Calling the Access List
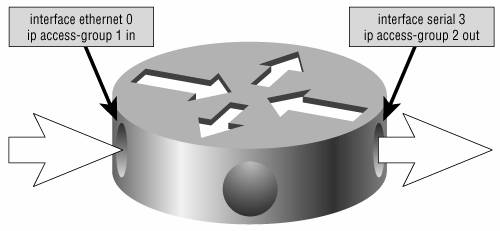
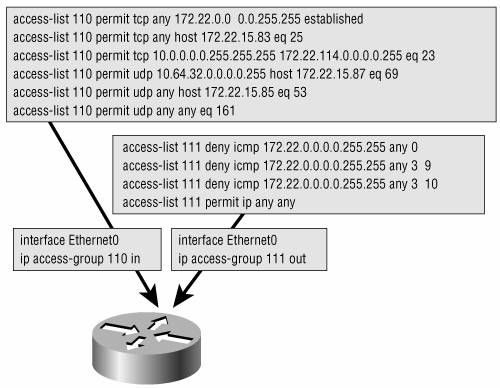
| An access list does nothing unless packets are sent to it by a calling command, which defines how the access list is to be used. One such command is ip access-group access-list-number {in | out} This command is configured on an interface to create security or traffic filters and can be applied to incoming or outgoing traffic. If neither the in nor the out keyword is specified, the filter defaults to outgoing. The access list number, of course, is the access list to which this command will send packets. Figure B-9 shows two configurations of this command. Figure B-9. The ip access-group command uses the specified access list to create a filter on an interface for either incoming or outgoing packets. Access list 1 in Figure B-9 filters incoming IP packets on interface E0. It has no effect on outgoing IP traffic and no effect on packets originated by other protocols, such as IPX. Access list 2 filters IP packets going out interface S3. It has no effect on incoming IP packets and no effect on packets originated by other protocols. Denying as much as possible on the inbound access list instead of the outbound list alleviates the need for the router to perform work on traffic that will be dropped. Multiple interfaces can make calls to the same access list, but any one interface can have only one incoming and one outgoing access list for each protocol. In Figure B-10, the TCP, UDP, and ICMP access lists given earlier as examples are used as filters. Access list 110, from the previous two examples, has been applied to the Ethernet 0 interface to check incoming traffic. Access list 111 is applied to the same interface to check outgoing traffic. Analyze the two access lists carefully, including their interrelationship, and consider the following:
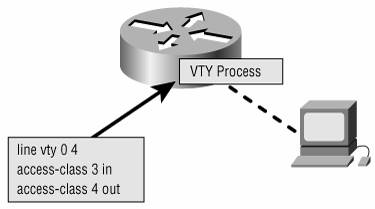
Figure B-10. Access list 110 is used here to filter incoming packets on the Ethernet interface. Access list 111 is used here to filter outgoing packets on the same interface. The ping response from 172.23.12.5 will be allowed to exit interface Ethernet 0. Ping responses are denied for packets from 172.22.0.0/16, not 172.23.0.0/16. The ping from 172.22.67.4 to 10.64.32.20, exiting Ethernet 0, will not be successful. The ping request will successfully exit the interface, but the response will be denied by the inbound access list. Another command that makes calls to an access list is the access-class command. This command is used to regulate Telnet sessions to and from the router's virtual terminal lines, not for packet filtering. The format of the command is access-class access-list-number {in | out} Figure B-11 shows an example of the access-class command. Access list 3 regulates the addresses from which the router's VTY lines will accept Telnet sessions. Access list 4 regulates the addresses to which the router's virtual terminal lines may connect. Figure B-11. The access-class command uses an access list to regulate Telnet traffic to and from the router's virtual terminal lines. The access-class command has no effect on Telnet traffic transiting the router. It influences only Telnet sessions to and from the router itself. |
EAN: 2147483647
Pages: 233
- Enterprise Application Integration: New Solutions for a Solved Problem or a Challenging Research Field?
- The Effects of an Enterprise Resource Planning System (ERP) Implementation on Job Characteristics – A Study using the Hackman and Oldham Job Characteristics Model
- Distributed Data Warehouse for Geo-spatial Services
- A Hybrid Clustering Technique to Improve Patient Data Quality
- Relevance and Micro-Relevance for the Professional as Determinants of IT-Diffusion and IT-Use in Healthcare