Spectrum Reuse
Spectrum Reuse
The wireless spectrum is limited wireless is like having one invisible cable in the sky that the whole world has to share. This is one of the major limitations of wireless, and we need techniques for efficiently using the spectrum that we do have. There are several methods for reusing spectrum.
The first step is to apply space division; you carve up the service area into smaller coverage areas. The key purpose of space division is to reuse frequencies across the coverage areas, or cells. The second step is to apply a multiple access technique, to allow the sharing of spectrum by multiple users. After you have delineated the space and combined multiple conversations onto one channel, you can then apply spread spectrum, duplexing, and compression techniques to use the bandwidth even more efficiently.
Space Division
The cellular concept involves subdividing coverage areas. Mobile telephony is not a new invention. It has been around since the early 1950s, but at that time, two things limited its availability to the mass market. First, we were using very high-powered antennas. So, when we relayed a signal, it would have strength over a coverage area of perhaps 100 miles (161 kilometers) in diameter. Second, at that time, the spectrum management agencies issued very few frequencies (perhaps a dozen or two) that could be used for purposes of mobile communications. In a relatively large coverage area of 100 miles (161 kilometers) or so, only 12 channels to 24 channels were available. The majority of these few channels were reserved for critical services, such as police and other emergency services, as well as for those who could afford a body builder to carry those big phones that operated at low frequencies over long stretches.
In the 1970s, two things changed. The first was the advent of the low-power transmitter receiver tower, which reduced the coverage area to a cell size that was only about 8 miles (13 kilometers) in diameter. Second, the regulatory agencies made available large amounts of spectrum for use in support of mobile communications, and depending on where you were in the world, anywhere from 600 to 1,000 channels were made available to service providers.
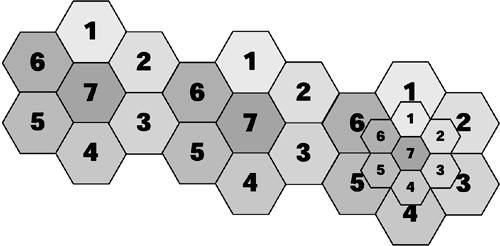
The cellular architecture depends on cells organized into a reuse pattern. In the traditional analog cellular network, the cellular reuse pattern is n=7, and is often depicted as a honeycomb configuration of what are called seven cells (see Figure 14.1). The idea of spectrum reuse is that you can reuse frequencies, as long as they are not in adjacent cells. Say that in the honeycomb configuration, 700 channels are available. Each of the cells could make use of 100 of those channels. We could then reuse those 100 channels in the next honeycomb configuration, as long as those channels were not adjacent to one another between cells.
Figure 14.1. Providing channels by subdividing space into cells
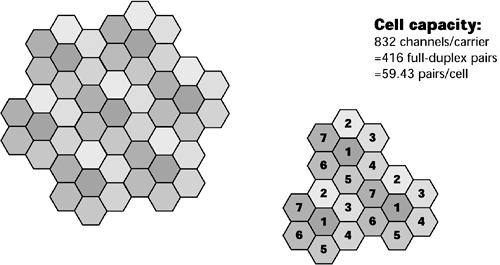
As the density of subscribers increases, the next step is to subdivide the cells into smaller coverage areas, based on accepted reuse patterns. The traditional analog cellular network uses macrocells (see Figure 14.2). This network was for fast-moving users, traveling distances of miles on their end-to-end journey. The coverage area was about 8 miles (13 kilometers) in diameter, and the base station power was rather great generally 10 watts or more. This network offered low deployment costs and a small number of handoffs. Depending on how many channels the spectrum agency gave the region, a cell could support up to about 60 users.
Figure 14.2. An AMPS example of a cellular reuse pattern (n = 7)
As the demand for use increased, we started to migrate toward a microcell architecture. Users of this architecture were assumed to be moving more slowly than those in a macrocell approach; they were, for example, people trapped in a traffic grid, people on golf carts on a golf course, people riding bicycles in Amsterdam, pedestrians anywhere. These users traveled distances of less than 1 mile (1.5 kilometers) end to end. Therefore, there are not as many hand-offs involved with microcells as there are with macrocells. With macrocells and high-speed vehicles, in 1980, when processing power was significantly less than it is today, if you were moving very rapidly through cell boundaries, there would be undue strain on the processing power of the systems, and calls might be dropped. But by the time microcells started to come about, hand-offs were facilitated by more rapid processing. The coverage area of a microcell is about 0.6 miles (1 kilometer) in diameter. Compared to macrocells, this architecture offers better frequency reuse, lower power, and better battery life, as well as smaller subscriber units.
