B.4 Project 1: Firewall and proxy server
| StoreCompany's desire to add its catalog to the Internet sparked an audit into security and feasibility of the project. A firewall and demilitarized zone would be needed to separate the zSeries from the Internet. The conclusion was that infrastructure servers could be located as Linux guests under z/VM on the mainframe. This would have three desirable results: a standard setup for all guests, some savings in actual hardware, and a fairly simple project for introducing Linux on the mainframe into the production environment. The team doing the Linux infrastructure work was composed of both mainframe and UNIX/Linux people. The infrastructure work went well. It was fast (75 days) and it was on budget. After the conclusion of Project 1, security had the structure needed to give the green light to the more complicated online catalog project. As a follow up from Project 1, StoreCompany then decided to move its departmental Samba servers from UNIX and Windows servers to the mainframe. These servers hold data for the various StoreCompany departments. B.4.1 Changes needed
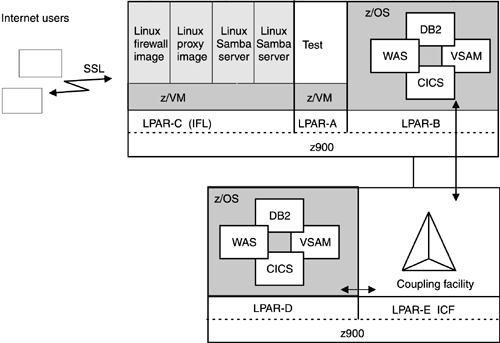
B.4.2 ImplementationWork started out with Linux on z/VM under the test LPAR, LPAR-A. Once that worked, an IFL was ordered as a trial, knowing that it could be sent back if things did not work. While the IFL order process was wending its way through StoreCompany, the project went into production using the test LPAR just before the IFL was to show up to accelerate delivery. Once the IFL was in place and the second z/VM was set up, ISPCompany just moved over the Linux image and the network attachment, and so forth. The final implementation is shown in Figure B-3.
Figure B-3. Logical setup of StoreCompany after locating the firewall and the proxy on the zSeries machine
|
EAN: 2147483647
Pages: 199