Hack 24 Passive Scanning with KisMAC
|
Glean detailed network information with this passive scanner for OS X. KisMAC (http://www.binaervarianz.de/projekte/programmieren/kismac/ ) is another OS X tool that shares a name with the popular monitoring tool Kismet [Hack #31]. This is a much more advanced network discovery and monitoring tool than either MacStumbler or iStumbler [Hack #22]. As stated earlier, active scanners work by sending out probe requests to all available access points. Since these scanners rely on responses to active probing, it is possible for network administrators to detect the presence of tools like MacStumbler and iStumbler (as well as NetStumbler [Hack #21], miniStumbler [Hack #23], or any other tool that makes use of active network probes). KisMAC is a passive network scanner. Rather than send out active probe requests, it instructs the wireless card to tune to a channel, listen for a short time, then tune to the next channel, listen for a while, and so on. In this way, it is possible to not only detect networks without announcing your presence, but also find networks that don't respond to probe requests namely, "closed" networks (APs that have beaconing disabled). But that's not all. Passive monitors have access to every frame that the radio can hear while tuned to a particular channel. This means that you can not only detect access points, but also the wireless clients of those APs. The standard AirPort driver doesn't provide the facility for passive monitoring, so KisMAC uses the open source Viha AirPort driver (http://www.dopesquad.net/security/). It swaps the Viha driver for your existing AirPort driver when the program starts, and automatically reinstalls the standard driver on exit. To accomplish this driver switcheroo, you have to provide your administrative password when you start KisMAC. Note that while KisMAC is running, your regular wireless connection is unavailable. KisMAC also supplies drivers for Orinoco/Avaya/Proxim cards, as well as Prism II-based wireless cards. KisMAC's main screen provides much of the same information as MacStumbler or iStumbler. But double-clicking any available network shows a wealth of new information (see Figure 3-20). Figure 3-20. Wireless network details in KisMAC.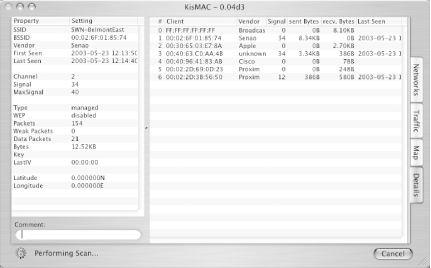 One interesting side effect of passive scanning is that channel detection isn't 100 percent reliable. Since 802.11b channels overlap, it is sometimes difficult for a passive scanner to know for certain which channel an access point is tuned to, and it can be one off from time to time. The AP in Figure 3-21 is actually set to channel 3, although it is reported as channel 2. KisMAC allows you to specify which channels you would like to scan on. This can help if you are trying to find access points that are using the same channel as your own. See Figure 3-21. Figure 3-21. You can select only the channels you need to scan in KisMAC.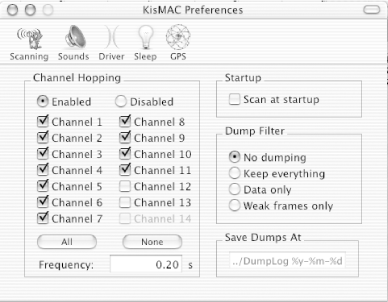 KisMAC has a slew of nifty features, including GPS support, raw frame injection (for Prism II and Orinoco cards), and even a real-time relative traffic graph (Figure 3-22). If it detects a WEP network, it can use a number of advanced techniques to try to guess the password. And yes, it can even read discovered ESSIDs aloud. Figure 3-22. Show the relative traffic of all detected networks, without transmitting a single bit.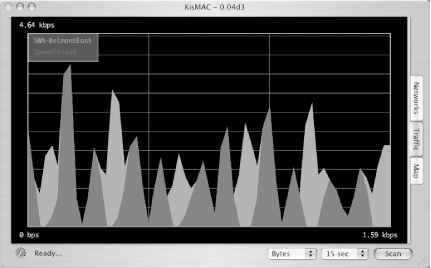 Perhaps the most powerful feature of all is KisMAC's ability to log raw 802.11 frames to a standard pcap dump. Check the "Keep Everything" or the "Data Only" option in preferences to save a dump file that can be read by tools such as Ethereal [Hack #39]. KisMAC is probably the most advanced wireless network monitor available for OS X, although it is still quite beta. I keep MacStumbler and iStumbler handy, as they both are slightly more stable and can operate without removing the AirPort driver. If you are simply looking for available networks, then KisMAC is probably overkill. But sometimes you need as much detail as you can get to troubleshoot difficult network problems, and when you do, KisMAC can be the right tool for the job. |
EAN: N/A
Pages: 158