6.2 Using Public Keys for Identification
| only for RuBoard - do not distribute or recompile |
6.2 Using Public Keys for Identification
The identification and authentication techniques mentioned in the first part of this chapter all share a common flaw: to reliably identify an individual, that person must be in the presence of the person or computer that is performing the identification. If the person is not present if the identification is being performed by telephone, by fax, or over the Internet then there is high potential for fraud or abuse because of replay attacks.
6.2.1 Replay Attacks
To understand replay attacks, consider the case of a computer that verifies its user's identity with a fingerprint scanner. Under ideal conditions, a person sits down at the computer, presses his thumb to the scanner, and the computer verifies his identity. But consider the case shown in Figure 6-5, in which one computer acquires the fingerprint and another performs the verification. In this case, it is possible for an attacker to intercept the code for the digitized fingerprint as it moves over the network. Once the attacker has the fingerprint transmission, the attacker can use it to impersonate the victim.
Figure 6-5. When a biometric verification is performed remotely over a computer network, the identification can be compromised by replay attacks (by tampering with the computer or software that measures the biometric).
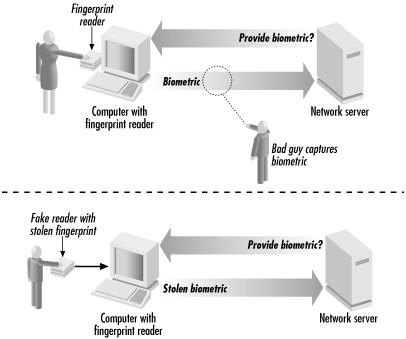
Replay attacks aren't a problem for biometrics alone: they represent a fundamental attack against all of the digital identification systems mentioned in this chapter. For example, passwords can be eavesdropped and re-used by an attacker. Even position-based systems can be attacked with replay attacks.
Simple encryption provides a measure of protection against replay attacks because encryption makes it more difficult for an attacker to intercept passwords, digitized fingerprints, and other kinds of information used to prove identity. But straightforward encryption has an important limitation: although encryption protects the identification information while it is in transit, if the information is ever revealed to a hostile party, then the information is forever compromised!
This is why the practice of banks and credit card companies of using a person's Social Security number and his "mother's maiden name" is so problematic: there is no way for this information to be verified while at the same time keeping it secret, and once the information is no longer secret, it has no value for identification.
6.2.2 Stopping Replay Attacks with Public Key Cryptography
Properly implemented, public key cryptography can eliminate the risk of replay attacks.
In Chapter 3 we saw that public key cryptosystems involve the use of two cryptographic keys: a public key, which is widely distributed, and a private key, which is kept a secret. When public key systems are used for identification, the private key is used to create a signature and the public key is used to verify that signature. As the private key never leaves the possession of the person being identified it never gets sent over the wire there is no opportunity for an attacker to intercept the private key and use it for malicious purposes.
Public key cryptography can be used for either offline authentication or online authentication. In the case of offline authentication, a user creates a digitally-signed message that can be verified at a point in the future. In the case of online authentication, a user authenticates in real time with a remote server.
Offline authentication systems are fairly straightforward:
-
The user creates a message.
-
The user signs the message with his private key.
-
The message and the digital signature are sent to the remote server.
-
At some point in the future, the remote server verifies the digital signature on the message with the user's public key.
Online authentication systems are somewhat more complicated than offline authentication systems because they have more back-and-forth steps:
-
The user's computer makes a connection with a remote server.
-
The remote server sends the user a randomly-generated challenge.
-
The user's computer digitally signs the challenge with the user's private key.
-
The digitally signed challenge is sent back to the remote server.
-
The server verifies the signature with the user's public key.
Because of the challenge-response protocol, online systems are also generally more secure than offline systems.
6.2.2.1 PGP public keys
PGP is a sophisticated cryptographic system for performing public key encryption. Although the original PGP system was designed primarily for encrypting and digitally signing email, today it is used for all kinds of electronic documents. PGP also has facilities for creating and managing cryptographic keys.
