Chapter 4: Understanding Windows Server 2003 Integration
In the last two chapters, you learned about the storage and routing architectures in Microsoft Exchange Server 2003. This chapter builds on that knowledge by describing how Exchange Server 2003 integrates with Microsoft Windows Server 2003 and how it uses the services in Windows Server 2003 to its advantage. We’ll begin with a brief overview of the Windows Server 2003 Active Directory directory service and then finish the chapter by describing how Exchange Server 2003 uses Active Directory and discussing some of the more important Internet information protocols.
| Note | In various parts of this chapter, we will compare Exchange 2003 Server with Exchange 5.5 Server because at the time of this writing, a large Exchange 5.5 install base remains, and many users will be upgrading directly to Exchange 2003 Server, bypassing Exchange Server 2000. If you’ve been running Exchange 2000 Server, you can skip those parts that discuss Exchange 5.5. |
Brief Overview of Active Directory
A full explanation of Active Directory is outside the scope of this book but a brief overview is warranted. Because Exchange Server 2003 is heavily dependent on the underlying network operating system, it is important to have a basic understanding of Windows Server 2003 Active Directory.
| More Info | For a more thorough discussion of Active Directory and the other concepts discussed in this chapter, see Microsoft Windows Server 2003 Administrator’s Companion, by Charlie Russel, Sharon Crawford, and Jason Gerend (Microsoft Press). |
Directory Structure in Active Directory
Before we discuss what Active Directory is, you should first understand what a directory is. As an analogy, think of a generic file system. Perhaps in this file system, you have a C: drive, and on that drive, you have a root folder named Memos. Under C:\Memos, you have a folder for each of the 12 months of the year, so you would find a folder in the structure named July. Under C:\Memos\July, you have a folder named Departments; the full pathname to Departments is C:\Memos\July\Departments. This is a hierarchy of folders in a file system.
A directory is no different from a folder list, except that the hierarchy consists not of folders but of objects. An object is an entity that is described by a distinct, named set of attributes. Instead of using Windows Explorer to search through this hierarchy of objects, we’ll be using a protocol designed to search a directory, called the Lightweight Directory Access Protocol (LDAP).
| Note | The original protocol for accessing a directory was called Directory Access Protocol (DAP), but it had a high overhead and tended to be slow. Lightweight Directory Access Protocol (LDAP) is an improved version that is faster and requires less overhead. For more information about the LDAP protocol, see Chapter 20, “Supporting Internet Protocols and SMTP.” |
With Active Directory, Microsoft has made significant improvements to the directory concept, such as dynamic DNS. The “Active” in Active Directory describes the flexibility and extensibility that has been built into Microsoft’s directory service.
Logical Structure of Active Directory
The components that form the logical structure of Active Directory include domains, organizational units, trees, and forests.
Domains
A domain is the core unit in Active Directory and is made up of a collection of computers that share a common directory database. The computers that share this common directory database are called domain controllers. A domain controller is a Windows Server 2003 server that has Active Directory installed. It is able to authenticate users for its own domain. Each domain controller holds a complete replica of the domain naming partition for the domain to which it belongs and a complete replica of the configuration and schema naming partitions for the forest. Dcpromo.exe is the utility used to promote a Windows Server 2003 server to a domain controller. We’ll discuss these partitions later in this chapter.
All Active Directory domain names are identified by a DNS name as well as by a NetBIOS name. The following is an example of the two types of names:
DNS-style domain name: sample.microsoft.comNetBIOS name: SAMPLE
Generally, the NetBIOS name is the same as the first naming component in the DNS name. However, a NetBIOS name can be only 15 characters in length, whereas each name in the DNS naming convention can have up to 64 characters. During installation, both names can be configured to meet your needs. In the initial release of Windows Server 2003, Active Directory names cannot be changed.
The domain is also a security boundary in Active Directory. Administrators in a domain have the permissions and rights to perform administrative functions in that domain. However, since each domain has its own security, administrators must be given explicit permissions to perform administrative tasks in other domains. Members of the Enterprise Admins group have rights to perform administrative tasks in all domains across the forest. Hence, you can have domain administrators and a higher level of administration from the Enterprise administrators.
A Windows Server 2003 Active Directory domain can be in either mixed mode or native mode. The default installation is mixed mode. In mixed mode, a Windows Server 2003 domain controller acts like a Microsoft Windows NT 4 domain controller. Active Directory domains in mixed mode have the same limitations on the security accounts database as Windows NT 4 domain controllers. For example, in mixed mode, the size of the directory is limited to 40,000 objects, the same restriction imposed by Windows NT 4. These limitations allow Windows NT 4 backup domain controllers to exist on the network and connect to and synchronize with the Windows Server 2003 domain controllers.
