14.5. Monitoring Traffic
| | ||
| | ||
| | ||
14.5. Monitoring Traffic
As already mentioned, the most popular tools used for local network break-in are sniffer programs, that is, traffic monitoring. Even though using these programs on the Internet is a more difficult task, it is not impossible . In this chapter, I consider the theory of implementing attacks using sniffers and explain how to detect traffic-intercepting sniffers in a network.
As you know, sniffers intercept packets addressed to other computers. Because most protocols are created at the dawn of the Internet and transmit data in plaintext, confidential information (passwords, credit card numbers , etc.) can easily be gathered from transmitted packets.
The initial purpose of sniffer programs was to be an administrative tool. But hackers found other applications for it, turning it from a simple network traffic analyzer into a powerful hacker weapon.
Sniffers can work in active and passive modes, both of which are considered in this chapter. However, to have a better understanding of the subject, you will have to learn the basic concepts of the Open Systems Interconnection (OSI) model.
14.5.1. The OSI Model
When data are sent over a network, they are directed from one computer to another. But how exactly is it done? You may guess that a special network protocol is used, and you would be right. But there are many protocol varieties. When is each of them used? How do they work? These and other questions I will try to answer in this section.
Before getting down to the protocols, you have to learn about the OSI model, developed by the International Standard Organization (ISO) to describe how information moves from one computer through a network medium to another computer. According to this model, all network interaction is broken down into the following seven layers (Fig. 14.1):
-
The physical layer is responsible for transmitting data over physical network media (e.g., coaxial, twisted pair, and fiber- optic cables). It defines physical environment characteristics and electrical signal parameters.
-
The data link layer provides transit of data between any nodes in typical topology networks or between adjacent nodes in random topology networks. Addressing employs MAC addresses.
-
The network layer defines the network address, which differs from the MAC address. The layer provides unreliable communication, meaning the delivery of packets is not guaranteed .
-
The transport layer is responsible for delivering data across the network with the specified delivery-reliability level. The layer provides for establishing a connection and buffering, numbering, and sequencing packets.
-
The session layer establishes, manages , and terminates communication sessions. The layer sets the currently-active communications party.
-
The presentation layer provides data coding and conversion functions.
-
The application layer provides a set of network services (FTP, email, etc.) for users and applications.
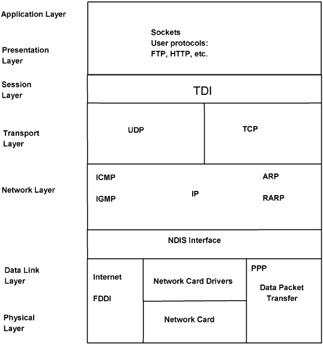
Figure 14.1: The OSI model
If you paid attention when reading the descriptions of the OSI layers, you probably noticed that the first three levels are implemented in hardware, such as network cards, routers, hubs, and bridges. The last three layers are implemented by the operating system or applications. The fourth layer is implemented in both hardware and software.
How are data transmitted according to this model? The process starts with the application layer, where packets are added a header. The application layer then transfers the resulting packet to the presentation layer. The application layer communicates any necessary control information required by the application layer of the destination machine by prefixing a header of its own to the packet. The process is repeated for each successive layer up to the physical layer, which places the packet on the network media.
The process is reversed on the destination machine, with each layer stripping the header added by the corresponding layer on the source machine and passing the resulting data unit to the next layer until only pure information, without any service data, is handed to the application layer.
Data transmission does not necessarily start from the physical layer. If the protocol used works on the transport layer, the packet's downward travel starts at this layer. The number of layers used by a protocol defines its needs and data-transfer capabilities.
The higher a protocol (the closer to the application layer), the more capabilities it has and the more overhead involved in data transmission (more headers, which are also more complex).
14.5.2. Passive Sniffing
Passive sniffing involves monitoring packets that pass directly through your network card. This method can only be used on the common-bus and star-topology networks. (Network topologies are described in Section 5.2 .)
Passive sniffing is the easiest to implement. All network packets that pass through a network card are checked for being addressed to that card. The network card compares the destination address in the packet header with its own MAC address and, if they match, passes the packet to the operating system for further processing. Packets whose address does not match are rejected. The operating system uses the header information to determine the port, to which the packet is directed, and the program that opened the port and must process the packet.