You can think of a PGP public key as a kind of identity card. In the original version of PGP, a PGP public key included a person's name and the actual numbers used by the RSA encryption algorithm used for encrypting or signature verification. Newer versions of PGP allow you to add photographs and additional information to your public key. Simson's PGP public key is shown in text form in Figure 6-6, and in graphical form, as displayed in the Windows PGPkeys program, in Figure 6-7.[3] Using the private key that corresponds with the PGP public key shown, he can digitally sign his name so that anyone with his public key can verify his identity.
[3] We won't reproduce Spaf's two keys here, but if you want to increase your confidence in using them, here are the key fingerprints: ID 0xF7AB8D54 is B28E 6E51 7BBF 80CD 0B7A 9074 1ECF E570 F7AB 8D54, and ID 0xFC0C02D5 is 9F30 B7C5 8B52 358A 424B 73EE 55EE C541. See PGP: Pretty Good Privacy (O'Reilly) to understand how to use these values.
Figure 6-6. Simson Garfinkels's PGP public key, in text form

Figure 6-7. Simson Garfinkel's PGP public key, as shown by the Windows PGPkeys program
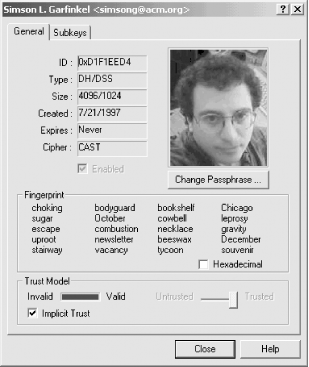
Of course, the fact that Simson Garfinkel's can to create a digital signature that matches a given public key doesn't really prove his identity. When a digital signature is used to "prove someone's identity," identity proving is not precisely what is taking place. Being able to create a valid digital signature doesn't prove you are a particular person: it proves you have possession of a particular private key. That's why it's possible to find keys on the public keyrings purporting to be for Hillary Clinton and Batman.
6.2.3 Creating and Storing the Private Key
For digital signature validation to become identity authentication, several preconditions need to be met:
-
Each private key/public key pair must be used by only one person.
-
The private key must be kept secure, lest it be compromised, captured, and used fraudulently by others.
-
There needs to be some sort of trust mechanism in place, so that the person verifying the identity can trust or believe that the name on the key is in fact the correct name.
If keys are carelessly generated, then it may be possible for an attacker to take a public key and determine the corresponding private key. If keys are not stored properly, then the attacker may simply be able to steal the private key.
While these rules look simple on the surface, in practice they can be exceedingly difficult to implement properly. Even worse, frequently it is difficult to evaluate a company's public key system and decide if it is more secure or less secure than a competing system.
There are a number of different alternatives for creating and storing keys. Roughly in order of decreasing security, they are:
-
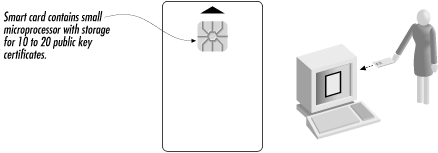
Probably the most secure way to create and use a set of keys is to employ a cryptographic coprocessor such as a smart card.[4] A typical public key-compatible smart card has a small microprocessor with a hardware random number generator for creating keys and performing the basic public key algorithms; it also has a region of memory that can hold the keys and public key "certificates" (see Figure 6-8). In theory, the private key never actually leaves the card. Instead, if you want to sign or decrypt a piece of information, that piece of information has to be transmitted into the card, and the signed or decrypted answer transmitted off the card. Thus, attackers cannot use the private key unless they have possession of the smart card. Smart cards can be augmented with fingerprint readers or other biometric devices, so that the card will not create a signature unless the biometric is presented (see the discussion in Section 6.2.3.2 later in this chapter).
[4] The discussion in this section pertains only to smart cards that contain a microprocessor capable of performing public key cryptography and storing the resultant keys. Most smart cards in use today cannot perform public key cryptography.
Figure 6-8. Using a smart card to store a private key/public key pair.
-
For those who do not wish to invest in special smart cards and smart card readers, another technique to manage private keys is to generate them on a desktop computer and then store the encrypted keys on a floppy disk or flash disk. When the key is needed, the user inserts the floppy disk into the computer's drive; the computer reads the encrypted private key into memory, decrypts the key, and finally uses the key to sign the requested information. This technique is less secure than the smart card because it requires that the private key be transferred into the computer's memory, where it could be attacked and compromised by a computer virus, Trojan horse, or other rogue program.