The demand for spectrum is growing beyond what even the microcell design can provide, and so we are now going to the picocell the tiny cell architecture. This approach is for stationary or very slow-moving users the folks who dash out of a seminar during the conference and go stand by a window so they can conduct a conversation. Users are not traveling great distances, maybe 330 to 1,000 feet (100 to 300 meters) end-to-end. The coverage radius of a picocell is only about 150 feet (46 meters), and because it's such a small coverage area, the base station power is also very small 10 milliwatts or less. Therefore, the picocell design offers even better frequency reuse, even lower power, even smaller subscriber units, and even better, longer battery life than microcells. The picocell architecture does create some concerns in the engineering realm; for example, Tokyo needed to plan how to implement more than 40,000 cells for its Personal Handyphone System (PHS) deployment. There are tradeoffs with the various designs: You can serve greater densities with the picocell design than with other designs, but at the cost of a bigger engineering project.
Multiple Access Techniques
There are three major multiple access techniques: Frequency Division Multiple Access (FDMA), Time Division Multiple Access (TDMA), and Code Division Multiple Access (CDMA). The following sections describe the multiple access techniques that are used to make efficient use of the bandwidth within each cell of the cellular system.
FDMA
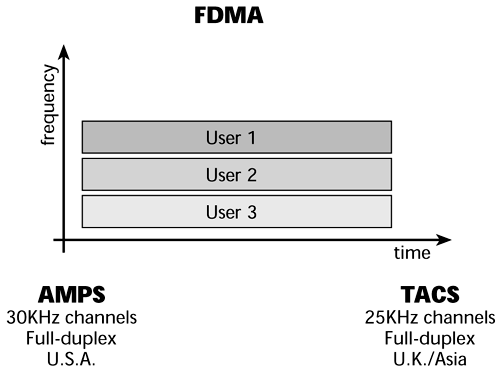
FDMA is used in analog cellular systems, and each user is assigned to a different frequency. With FDMA, everybody is speaking at the same time, but each conversation is on a different portion of the frequency band. FDMA is characterized as facilitating what would today be called low capacity approximately 60 users per cell. Current forecasts suggest that there will be 1.5 billion wireless users worldwide by 2005, and FDMA will not be able to handle the future volume.
The cost of FDMA handsets is low, as these are not smart devices. For example, an FDMA-based device does not know how to search for another frequency that has a better transmission quality associated with it. This approach is inexpensive for the user, but the service operator needs to have a transceiver for each channel, which means the base station cost is high. And because it's an analog technology, FDMA also consumes a great deal of power, and the cost associated with the power consumption is greater than with digital systems.
The advantage of FDMA is that it doesn't need strict clocking devices to enable synchronization between the base stations, as would, for example, TDMA. As Figure 14.3 shows, everybody uses the system at the same time, but each user is working off a different frequency.
Figure 14.3. FDMA
TDMA
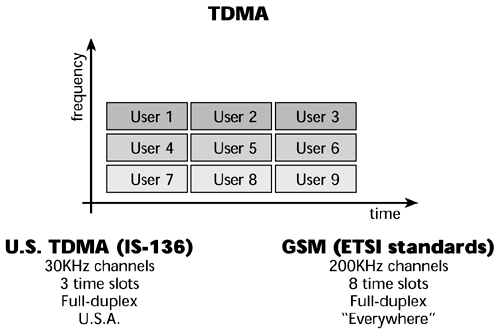
TDMA is used in digital cellular and PCS systems. It is actually a combination of Frequency Division Multiplexing (FDM) and Time Division Multiplexing (TDM). With TDMA, you first divide the available or allocated frequency spectrum into a number of channels. Then, within each channel, you apply TDM to carry multiple users interleaved in time. Therefore, one transceiver can support multiple channels. There are various cellular network standards based on TDMA, including GSM (Global System for Mobile Communications), UWC (Universal Wireless Communications), and JDC (Japanese Digital Cellular). UWC TDMA technology, also referred to as ANSI-136, provides a three-to-one gain in capacity compared to analog technology. Each caller is assigned a specific time slot for transmission. In GSM, eight users per channel are supported. These standards are discussed in further detail later in this chapter.
The digital handsets associated with TDMA are more intelligent than those used with FDMA. For example, they have scanning capabilities, and if the channel you are on is encountering anomalies that are lending themselves to transmission errors, the handset can search for an available channel that provides a better performance.
The key benefits of TDMA are that it offers greater capacity and spectral efficiency than FDMA.
Figure 14.4 shows that in TDMA, everybody is talking on the same frequencies but at different moments in time. The users perceive their conversations as being continuous, even though they are actually getting very rapid samples of that conversation.