Processing to filter out packets addressed to a particular computer is carried out on the network card level. But a network card can be placed into a special mode, called promiscuous, in which all packets are passed to the operating system and can be processed using specialized programs. It should be noted that not all network cards can be switched into the promiscuous mode, but at least all modern cards can.
This trick, however, cannot be pulled on the Internet and networks using routers, because only packets addressed to a particular network card reach that card. All other packets are filtered out by switches or the provider's routers. In this case, active sniffing is resorted to.
At first, it may seem that administrators cannot detect sniffing, making engaging in this activity safe for hackers. Acting on this belief, some beginning hackers launch their sniffing programs and keep them running all day long, waiting for secret passwords to start coming their way. But administrators can and should detect sniffing activity in their networks, even passive sniffing, and discover and punish the perpetrator.
Passive sniffing is detected by sending ping requests to all network computers, in which the correct IP address but an incorrect MAC address is specified. In the regular mode, the network card checks each packet's MAC address and rejects those packets that are not addressed to it. But if the network card is switched into the promiscuous mode, it will pass any packet it receives to the operating system, which will check the packet's IP address. Because the packet's IP address is correct, the operating system will respond to it with an echo reply. This explicitly indicates that the given computer's network card is switched into the promiscuous mode.
But hackers are not that stupid and operate from behind firewalls. All the hacker has to do is prohibit outgoing ICMP traffic, and his or her computer will not reply to the administrator's ping requests.
An indication of a sniffer in a system can be increased average processor workload. This is caused by the network card passing all network traffic to the operating system.
To find out whether your network card is operating in the promiscuous mode, execute the following command:
ifconfig -a
If the PROMISC mode is set, your card can monitor all network traffic.
14.5.3. Active Sniffing
Active sniffers redirect other computers' traffic to themselves . This is done by modifying routing tables and fooling network equipment, which is more difficult to implement.
To understand how active sniffing works, you have to understand how packets are transmitted at the low layers. To transfer packets on the Internet, network devices use IP addresses. If the destination IP address is within the current network, the packet is delivered using the MAC address; otherwise , it is sent to the default gateway, which is either a router or a computer forwarding packets to the router. The router uses the packet's IP address to determine the necessary destination network. When such a network is found, the packet is passed to this network, where it is delivered to the destination by its MAC address.
Spoofing the MAC Address
Thus, inside networks, packets are addressed using only the MAC address. This is because network cards, hubs, and most switches work only with MAC addresses.
Here is where the OSI model comes into the play. Network cards, hubs, and most switches operate on the level of the data link layer. Receiving a packet, they check its data link header, operating only with MAC addresses. These devices can neither see nor understand other layer headers. Routers and more advanced (third-layer) switches disassemble packets to the network layer, where IP addresses are used.
Thus, within a network that has no third-layer switches, packets can only be addressed using MAC addresses. But how is it done exactly? Users never specify the MAC address, and you cannot simply place a packet on the network addressed using the IP address.
How, then, does the source computer find out the MAC address of the destination computer? It first sends a broadcast request to all computers in the network, asking something like this: Whose IP address is XXX.XXX.XXX.XXX ? The request is sent using ARP. Also, packets are addressed using a special broadcast address as the destination MAC address, and all network cards must accept such packets and pass them for processing to the operating system. The operating system examines the packet on the network-layer level, where ARP is employed. If the IP address being inquired about belongs to the particular computer, the operating system replies to the requester informing it about its MAC address. Now the source computer has the IP address mapped to the MAC address.
But what is to prevent your computer to answer ARP requests directed to another computer and pass itself off as that computer? Nothing. ARP does not have any authentication mechanism. It blindly accepts any replies to any ARP requests without further questions.
But this is not the worst thing. The source operating system caches responses to its ARP requests, and the next time it has a message to a resolved IP address, it does not send a broadcast ARP request but uses the cached MAC-mapping information. And here is the worst thing. Some operating systems (I will not name names ) cache not only replies to its own ARP requests but also replies to ARP requests issued by any other host. Thus, a hacker's computer can send ARP replies mapping its MAC address to another computer's IP address to all network's computers, and they will cache this fake MAC-to-IP mapping information.
You can view the current ARP cache by executing the arp command. The results of its execution look similar to the following:
Address HWtype HWaddress Flags Mask Iface 192.168.77.10 ether 00:03:0D:06:A4:6C C eth0
The most interesting columns are the following:
-
Address The computer's IP address
-
HWtype The remote device type
-
HWaddress The MAC address of the remote device
-
Iface The network interface
Thus, if a host has to address a computer with the IP address 192.168.77.10, it uses its ARP table to determine that the computer with this address can be found at the eth0 network interface and that its hardware (network card's) address is 00:03:0D:06:A4:6C.
