Branch Office
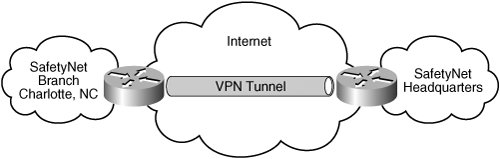
| The SafetyNet Insurance agency is a large company with over 20,000 employees. A majority of the employees are independent agents who pay SafetyNet a franchise fee to be allowed to open a brick-and-mortar storefront. One of the branch offices is located in a strip mall in Charlotte, North Carolina. The office employs 10 agents, 20 support staff, and each has their own computer for a total of 30 desktops. They also have one Windows server that they use for database services and file sharing. A point-to-point VPN over a high-speed Internet connection allows them to transmit paperwork to SafetyNet headquarters. They use the same Internet connection without the VPN for e-mail, web browsing, and so on (see Figure 11-3). Figure 11-3. Initial SafetyNet Network Configuration
If the computers or the Internet connection need repair, they can call the "computer guy" who services all of the SafetyNet offices in the county. His salary is subsidized by SafetyNet, but the office still has to pay him an hourly wage. Plus, the guy is really busy, so it sometimes takes him a few days to get to the office to solve the problem. A few weeks ago, the managers in the office decided to make a major investment in computer security. They had three reasons for the decision:
They hired a computer security consultant to help them. He immediately suggested that IPS could alleviate many of their problems. Limiting FactorsBefore the consultant could get started, the office management made him aware of the limitations under which he had to work. They explained that although the office doesn't have a computer security policy, headquarters has one with specific caveats that apply to all branch offices. A few of the guidelines in the policy appeared to be applicable:
The branch office is prohibited from modifying the operation of the router or VPN in any way. Security Policy GoalsWhen the consultant asked them what their goals for the project were, they listed four:
HIPS ImplementationSafetyNet's consultant used the limiting factors and goals to create an initial HIPS project plan. The plan defined the following:
Target HostsThe headquarters security policy requires that all of the branch office systems run virus protection. IPS falls into the virus protection category, so all hosts are targets for HIPS. Management ArchitectureOne of the limiting factors SafetyNet shared with the consultant is that they don't want to spend much money keeping the HIPS up-to-date. Also, they don't have the expertise to make HIPS configuration changes after the consultant leaves. To address both of these issues, the HIPS is to be managed by a reasonably priced managed security service provider (MSSP). The consultant is to do the initial agent deployment and configuration. Once he is finished, the agents are to be configured to report events and receive security settings from the MSSP's management server. Also, the MSSP delivers weekly status reports to the office manager. Agent ConfigurationHIPS can help address all of SafetyNet's goals. To do so, it will be configured to
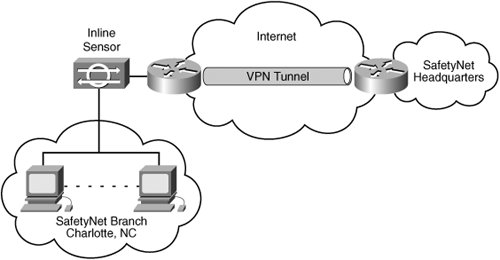
NIPS ImplementationMany of the problems being faced by SafetyNet can be addressed using HIPS. The consultant also decided to utilize NIPS to help minimize the VPN connections from being taken down by headquarters by installing an in-line sensor that drops all virus traffic (using IPS virus signatures) before they leave or enter the Charlotte branch. Sensor DeploymentThe Charlotte branch decides to deploy an in-line NIPS sensor between their network and the VPN router connected to the headquarters. By dropping all known virus-related traffic, they hope to keep the branch VPN operational (even if they have an infected system) while allowing them time to clean the infected system (see Figure 11-4). Figure 11-4. Final SafetyNet Network Configuration
Using an in-line NIPS sensor, the Charlotte branch decides to drop the initial virus traffic (using virus-based signatures) and then block all traffic from the infected host for 24 hours (allowing time for the machine to be cleaned). If the virus is detected over a weekend, the traffic from the infected host is blocked for a longer period of time. NIPS ManagementThe Charlotte office decides that the configuration on their sensor is not going to change very often. Furthermore, their research indicates that the virus-based NIPS signatures are accurate (the false alarm rate is very low). Therefore, the Charlotte branch decides to pay a consultant to initially configure the sensor and update the configuration quarterly. They plan to use the same MSSP that is monitoring their HIPS to manage the NIPS deployment. To test the effectiveness of their in-line sensor, the managers decide to have the consultant configure the NIPS to generate an e-mail to all of the branch managers whenever an infected system is detected. Note The Charlotte deployment goes very well, and infections not detected by HIPS are blocked by the NIPS sensor. Headquarters notices that during the last year, it has never had to drop the Charlotte branch VPN connection because of an infected system. After investigating the Charlotte solution, SafetyNet decides to protect all of its branches in a similar fashion. Instead of deploying in-line sensors at each branch, it decides to deploy the NIPS sensors at the headquarters site. By deploying sensors at the headquarters location, it can decrease costs and management because traffic from all of the branches can be monitored with fewer sensors (a single sensor can handle multiple branches). Furthermore, the in-line sensors enable SafetyNet to modify its security policy to state that all traffic from an infected system will be blocked for 24 hours instead of all traffic from a specific branch, thereby reducing lost business opportunities. |
EAN: 2147483647
Pages: 115