Figure 14.4. TDMA
CDMA
CDMA is a multiple-access technique that is receiving a great deal of attention. In CDMA, everybody is using the same frequency at the same time. This is referred to as universal frequency reuse (see Figure 14.5). CDMA provides the ultimate in terms of the density that you can support, and it is possible because each conversation is uniquely encoded. In CDMA, a single spectrum of bandwidth is available for all the users. As Figure 14.6 shows, in CDMA everybody is using the same frequencies at the same time, but each conversation is uniquely encoded, allowing the transceiver to pick it out from among all the conversations.
Figure 14.5. CDMA frequency reuse
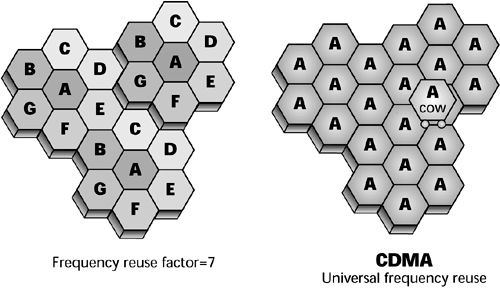
Figure 14.6. CDMA
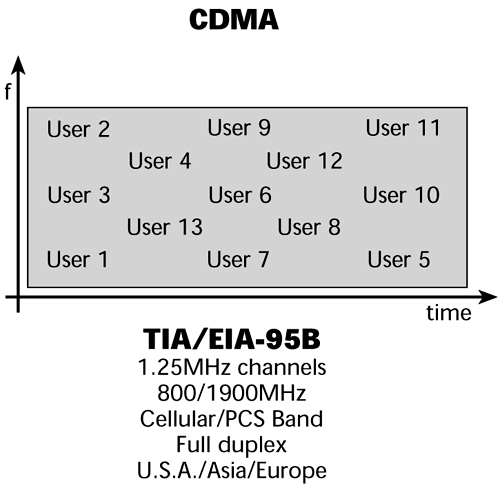
There are two generations of CDMA. First-generation CDMA operates in an allocation of 1.25MHz, and the standard specifications for this version basically emanated from Qualcomm. The second generation of CDMA is Wideband CDMA (WCDMA), which operates over allocations of either 5MHz, 10MHz, or 15MHz, and was created by Oki and Interdigital. As is implied by the name, WCDMA can support higher data rates than can first-generation CDMA. Both generations of CDMA use a unique code for each conversation, and both use a spread-spectrum technique. Advantages of WCDMA include its use of a bigger channel than CDMA, which means that it can carry more calls and that those calls can be encoded in longer strings. The longer strings, in turn, mean greater security and better performance.
CDMA is characterized by not requiring any timing coordination, so clocking is not necessary. It offers great reliability because it is highly resistant to interference. CDMA has greatly improved capacity over FDMA and TDMA; the spectral efficiency of CDMA, as standardized in IS-95, is 10 to 20 times greater than that of an analog network. The number of users who can be serviced depends on the location of the users how many of them are within a given cell and what signal-to-noise ratio the service provider deems acceptable. CDMA allows for two compression ratios for digitized voice, and they're variable according to the channel quality: 13Kbps, which is used to provide near-LAN-line voice qualities (for instance, in support of something like wireless local loop), and 8Kbps, which is used when you want to maximize the use of the spectrum and extend battery life. It is important to realize that CDMA requires complex power control schemes, and power control is very important in CDMA.
CDMA's Military HistoryThe glamorous movie star Hedy Lamarr and George Antheil held the original patent on CDMA technology. Hedy Lamarr had strong personal sentiments against the war. She had recently escaped from her first husband Fritz Mandl, who was one of Europe's largest armaments manufacturers and selling munitions to Hitler. As his wife, Lamarr was exposed to military technology ideas. Lamarr met George Antheil, who had been at the forefront of experimental music in the 1920s, at a party in Hollywood. Antheil was one of the first people to work with the player piano as an instrument for composed music; his famous Ballet Mecanique was written for 12 player pianos, an airplane propeller, and a symphony. Antheil also opposed the Nazis, and it was in this context that Lamarr told Antheil about her idea for a secret communications system that could guide torpedoes to their target without being intercepted by the enemy, by sending messages between transmitter and receiver over multiple radio frequencies in a random pattern. The only problem was how to ensure that the transmitter and receiver would stay in synchronization as they moved through the frequencies. Lamarr thought Antheil could help solve the synchronization problem. Antheil did come up with a solution: Paper rolls perforated with a pseudorandom pattern would delineate the frequency path. Two rolls with the same pattern would be installed in the transmitter and receiver. If the two rolls were started at the same time, and one stayed at the launch point while the other was launched with the torpedo, you'd maintain the synchronization right on down to where the torpedo hit the ship. Interestingly, Lamarr and Antheil designed their system to use 88 frequencies exactly the number of keys on a piano just like the player piano rolls in Ballet Mecanique. (There is more to this fascinating story. For a full account, go to www.siriuscomm.com/lamarr.htm.) Today, we call this technique Frequency Hopping Spread Spectrum (FHSS), and it is one of the ways in which CDMA uniquely encodes its conversations. Along with FHSS, we also now rely on a newer and better technique for transmitting messages securely and with great resistance to noise, Direct Sequence Spread Spectrum (DSSS). |
Spread Spectrum Techniques
There are two spread spectrum techniques: FHHS and DSSS. With FHHS, which is the older of the two methods, the frequency hopping varies in a known pattern, and separate error correction must be included (see Figure 14.7). Slow frequency hopping is used to combat fading. Today, we predominantly rely on DSSS, in which each data bit is converted to a series of 10 transmitted bits to 144 transmitted bits, or chips. DSSS requires greater bandwidth than does FHHS, but this is exactly what makes its performance so good.