-
The simplest way to create and store a public key/private key pair is to generate the key inside the computer, then to encrypt the key using a passphrase and store the key in a file on the computer's hard disk. This is the technique that programs such as PGP and Netscape Navigator use to protect private keys. This technique is convenient. The disadvantage is that if somebody gains access to your computer and knows your passphrase, he or she can access your private key. And because the key must be decrypted by the computer to be used, it is vulnerable to attack inside the computer's memory by a rogue program or a Trojan horse.
-
The least secure way to generate a public key/private key pair is to let somebody else do it for you, and then to download the private and public keys. The fundamental problem with this approach is that the private key is by definition compromised: somebody else has a copy of it. Nevertheless, some organizations (and some governments) require that people use third-party key generation for this very reason: so that the organization will have a copy of each user's key, allowing the organization to decrypt all email sent to the individual.
In practice, most cryptographic systems use the third option generating a key on a desktop computer and then storing the key on the computer's hard disk.
6.2.3.1 Creating a public key/private key pair with PGP
To demonstrate the process of creating a public key/private key pair, we can use the popular Pretty Good Privacy encryption program.
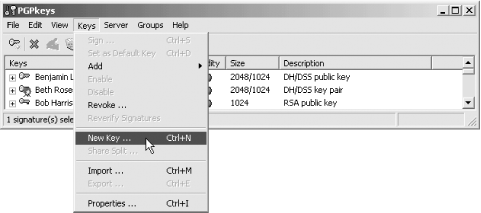
PGP makes it easy to create keys. With the Windows version of the program, simply select the "New Key" option from the "Keys" menu of the PGPkeys applications (Figure 6-9).
Figure 6-9. To create a new PGP key, select the "New Key..." option from the "Keys" menu of the PGPkeys application program
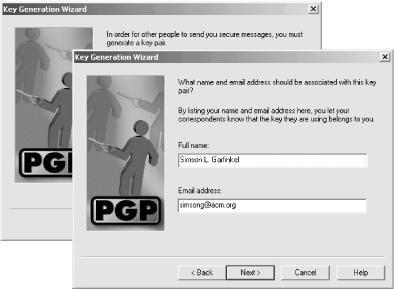
PGP will now display the PGP Generation Wizard (Figure 6-10). Click "Next" and the program will prompt you to enter the name and email address that will be associated with the key.
Figure 6-10. When you run the PGP Key Generation Wizard, you will be prompted to enter your full name and email address. This information is recorded on the key. You can change the full name or email address at a later time, but if you do, you will need to have your key reassigned.
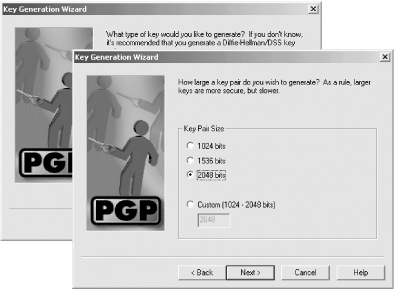
The PGP encryption system supports two kinds of public keys: keys based on the RSA encryption algorithm and keys based on the DSA algorithm. On the next window of the wizard, PGP allows you to choose which kind of key you wish to create, and then the number of bits you wish to have in the encryption key (Figure 6-11). More bits in the key makes the key more secure, but increases the amount of time that it takes to both encrypt and decrypt.
Figure 6-11. After you have given the PGP Key Generation Wizard your name, you will be asked to choose whether you are creating a Diffie-Helman/DSS key or an RSA key. Although PGP recommends that you use a Diffie-Helman key, such keys are not compatible with older versions of PGP. After you choose which algorithm the key will use, you can choose the key's size.