The PDC Emulator is one of the five Flexible Single Master Operation (FSMO) roles that makes the Windows Server 2003 look like a Windows NT 4 PDC. Only one Windows Server 2003 domain controller can act as the PDC Emulator. By default, the PDC Emulator role, like all other FSMO roles, is installed on one domain controller in each domain, by default, on the first domain controller of each domain. (We will discuss the FSMO roles in just a moment.) To run Windows Server 2003 in native mode, you must not have any reason or desire to connect to a Windows NT 4 backup domain controller. In other words, when you decide to run Windows Server 2003 in native mode, you won’t be able to use a Windows NT backup domain controller again on your network, and no applications running on your network will be able to use Windows NT to operate. The switch to native mode is a one-time, one-way switch and is irreversible. Native mode allows your Windows Server 2003 domain controllers to have millions of objects per domain. In addition, native mode allows the nesting of groups, something that is advantageous if you anticipate large distribution groups in Exchange Server 2003.
A Windows Server 2003 network running in native mode can accommodate Windows NT 4 stand-alone and member servers. Windows NT 4 workstations must be upgraded to Windows Server 2003 Professional to participate in Active Directory, or you must install the Directory Service Client. Windows Server 2003 implements Active Directory in a multimaster model because objects in Active Directory can be modified on any domain controller, which accounts for the emphasis on directory replication between domain controllers. However, some roles are either too sensitive to security issues or too impractical to perform in a multimaster model because of potential conflicts that could arise from the replication traffic. An understanding of these roles is important; if a domain controller that is performing a particular role becomes unavailable, the function it performed will not be available in Active Directory. These roles are schema master, domain naming master, relative identifier master, PDC emulator, and infrastructure master.
Schema Master The schema is the set of object classes (such as users and groups) and their attributes (such as full name and phone number) that form Active Directory. The schema master controls all aspects of updates and modifications to the schema. To update the schema, you must have access to the schema master. There can be only one schema master in the forest at any given time.
Domain Naming Master The domain naming master controls the addition and removal of domains in the forest. This is the only domain controller from which you can create or delete a domain. There can be only one domain naming master in the forest at any given time.
Relative Identifier Master The relative identifier (RID) master allocates sequences of RIDs to each of the domain controllers in its domain. Whereas the schema master and domain naming master perform forestwide functions, one RID master is assigned per domain. Since each domain controller can create objects in Active Directory, the RID master allocates to each domain controller a pool of 500 RIDs from which to draw when creating the object. When a domain controller has used more than 400 RIDs, the RID master gives it another batch of 500 RIDs.
Whenever a new user, group, or computer object is created, the object inherits the security identifier (SID) of the domain. Appended to the end of the domain SID is the RID, which makes up the unique SID for the object. In addition, when an object is moved from one domain to another, its SID changes, because it receives a new SID (made up of both the domain SID and the RID) in the destination domain. By allowing only the RID master to move objects between domains, Windows Server 2003 ensures SID uniqueness, even across domains. Objects maintain a SID history for security access to resources.
PDC Emulator Each domain in the forest must have one domain controller that acts as the PDC emulator. If Active Directory is running in mixed mode with Windows NT 4 domain controllers on the same network, the PDC emulator is responsible for synchronizing password changes and security account updates between the Windows NT 4 servers and the Windows Server 2003 servers. Moreover, the PDC emulator appears to downlevel clients, such as Windows 95, Windows 98, and Windows NT 4, as the PDC of the domain. It functions as the domain master browser, is responsible for replication services to the BDCs, and performs directory writes to the Windows NT 4 domain security database.
In native mode, the PDC emulator receives the urgent updates to the Active Directory security accounts database, such as password changes and account lockout modifications. These urgent changes to user accounts are immediately replicated to the PDC emulator, no matter where they are changed in the domain. If a logon authentication fails at a domain controller, the credentials are first passed to the PDC emulator for authentication before the logon request is rejected.
Infrastructure Master The infrastructure master is responsible for tracking group-to-user references whenever the user and the group are not members of the same domain. The object that resides in the remote domain is referenced by its GUID and SID. If an object is moved from one domain to another, it receives a new SID, and the infrastructure master replicates these changes to other infrastructure masters in other domains.
Organizational Units
An organizational unit (OU) is a container object that is used to organize other objects within a domain. An OU can contain user accounts, printers, groups, computers, and other OUs.
| More Info | The design of Active Directory is based on the X.500 standard, which can be procured from www.itu.org. The standard is rather short— around 9 pages—but reading it will give you a great background for understanding Active Directory and, for that matter, Novell Directory Services. |
OUs are strictly for administrative purposes and convenience. They are transparent to the user and have no bearing on the user’s ability to access network resources. OUs can be used to create departmental or geographical boundaries. They can also be used to delegate administrative authority to users for particular tasks. For instance, you can create an OU for all of your printers and then assign full control over the printers to your printer administrator.
OUs can also be used to limit administrative control. For instance, you can give your help desk support personnel the permission to change the password on all user objects in an OU without giving them permissions to modify any other attributes of the user object, such as group membership or names.
Because an Active Directory domain can hold millions of objects, upgrading to Windows Server 2003 allows companies to convert from a multiple-domain model to a single-domain model and then use organizational units to delegate administrative control over resources.