Figure 14.7. FSSS
Power Control Schemes in TDMA and CDMAThe classic example that instructors give their students when talking about wireless is the following: You walk into a TDMA cocktail party, and a group of people stands in a circle. Each person takes a turn at making a comment or answering a question. You can separate the conversations by the moment in time when each individual is speaking. You walk into a CDMA party, and you feel as though you've walked into the United Nations. There's German in the left-hand corner, Japanese in the right-hand corner, and English in the center. Somebody says a word in your language that you recognize, and you immediately focus your attention there. You're able to filter out the extraneous conversation as noise because you've tuned in on a code that's understandable to you. You can continue to filter out the extraneous conversation, unless another 200 delegates walk in and add their conversations to the overall mix, making it impossible for you to distinguish between the conversations. |
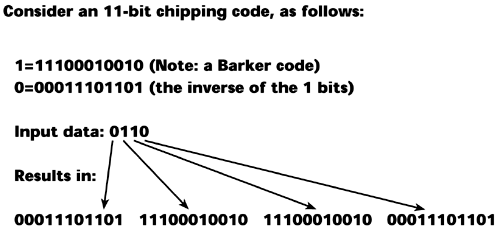
Figure 14.8 shows an example of DSSS that uses the Barker Code, which is an 11-bit chipping code. The 1-bits are encoded as a particular sequence of ones and zeros, and the 0-bits are the inverse of that sequence. In the course of a transmission, if a bit is affected by noise and several chips get knocked out, the receiver can determine from the pattern of remaining bits whether a one or a zero got knocked out and recover that information accurately. This is why DSSS provides such good performance and resistance to interference and noise. DSSS also provides great reliability because the DSSS operation generates more bits per second than it starts with, and the resulting signals spread over a wide range of frequencies when it is transmitted, minimizing the impact of interference and multipath fading.
Figure 14.8. A DSSS example
Duplexing Techniques
Another way in which the operations of wireless networks differ, and hence also the standards differ, is the duplexing technique the procedure for separating the incoming and outgoing conversations. There are two duplexing techniques:
Frequency Division Duplex (FDD) FDD is a full-duplex approach. It is used when there is a significant contiguous spectrum allocated and when synchronization between the base stations is not possible. With FDD, each direction (incoming and outgoing) occupies a different portion of the frequency band, and a rather large portion of the spectrum is consumed.
Time Division Duplex (TDD) TDD is a half-duplex technique sort of a Ping-Pong approach. Each end of the conversation makes use of the same frequency, but this requires very tight timing coordination, so there's a trade-off. Where spectrum is an issue and where you want to conserve on how you utilize the spectrum, TDD is more efficient than FDD.
Compression Techniques
After you have carved space into cells and applied multiple access techniques within each cell to make better use of the bandwidth available in that area, you need to apply compression to make greater use of the bandwidth within each given channel. Compression is very important because it improves the use of a very precious resource, the communications channel.
Voice compression techniques use voice coders/decors (vocoders), of which there are two general types:
High-bit-rate vocoders These vocoders are used by PCS, wireless local loops, and wireless office telecommunication systems applications. These vocoders carry voice by using 32-Kbps Adapted-Differential Pulse Code Modulation (ADPCM). A bit rate this high emulates the quality that you achieve on the public switched telephone network (PSTN), and no additional error detection and correction is necessary.
Low-bit-rate vocoders These vocoders are used in cellular systems that deal with vehicular traffic, where there are large cells and you need to facilitate a large number of conversations. These vocoders reduce the voice to 8Kbps, by using extensive channel coding techniques that help facilitate error correction, such as Line Pulse Coding (LPC), Quantized Code-Excited Linear Predictive (QCELP), or Vector Sum Excited Linear Prediction (VSLEP). GSM uses Regular Pulse Excitation Long-Term Prediction (RPE LTP), which carries digitized voice at 13Kbps, achieving good voice quality.
In the realm of data, unfortunately, there are no set standards for data compression; many techniques exist, and, overall, data compression is underused.
EAN: 2147483647
Pages: 84