Advanced Configurations
| Advanced configurations are those that are a bit more than just authenticating a user with a password. They can be used in a number of ways that you see during the course of this book. Some of these advanced configurations include some of these features:
A beneficial advanced configuration capability of ACS is the configuration of 802.1x Switchport Authentication. The IEEE 802.1x standard defines a client-serverbased access control and authentication protocol that restricts unauthorized clients from connecting to a LAN through publicly accessible ports. This might be a connection directly into a switch or via a wireless network. This is done by the authentication server, in this case ACS, authenticating each client connected to a switchport and assigning that port to a VLAN before making available any services offered by the switch or the LAN. Until the client is authenticated, 802.1x access control allows only Extensible Authentication Protocol over LAN (EAPOL) traffic through the port to which the client is connected. After authentication is successful, normal traffic can pass through the port. EAP SupportEAP support can be considered an advanced configuration in ACS. The actual EAP support at the switchport can be performed via the RADIUS protocol by authenticating the user to ACS. In this type of environment, you must determine what type of EAP to use, EAP-TLS or EAP-MD5. To enable switchport authentication support in ACS, follow these steps:
Configuring SwitchesThe next set of configurations you need to do is configuring the switch to talk to ACS and vice versa. At this point, you should be able to add a new AAA client to ACS. Do this from the Network Configuration section. When you add the switch as an AAA client to ACS, ensure that you select RADIUS (IETF) as your protocol type. This is seen in Figure 7-17. Figure 7-17. Configuring the Switch as an AAA Client in ACS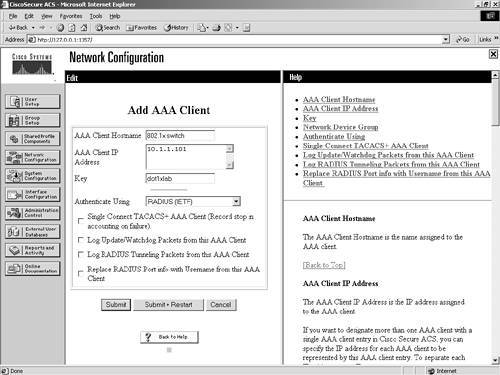 On the Cisco switch, you would enter the commands seen in Example 7-2. Example 7-2. AAA Switch Configurationswitch#conf t switch(config)#aaa new-model switch(config)#radius-server host 10.1.1.100 switch(config)#radius-server key dot1xlab switch(config)#aaa authentication dot1x default group radius switch(config)#dot1x system-auth-control Example 7-2 is for an IOS-based switch. For set-based switches see the Cisco documentation at http://www.cisco.com/univercd/home/home.htm. The preceding configuration enables VLAN assignments from the ACS server. The new topology with the 802.1x switch is seen in Figure 7-18. Figure 7-18. New Common Topology with 802.1x Switch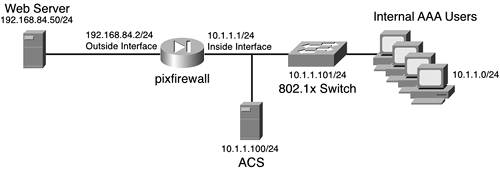 Enable an Administrative PolicyThe next configuration enables an administrative policy in ACS for the switch. Cisco recommends that you separate your users' access to the network from the administrator's access to the network. The simplest way to do so is by using the RADIUS protocol for average users and TACACS+ for administrative users. To enable this on your IOS-based switch, you enter the additional commands seen in Example 7-3. Example 7-3. Separating Users from Administrators[View full width] switch#conf t switch(config)#tacacs-server host 10.1.1.100 switch(config)#tacacs-server key dot1xlabadmin switch(config)#aaa authentication login default group tacacs+ local switch(config)#aaa authentication login not_auth none switch(config)#aaa authentication enable default group tacacs+ enable switch(config)#ip tacacs source-interface loop0 As long as you have users configured in the ACS and the AAA client has been defined, the administrator gains access to the switch where the average user that authenticates with RADIUS would fail shell authorization. To configure a host to perform EAP authentication, you can use the following URL as a guide for Windows XP: http://www.cisco.com/en/US/products/hw/switches/ps700/products_tech_note09186a00801d11a4.shtml. Note that URL requires a CCO login. |
EAN: 2147483647
Pages: 173
 This enables dot1x on the switch. switch(config)#
This enables dot1x on the switch. switch(config)#