If you discover fake IP-to-MAC mapping information in the ARP table, you should delete it; afterwards, you can use the MAC address to find the miscreant.
You can delete entries from the ARP table by executing the arp command with the -d option and specifying the necessary IP address. For example, the ARP entry in the preceding example can be deleted as follows :
arp -d 192.168.77.10
This will result in the MAC address being replaced with (incomplete):
Address HWtype HWaddress Flags Mask Iface 192.168.77.10 (incomplete) eth0
ARP table entries added to the cache by ARP are dynamic, meaning they are periodically deleted. Hackers know this and may periodically mail fake ARP replies. So simply deleting fake entries from the ARP table will not be effective. You have to find and go after the miscreant.
You can use Reverse ARP (RARP) for this. This protocol requests the IP address from a known MAC address. You should receive replies from all IP addresses, for which there are entries in your ARP table. Keep in mind that more than one IP address can be mapped to one MAC address. For example, the network card on my computer has two IP addresses mapped to its MAC address to work in two logical networks concurrently. So this is a normal situation. But if a certain IP address does not answer, you should delete the corresponding entry in the ARP table.
For working with ARP tables in Windows, I recommend using the CyD NET Utils utility ( www.cydsoft.com ).
Keep it in mind, however, that it is difficult to spoof ARP mapping in Windows.Broadcasting fake ARP replies mapping IP address 192.168.77.1 to your MAC address will result in the computer with this IP address issuing an error message that this address is already used by another network device and disconnecting from the network. This can be avoided by sending fake ARP replies to only one computer instead of broadcasting them.
Sending fake ARP replies is a rather involved task. It is much easier to simply change the network card's MAC address if its driver supports this operation. This can be done using the already familiar ifconfig utility with the wh option followed by the hardware class and the new MAC address.
If switches can be easily fooled by using fake ARP entries, this is not the case with routers. Routing devices operate on the network layer level, that is, on the IP address level. To fool routers, faking MAC addresses will not do; it takes faking IP addresses. For this purpose, hackers break into routers and reprogram them to serve their needs.
The only way to resist fake ARP information is by employing programmable switches to organize the network. These switches can permanently assign a certain MAC address to each of its ports. But this is only a partial solution to the fake ARP reply problem.
The complete solution is to use static ARP table entries, that is, to manually fill out the ARP table on each client computer. But this is not that convenient to put into practice, because ARP tables on all computers will have to be edited when there is any network equipment change on a single computer. It's alright if you have, say, five or even ten computers in the network, but what if there are dozens or even hundreds of them? Every time you add or replace a network card, you will have to update the ARP tables on all of the network's computers.
To facilitate the task of manually updating ARP tables, you can create a script. The script is located on the server, and each client should run it at booting.
Flooding Switches
Hubs are devices that replicate all traffic that arrives to the incoming port to all outgoing ports. Switches are intelligent devices that route incoming packets to their corresponding MAC addresses. This means that a switch will send an incoming packet only to the port, to which the packet's recipient is connected, not to the rest of its ports.
Thus, sniffing is impossible on a network built using switches. But switches have one peculiar feature: When a switch cannot analyze all packets it receives, it switches to operating as a simple concentrator, replicating all incoming packets to all computers connected to it.
So you have to flood the switch with so much traffic that it switches into the broadcasting mode. The best way of doing this is by throwing a bunch of packets with wrong MAC addresses at the switch. It takes too much of the switch's resources to analyze such packets, and it cannot handle the workload.
The only way to defend against switch flooding is by using more powerful equipment. At present, switches from 3Com and Cisco are sufficiently powerful to handle even the maximum load of fake packets. I haven't had an opportunity to test equipment from other manufacturers.
Fooling Routers
Routers can also be fooled; to be more exact, computers acting as routers can be fooled. Suppose that your network consists of several subnetworks connected using routers. Fig. 14.2 shows an example of such a network.
