Understanding Common Ways Clients Receive Malicious Server Responses
Understanding Common Ways Clients Receive Malicious Server Responses
-
Client application knowingly connects to an arbitrary server. Most client applications are designed so that the client machine cannot be harmed when it connects to arbitrary servers. For example, a Web browser should not be harmed when it loads data from a server even if malicious data is encountered . However, this is not always the case. If a client issues requests to a malicious server, the server s responses could be designed to exploit bugs in the client.
Often, the target s client need not directly specify the malicious server to connect to. An attacker can use various methods to trick a victim s client into connecting to arbitrary servers. For example, a protocol handler hyperlink such as ftp://ftp.example.com could be used to force an FTP client to connect to ftp.example.com when the hyperlink is clicked. JavaScript can also be used to automate activating a hyperlink so the victim doesn t even need to click the link. Another example is when ActiveX controls are used to force a client to connect to a server of the attacker s choice. For example, Adobe Acrobat, RealNetwork RealPlayer, and Microsoft Windows Media Player all allow callers of their controls to specify to which server the client should connect without user intervention. It isn t hard to get a target to connect to a malicious server when functionality like this exists.
-
Attacker performs a man-in-the-middle (MITM) attack. Some clients don t allow the server to be specified. These applications typically connect only to a set of predefined trusted servers. Neither the user nor the attacker can specify the name of another server in this situation. However, an attacker might be able to intercept the network request to the server and respond with malicious data or intercept the response from the legitimate server and modify it. This is known as an MITM attack.
Important When users connect to untrusted networks that connect unknown other users, such attacks as the MITM attack are easier to pull off. How secure is your computer when you connect to a hot spot at the local coffee shop? Do you know for sure whether you are connecting to the coffee shop s network or to a rogue access point pretending to be the coffee shop s network? Do you really trust the other users on that network?
-
Attacker controls or poisons the DNS. In situations in which a client connects to a server by name, a DNS server is used to look up the IP address of the server. If the DNS information is controlled by an attacker, the lookup procedure might return the IP address of the attacker s server instead of the legitimate server s IP address, resulting in the client being directed to the attacker s machine. For more details, including several different attacks that allow DNS poisoning , see http://www.lurhq.com/dnscache.pdf .
Important Similar to DNS cache poisoning, a Web proxy s cache can be poisoned. The result is the attacker s response is sent to the client instead of the legitimate server s response. HTTP splitting is one way of poisoning a proxy s cache. HTTP splitting is discussed in Chapter 10, HTML Scripting Attacks.
-
Server socket is hijacked. When a program binds ( associates ) a local address with a port, the default action is for the program to associate all local addresses with that port. Even machines with one network card typically have at least two IP addresses ”an externally reachable address and the localhost address (127.0.0.1). It is possible for two programs to listen on the same port when different addresses are associated with that port. For example, one program could listen on port 80 for the external IP address while a separate program listens on the same port for the localhost address. Although a program might be listening on a port for all addresses, it is possible for another program to request the same port for a specific address. When a connection is made for the specific address, the program listening specifically for those requests will receive it. This is illustrated in Figure 5-1, which shows that the rogue program will receive all network requests with the destination IP address of 192.168.1.188 on port 8080 because the rogue program is more specific in what it is listening for than the legitimate program is.
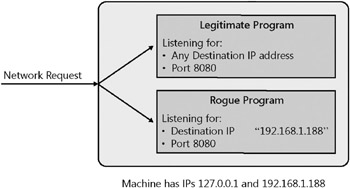
Figure 5-1: A rogue program listening specifically for requests for IP address 192.168.1.188 on port 8080Socket hijacking is a potential security problem in server software. If an attacker can gain user-level (nonadmin) access on the server, by listening on a specific address the attacker can attempt to receive requests normally received by a server process on the same machine. If a socket can be hijacked, the server program that opened the hijacked socket contains a bug that should be fixed.
| Tip | Applications on UNIX-based operating systems are also potentially vulnerable to socket hijacking. Most UNIX systems require admin/root to open a socket port 1024 and below. |
The Netcat tool ( http://www.vulnwatch.org/netcat/ ) is useful in testing for socket hijacking vulnerabilities. Once the target server program is listening on a port, issue the following command line as a user:
nc -s <IPAddress> -p <PortNumber> -v -l
where IPAddress is the address on the server to hijack and PortNumber is the port to hijack. The account used to launch the Netcat command should be different from the one used by the server process. Once the Netcat command is issued, attempt to make aconnection to the server. If Netcat receives the connection, the server application is vulnerable to socket hijacking.
| Tip | In versions earlier than Microsoft Windows Server 2003, developers explicitly had to block socket hijacking by setting the SO EXCLUSIVEADDRUSE flag. As a result, many server applications are vulnerable to this attack. For example, we recently tested several server applications and found most to be vulnerable. In Windows Server 2003, Microsoft enhanced socket security so that by default sockets are not sharable . More information about this change and socket hijacking is available on Microsoft Developer Network (MSDN) at http://msdn.microsoft.com/library/default.asp?url=/library/en-us/winsock/winsock/using_so_reuseaddr_and_so_exclusiveaddruse.asp . |
EAN: 2147483647
Pages: 156