Trees and Forests
The first Windows Server 2003 domain that you create is the root domain, which contains the configuration and schema for the forest. You add additional domains to the root domain to form the tree. As Figure 4-1 illustrates, a tree is a hierarchical grouping of Windows Server 2003 domains that share a contiguous namespace. A contiguous namespace is one that uses the same root name when naming additional domains in the tree.
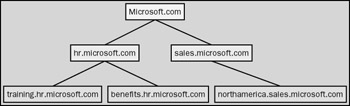
Figure 4-1: Fictitious tree of Microsoft.com.
A collection of trees that do not share a contiguous namespace can be placed in the same forest. They then share a common configuration, schema, and Global Catalog (GC). By default, the name of the root domain becomes the name of the forest, even though other trees will not share the same name as the root domain.
Even though they don’t share the same name, transitive trust relationships are automatically established between the root domain servers in each tree, as long as they are members of the same forest. Figure 4-2 shows two trees, Microsoft.com and trainsbydave.com, in the same forest.
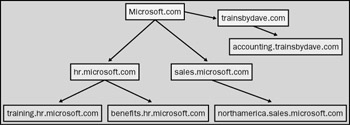
Figure 4-2: Forest consisting of Microsoft.com and trainsbydave.com.
The schema and configuration partitions for Active Directory are replicated to all domain controllers in each domain. Whereas a domain represents a boundary for security and the logical grouping of objects, a forest represents the boundary for Active Directory and the Exchange 2000 organization.
In addition, other domain names cannot be represented above the first domain name. For instance, if your root domain name is hr.trainsbydave.com, you can never install a domain named trainsbydave.com in the same forest. You can join other domain names to the forest, such as microsoft.com, as long as they are in a different namespace.
Groups
Windows Server 2003 enhances the group structure of Windows NT 4. Groups are used to reduce administrative effort and to enable the management of many user accounts simultaneously. Windows Server 2003 uses groups to reduce the number of objects that require direct administration.
There are basically two kinds of groups in Windows Server 2003. Each has its own advantages and restrictions that you must take into account when using them. Exchange Server 2003 uses both kinds of groups from Windows Server 2003:
-
Security groups Security groups host security principles within Active Directory. They are used to group users or computers for the purpose of reducing the points of administration and providing permissions to network resources.
-
Distribution groups Distribution groups are meant to perform distribution functions. In cooperation with Exchange Server 2003, these groups are the replacement for distribution lists in Exchange 5.5. You cannot use them to assign permissions to network resources.
Global Groups Global groups, in mixed mode, can contain users only from the domain in which they are hosted. In native mode, they can contain users and global groups from the local domain in which they were created. However, they can be used to assign permissions to resources in any domain. Global groups can contain users, computers, and global groups from the local domain. They can be members of any other type of group.
Typically, you’ll use global groups for administering user membership that has permissions to a network resource. The group itself is replicated as part of the Global Catalog, but its membership is not. This restriction means that adding user accounts to or removing user accounts from a global group will not trigger a new replication of the Global Catalog. Global groups can be converted to universal groups (discussed shortly) as long as the global groups do not contain other global groups and the domain is in native mode.
Domain Local Groups Domain local groups in native mode can contain other domain local groups, users, global groups, and universal groups from any domain in the forest, but they can be granted permissions only in the domain in which they reside. In mixed mode, they can contain only user and global group accounts.
You’ll grant permissions to domain local groups only for objects in the local domain. The existence of the domain local group is replicated to the Global Catalog server, but its membership is not replicated. Domain local groups are flexible in that you can use any other security principle inside the domain local group (when running in native mode) to reduce administrative effort. You can convert a domain local group to a universal group in native mode as long as it does not contain other domain local groups.
Universal Groups Universal groups can contain users, global groups, and other universal groups from any Windows Server 2003 domain in the forest. The domain must be operating in native mode to create security groups with universal scope. You can grant permissions to resources anywhere in the forest to a universal group.
Universal group membership must be determined at the time of logon. Because the scope of the universal group is universal, this group is propagated through the Global Catalog. Hence, not only is the group itself propagated in the Global Catalog, but its membership is propagated as well. A universal group with a large membership will generate additional replication overhead if the membership changes. Universal groups as security groups are available only in native mode. Table 4-1 summarizes group membership rules.
| Group Scope | In Mixed Mode Can Contain | In Native Mode Can Contain | Can Be a Member Of | Can Be Granted Permissions For |
|---|---|---|---|---|
| Domain local | User accounts and global groups from any domain | User accounts, global groups, and universal groups from any domain in the forest, and domain local groups from the same domain | Domain local groups in the same domain | The domain in which the domain local group exists |
| Global | User accounts | User accounts and global groups from the same domain | Universal and domain local groups in any domain and global groups in the same domain | All domains in the forest |
| Universal | Not applicable | User accounts, global groups, and other universal groups from any domain in the forest | Domain local and universal groups in any domain | All domains in the forest |
EAN: 2147483647
Pages: 254