Figure 14.2: A network with two routers
If a computer from Network 1 sends a packet to another computer in the same network, this packet, as you know, is forwarded using the MAC address without resorting to the routers. If a packet is addressed to another network, it is sent to the default gateway. Suppose that such a default gateway is the firewall computer. In this case, if the packet is addressed to the Internet, the firewall computer forwards it there without much ado. But if the packet is addressed to a computer in Network 2, the firewall computer will not necessarily forward it to the router. The firewall, acting as the default router, may send an ICMP message to the source computer, suggesting that it negotiate directly with the router connecting Network 1 to Network 2.
Because ICMP does not employ any authentication or encryption mechanisms, hackers can send such a message to any computer, asking it to use their computer instead of the legitimate router. This will give them the opportunity to view all traffic.
I recommend disabling the routing redirection feature by means of writing 1 to the /proc/sys/net/ipv4/conf/all/accept_redirects file. This is done by executing the following command:
echo 1 > /proc/sys/net/ipv4/conf/all/accept_redirects
This parameter can also be changed by adding the following line to the /etc/sysctl.conf file:
nt.ipv4.conf.all.accept_redirection=0
If there is only one router in your network, disabling routing redirection will only enhance the system's security. But even if there are more routers in the network, the network operation will not be affected much. At the worst, traffic will have to go through two routers instead of taking the direct route.
Because ICMP is necessary for carrying out the routing redirection attack, this protocol can be prohibited by configuring the firewall accordingly . This will make it impossible for hackers to send messages to redirect routing.
14.5.4. Hijacking the Connection
The first computer attack using connection hijack was carried out several decades ago. But even now, the only effective method to oppose this attack is to encode packets. At the initial stage of establishing a TCP connection between computers, two counters are created that are incremented with each sent packet. These counters can be intercepted with the help of network sniffers, and at a certain moment hackers can hijack the connection, becoming its owner and replacing the legitimate client in communications with the server. The legitimate client loses the connection.
In this way, hackers circumvent all authorization mechanisms. The legal client is initially authorized at the server, but then its connection is hijacked by hackers, who use it for their own purposes.
The reason for the connection vulnerability lies in the TCP/IP suite being obsolete. Its creators did not anticipate that someone may eavesdrop on network traffic or try to take over the connection. The problem is expected to be solved with the introduction of IPv6.
14.5.5. Protecting Against Eavesdropping
Even though it is possible to detect that you are being eavesdropped on, sometimes this knowledge may come too late. While you are discovering the hackers, they may intercept packets with passwords and break into the system. If sniffing is being conducted by a program installed on a zombie computer, you will be able to find out only this computer and its owner but not the hacker who installed the sniffer program.
Consequently, detecting sniffing and going after the perpetrator is not effective against sniffing. You should make sniffing unproductive for hackers so that they would not even think about resorting to it. The way to achieve this is to encrypt all traffic.
You cannot trust the network and send your data in plaintext over it. The times when networks were used only by professionals and only as intended are long gone. Nowadays, you can meet all kinds of people on the Internet, from children to retirees, from school students to scientists. What is more pertinent, there are not only good guys out there but also those bent on mischief.
In Section 5.2 , techniques to encrypt any service communications were considered. Thus, you can encrypt any connection and must do this if confidential information is being transmitted.
But before you start encrypting channels on your own, look around for an existing solution. For example, there already exists an HTTP version that supports encryption: HTTPS. You can use HTTP for transmitting public data, such as Web pages, and use HTTPS for transmitting confidential data, such as credit card numbers.
Even if hackers intercept a packet with encrypted data, they will not be able to decrypt it right away unless they have the private key, which is extremely unlikely . They can attempt to break the key, but this process will take too much time; by the time the packet is decrypted, if it is decrypted, its data will be of no value. Moreover, the data may be of no interest to the hackers to start with, but to find this out they will have to spend time decrypting it.
14.5.6. Sniffing Tools
Reading this chapter, you may get the impression that sniffing is inherently harmless and is exclusively a tool of hackers. It may even seem that hardware manufacturers ought to make their equipment sniffing-proof on the hardware level.
This is not quite the case. Sniffer software was initially developed as a programmer and administrator tool, and it is a handy means for debugging various protocols.
I will not consider all sniffer programs, because there are many of them and each has its own advantages and disadvantages. But I can recommend taking a look at my favorite and one of the most powerful of such programs: hunt . It can be used to monitor traffic, replace ARP records, and even intercept connections.
Another popular and in some cases more convenient is the dsniff utility package. This package comprises more than ten utilities and can be used to solve any task, both by administrators and hackers. A more detailed description of the package is given in Appendix 2 .