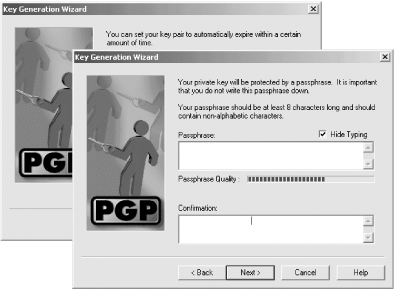
After you have picked the algorithm and the key size, versions of PGP after 6.0 will allow you to pick when the key will expire. Many users choose to have their keys never expire, but some organizations choose to create new keys every year or every few years. After you set the key expiration, PGP asks you to type a passphrase that will be used to encrypt the key once it is created. This is the only protection that PGP provides for your private key: if someone who has access to your encrypted key can guess your passphrase, he can decrypt the key and use it without your permission. Because the passphrase is so important, PGP actually rates your passphrase as you type it by showing the "passphrase quality" (Figure 6-12). Keys with a high "quality" are more difficult to guess. Good passphrases are long, have letters, numbers, and spaces, and are easy to remember.
Figure 6-12. The PGP Key Generation Wizard allows you to specify when your key automatically expires. Although this is useful in high-security applications, most users won't use this feature. After you choose an expiration time, you are prompted for a passphrase. PGP shows a passphrase rating.
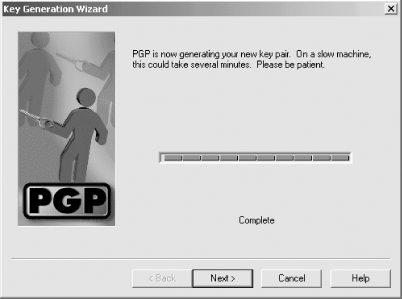
Finally, PGP creates the key (Figure 6-13).
Figure 6-13. Once all of the parameters of the key have been entered, the PGP Key Generation Wizard creates a key pair.
Earlier versions of PGP asked the user to type randomly on the keyboard or move the mouse to generate random numbers that were used as part of the key generation process. The current version of PGP gathers randomness from the user as part of its ongoing operations, and so does not include a special step requiring the user to move the mouse or type on the keyboard.
6.2.3.2 Smart cards
Smart cards are promising pieces of security technology. Take the card out of your computer, and you know that nobody else has access to your private key. Smart cards can also be programmed to require a PIN or passphrase before they will perform a cryptographic function; this helps protect your key in the event that the card is stolen. They can be programmed so that if many PINs are tried in succession, the key is automatically erased. Some smart cards forego the PIN and use biometrics instead: these smart cards are equipped with a small fingerprint reader.
Smart cards aren't without their drawbacks, however. If the card is lost, stolen, or damaged, the keys it contains are gone and no longer available to the user. Thus, if the keys on the card are to be used for long-term encryption of information, it may be desirable to have some form of card duplication system or key escrow to prevent key loss. Such measures are not needed, however, if the keys are only used for digital signatures. If a signing key is lost, it is only necessary to create a new signing key: no information is lost.
Some types of smart cards are exceptionally fragile and cannot hold up to day-to-day wear and tear. Keys stored on these cards may be inadvertently lost.
It is also the case that smart cards are not completely tamper-proof. Cryptographic smart cards implement tiny operating systems: flaws in these operating systems can result in the compromise of key material. It is also possible to physically analyze a card and force it to divulge its key. In 1996, Ross Anderson and Markus Kuhn presented a paper on how they broke the security of a professionally designed smart card widely used for security mechanisms.[5] More recently, two classes of nondestructive attacks have been identified on smart cards. Timing attacks are based on the observation that smart cards require slightly different amounts of time to perform encryption operations depending on the 1s and 0s in the keys that are being used. Differential power analysis (DPA) attacks are similar to timing attacks, except that they consider the amount of current used by the smart card for cryptographic operations. Details of these attacks can be found on the web pages of Cryptography Research, Inc., at http://www.cryptography.com/dpa/.
[5] For an excellent description of the ease of attacking hardware-based encryption devices, see Ross Anderson and Markus Kuhn, "Tamper Resistance a Cautionary Note," in The Second USENIX Workshop on Electronic Commerce Proceedings , Oakland, California, November 18-21, 1996, pp. 1-11, ISBN 1-880446-83-9. http://www.usenix.org/publications/library/proceedings/ec96/full_papers/kuhn/.
| only for RuBoard - do not distribute or recompile |
EAN: 2147483647
Pages: 194