L2TP
A protocol called the Layer 2 Tunneling Protocol (L2TP) has been defined by the PPP Extensions working group of the IETF as a way to, you guessed it, tunnel layer 2 data. Remember the OSI model of networking from Chapter 2. The link layer is layer 2, the layer at which data is sent directly from one entity to another over the physical connection (which is at layer 1).
The link layer can be either packet-switched or circuit-switched but regardless, the data being transferred is addressed from one physical entity to another. There is no concept of a route across the network at layer 2. One can say that layer 2 transmissions are point to point.
In fact, the main use of L2TP is to tunnel data that is already in the point-to-point protocol (PPP). Usually, when one uses a modem the data is sent from the local computer's modem to a remote modem encapsulated in PPP. The physical connection is the phone circuit and data is transferred directly from one physical endpoint to another. The information being sent across this point-to-point link is PPP-encapsulated data, usually IP datagrams. Upon receipt of PPP data, the PPP header is stripped off to reveal the IP data inside. This data is then routed normally as if it had been encapsulated in an Ethernet frame and taken off a directly connected network.
Quite often the modem that a local computer dials into is not on the network to which the PPP-encapsulated data is destined. For instance, a traveling businessman in a hotel room can dial a local Internet Service Provider (ISP) who will terminate his PPP packets and forward the resulting IP datagrams onto the Internet toward his ultimate destination. Using a local service provider would most likely be cheaper due to long distance phone charges or the maintenance of an 800 number by the businessman's company. The problem then is that the businessman's computer has an ISP-assigned address (which is foreign to the network that he is trying to reach) and will most likely fail any sort of access control or security check that the network will apply to his packets.
If the PPP data, which is layer 2 data, could be transmitted across the network and be terminated by a server on the network to which he is trying to reach, he could take advantage of all the services of his network (local IP address, resource sharing, security, and access control) and save on the cost by still placing a local call to a local ISP. This is where L2TP comes into play.
L2TP tunnels begin and terminate at the network layer. An L2TP Access Concentrator (LAC) is the client end of the connection while an L2TP Network Server (LNS) is the server side. The PPP packets are encapsulated in an L2TP header that are, themselves, encapsulated in IP. These IP packets can traverse the network just like ordinary IP datagrams. When such a packet is received, the LNS demultiplexes the session using information in the L2TP header. It can then decapsulate the PPP data in a session-specific manner and forward the internal IP datagrams onto the local network.
There are two types of L2TP configurations: compulsory, where the client connects to an ISP acting as a LAC which tunnels PPP packets to the LNS (Figure 12.6a); and voluntary, where the client acts as the LAC and brings up an L2TP tunnel directly with the LNS after first bringing up a connection to the ISP (Figure 12.6b). In the former, L2TP runs in the ISP-controlled LAC. In the latter, L2TP runs on the client itself.
Figure 12.6. Network Access with L2TP.
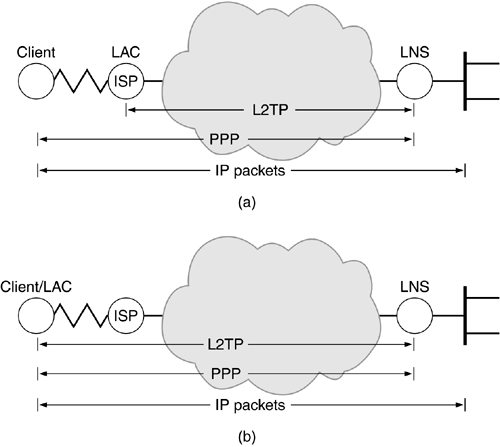
When using L2TP, the businessman can obtain an IP address from the enterprise network he is trying to access. This will allow his local computer to appear as if it is on the enterprise network. The addressing could even be non-routable in the ISP's domain! From a logical point of view, it will be the same as his computer being directly connected to the enterprise network via an Ethernet Network Interface Card (NIC). All resource sharing functionality that he can take advantage of at work is available on the road. In addition, the network administrator can monitor the session because the point-to-point connection is actually being terminated at his LNS.
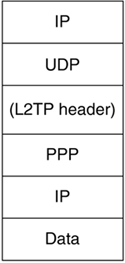
L2TP can be implemented as a UDP-based IP protocol (Figure 12.7). To envision how the various encapsulations work, start with the packet generated by the businessman's computer in our example. It is an IP packet sourced by his computer and destined for his company's remote network (note that the source IP addresses of this packet may be on the same network). This packet is then encapsulated in PPP that terminates on his company's LNS. These PPP packets are encapsulated in L2TP also terminated on the LNS. The L2TP packets are UDP packets encapsulated in an IP datagram that is addressed from an IP address assigned by the local ISP to which the businessman is dialing into and destined to the ISP's network access server (NAS). This IP packet will again be encapsulated in PPP, this time terminated by the ISP's NAS. This final, heavily encapsulated packet will be sent over the circuit-switched layer 2 phone line. Note that the local businessman's computer has two IP addresses. One, assigned by the ISP is the IP address of the physical connection most likely a modem while the other, assigned by the remote network with which he is connecting, is a logical IP address of his computer. The computer "thinks" its IP address is the logical one.
Figure 12.7. An L2TP Packet.
L2TP does not provide any security. Since L2TP runs over IP, it is possible to use IPSec to secure the tunnel.The data to protect are IP packets from the businessman's computer, either acting as an LAC or using the ISP's NAS as the LAC, to his company's LNS and back. IPSec can therefore be used in transport mode; the data is already being tunneled and therefore the extra overhead of another IP header is unnecessary. (Given the amount of overhead already, any savings will help.)
By using L2TP with IPSec it is also possible to protect non-IP data. Since L2TP tunnels layer 2 packets, any layer 2 protocol, for example IPX or AppleTalk, can be tunneled. When used in this fashion the L2TP tunnel will most likely not terminate on the box that is natively speaking IPX or AppleTalk. Instead, the LAC and LNS interconnect an IPX or AppleTalk network to an IP network. The L2TP tunnel between them is across the IP cloud. In effect, a layer 2 VPN has been set up because these two disparate networks are now virtually connected across a foreign (speaking) network. IPSec can then be used to protect this layer 2 VPN and provide the security necessary. This is very important because there is no IPX or AppleTalk analogy to IPSec; that is, there is no layer 3 security service that operates on native IPX or AppleTalk. The only way to get confidentiality and data integrity on an IPX or AppleTalk network is by tunneling it through L2TP and protecting that tunnel with transport mode IPSec. There is no requirement that L2TP be run over IP (its transport specification is so generic that it has been claimed that L2TP could be implemented over "running shoes" i.e., couriers could run back and forth with messages between tunnel endpoints), but to use IPSec for protection there is.
| Top
IPSec (2nd Edition) ISBN: 013046189X
EAN: 2147483647 Year: 2004
Pages: 76 Authors: Naganand Doraswamy, Dan Harkins
flylib.com © 2008-2017. If you may any questions please contact us: flylib@qtcs.net |