it is possible for a DNA network to try every key in less time by combining the power of several computers. Access Data's Distributed Network Attack (DNA) application can brute force Adobe Acrobat and Microsoft Word/Excel files that are encrypted with 40-bit encryption. Using a cluster of approximately 100 off-the-shelf desktop computers and the necessary software, it is possible to try every possible 40-bit key in 5 days. For example, the Wall Street Journal was able to decrypt files found on an Al Qaeda computer that were encrypted using the 40-bit export version of Windows NT Encrypting File System (Usborne 2002).
However, Microsoft Windows EFS generally uses 128-bit keys (Microsoft 2001) and because each additional bit doubles the number of possibilities to try, a brute force search quickly becomes too expensive for most organizations or simply infeasible, taking million of years. Therefore, before brute force methods are attempted, some exploration should be performed to determine if the files contain valuable evidence and if the evidence can be obtained in any other way. It may be possible to locate unencrypted versions of data in unallocated space, swap files, and other areas of the system. Alternatively, it may be possible to obtain an alternative decryption key. For instance, Encrypted Magic Folders[24] advises users to create a recovery disk in case they forget their password. In one investigation, finding this disk enabled the digital evidence examiner to decrypt data that none of the above mentioned tools could recover.
Similarly, when EFS is used, Windows automatically assigns an encryption recovery agent that can decrypt messages when the original encryption key is unavailable (Microsoft 1999). In Windows 2000, the built-in Administrator account is the default recovery agent (an organization can override the default by assigning a domain-wide recovery agent provided the system is part of the organization's Windows 2000 domain). Notably, prior to Windows XP, EFS private keys were weakly protected and it was possible to gain access to encrypted data by replacing the associated NT logon password with a known value using a tool like ntpasswd and logging into the system with the new password.
[14]A full discussion of recovering lost or hidden partitions is beyond the scope of this text. EnCase, gpart and testdisk (see Chapter 11) can be used to recover partitions on disks with incorrect or damaged partition tables.
[15]http://sourceforge.net/projects/biatchux/
[16]http://www.asrdata.com
[17]http://www.encase.com/support/escript_library.shtml
[18]http://www.forensics-intl.com/breakers.html
[19]http://lostpassword.com/
[20]http://www.password-crackers.com/crack.html
[21]http://home.eunet.no/~pnordahl/ntpasswd/
[22]http://www.winternals.com/products/repairandrecovery/erdcommander2002.asp
[23]http://www.atstake.com/research/lc/
[24]http://www.pc-magic.com/
EAN: 2147483647
Pages: 279