IPSec Modes
We have talked about IPSec in transport mode and tunnel mode without explaining when and how IPSec protocols are used in these modes. In this section, we describe how the IPSec protocols, AH and ESP, implement the tunnel and transport modes. There are four possible combinations of modes and protocol: AH in transport mode, AH in tunnel mode, ESP in transport mode, and ESP in tunnel mode. In practice, AH in tunnel mode is not used because it protects the same data that AH in transport mode protects.
The AH and ESP header do not change between tunnel or transport mode. The difference is more semantic in nature what it is they are protecting, IP packet or an IP payload. The guidelines for deciding what mode to use and some examples of using IPSec in various modes is discussed in later chapters.
Transport Mode
In transport mode, AH and ESP protect the transport header. In this mode, AH and ESP intercept the packets flowing from the transport layer into the network layer and provide the configured security.
Let us consider an example. In Figure 4.5, A and B are two hosts that have been configured so that all transport layer packets flowing between them are encrypted. In this case, transport mode of ESP is used. If the requirement is just to authenticate transport layer packets, then transport mode of AH is used.
Figure 4.5. Hosts with transport ESP.
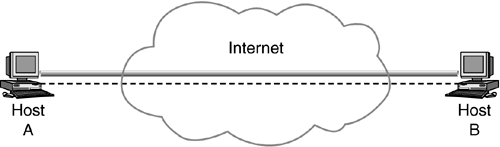
When security is not enabled, transport layer packets such as TCP and UDP flow into the network layer, IP, which adds the IP header and calls into the data link layer. When security in transport layer is enabled, the transport layer packets flow into the IPSec component. The IPSec component is implemented as part of the network layer (when intergrated with OS). The IPSec component adds the AH, ESP, or both headers, and invokes the part of the network layer that adds the network layer header.
The transport mode of IPSec can be used only when security is desired end to end. As stated earlier, the routers look mostly at the network layer in making routing decisions and the routers do not and should not change anything beyond the network layer header. Inserting transport mode IPSec header for packets flowing through a router is a violation of this rule.
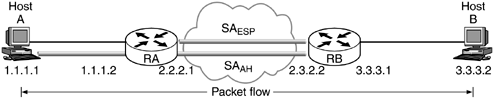
When both AH and ESP are used in transport mode, ESP should be applied first. The reason is obvious. If the transport packet is first protected using AH and then using ESP, the data integrity is applicable only for the transport payload as the ESP header is added later on as shown in Figure 4.6.
Figure 4.6. Packet format with ESP and AH.
![]()
This is not desirable because the data integrity should be calculated over as much data as possible.
If the packet is protected using AH after it is protected using ESP, then the data integrity applies to the ESP payload that contains the transport payload as shown in Figure 4.7.
Figure 4.7. Packet format with AH and ESP
![]()
The transport mode for BITS implementation is not as clean, as the ESP and AH headers are inserted after the IP payload is constructed. This implies the BITS implementation has to duplicate the IP functionality because it has to recalculate the IP checksum and fragment the packet if necessary. Many BITS implementations may not support transport mode but support only tunnel mode.
Tunnel Mode
IPSec in tunnel mode is normally used when the ultimate destination of the packet is different from the security termination point as shown in Figure 4.8 or in case of BITS or BITW implementations. The tunnel mode is also used in cases when the security is provided by a device that did not originate packets as in the case of VPNs.
Figure 4.8. IPSec in tunnel mode.
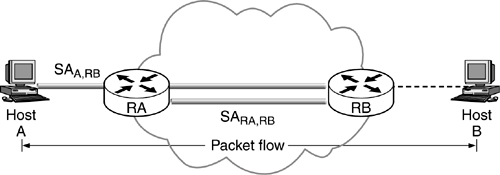
It is also used when a router provides security services for packets it is forwarding. The operation of tunnel mode is discussed in detail in the IPSec implementation chapter.
In the case of tunnel mode, IPSec encapsulates an IP packet with IPSec headers and adds an outer IP Header as shown in Figure 4.9.
Figure 4.9. IPSec tunneled mode packet format.

An IPSec tunneled mode packet has two IP headers inner and outer. The inner header is constructed by the host and the outer header is added by the device that is providing the security services. This can be either the host or a router. There is nothing that precludes a host from providing tunneled mode security services end to end. However, in this case there is no advantage to using tunnel mode instead of transport mode. In fact, if the security services are provided end to end, transport mode is better because it does not add an extra IP header.
IPSec defines tunnel mode for both AH and ESP. IPSec also supports nested tunnels. The nested tunneling is where we tunnel a tunneled packet as shown in Figure 4.10a.
Figure 4.10a. Nested tunnel example.
In this example, host A is sending a packet to host B. The policy says it has to authenticate itself to router RB. In addition, there is a VPN between the two networks bordered by RA and RB. The packet seen by router RB is shown in Figure 4.10b. The outermost header is the tunneled ESP packet. It is carrying a tunneled AH packet. The tunneled AH packet is carrying the IP packet destined for the host B generated by host A.
Figure 4.10b. Nested packet format.

The requirement for the tunnel is that inner header is completely encompassed by the outer header. The valid and invalid tunnels examples are shown in Figures 4.11a and b.
Figure 4.11a. Valid tunnel.
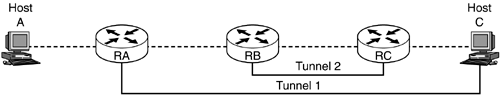
Figure 4.11b. Invalid tunnel.
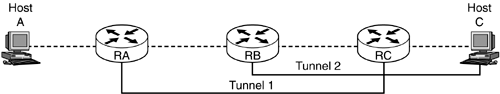
The example shown in Figure 4.11a is valid as the inner tunnel (tunnel 2) is completely encompassed by tunnel 1. The example shown in Figure 4.11b is invalid because neither tunnel completely encompasses the other. To understand why this is invalid, let us trace the packet flow. After RA constructs the tunneled packet, the packet format is as shown in Figure 4.12a.
Figure 4.12a. Tunneled packet.
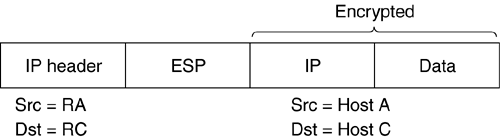
When the packet reaches RB, it tunnels the packet to host C. The packet format when the packet leaves RB is shown in Figure 4.12b.
Figure 4.12b. Invalid tunnel packet.

Clearly, this is incorrect because the packet now reaches host C before it reaches RC. When the packet reaches host C, it processes the AH header. When the second IP header is exposed, the host drops the packet because the destination is RC and not itself. Nested tunnels are difficult to build and maintain and should be used sparingly.
| Top
IPSec (2nd Edition) ISBN: 013046189X
EAN: 2147483647 Year: 2004
Pages: 76 Authors: Naganand Doraswamy, Dan Harkins
flylib.com © 2008-2017. If you may any questions please contact us: flylib@qtcs.net |