IPSec Implementation
IPSec can be implemented and deployed in the end hosts or in the gateways/routers or in both. Where in the network IPSec is deployed depends on the security requirements of the users.
This section discusses the capabilities and implications of implementing IPSec in various network devices (hosts and routers). There are merits in implementing IPSec in both routers and end hosts as they address different problems. The host implementation is most useful when end to end security is desired. However, in cases when security is desired over a part of a network, router implementation is desirable. This includes VPNs, Intranets, and Extranets.
Host Implementation
The proper definition of a host in this context is the device where the packet is originating. The host implementation has the following advantages:
Provides security end to end
Ability to implement all modes of IPSec security
Provides security on a per flow basis
Ability to maintain user context for authentication in establishing IPSec connections
Host implementations can be classified into:
Implementation integrated with the operating system (OS). We call it host implementation (for lack of a better term).
Implementation that is a shim between the network and the data link layer of the protocol stack. This is called the "Bump in the Stack" implementation.
OS Integrated
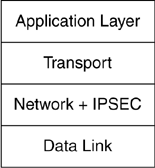
In the host implementation, IPSec may be integrated with the OS. As IPSec is a network layer protocol, it may be implemented as part of the network layer as shown in Figure 4.2. IPSec layer needs the services of the IP layer to construct the IP header. This model is identical to the implementation of other network layer protocols such as ICMP.
Figure 4.2. IPSec stack layering.
There are numerous advantages of integrating the IPSec with the OS. A few key advantages are listed below.
As IPSec is tightly integrated into the network layer, it can avail the network services such as fragmentation, PMTU, and user context (sockets). This enables the implementation to be very efficient.
It is easier to provide security services per flow (such as a Web transaction) as the key management, the base IPSec protocols, and the network layer can be integrated seamlessly.
All IPSec modes are supported.
Bump in the Stack
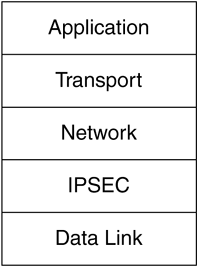
For companies providing solutions for VPNs and intranets, OS integrated solution has one serious drawback. On the end hosts, they have to work with the features provided by the OS vendors. This may limit their capabilities to provide advanced solutions. To overcome this limitation, IPSec is implemented as a shim, and inserted between the network and the data link layer as shown in Figure 4.3. This is commonly referred to as Bump in the Stack (BITS) implementation.
Figure 4.3. BITS IPSec stack layering.
As you may notice, the major issue in this implementation is duplication of effort. It requires implementing most of the features of the network layer, such as fragmentation and route tables. Duplicating functionality leads to undesired complications. It becomes more difficult to handle issues such as fragmentation, PMTU, and routing. An advantage of BITS implementation is the capability of an implementation to provide a complete solution. Vendors providing integrated solutions such as firewalls, prefer to have their own client as the OS vendor and may not have all the features required to provide a complete solution.
Router Implementation
The router implementation provides the ability to secure a packet over a part of a network. For example, an organization may be paranoid about the Internet but not its own private network. In this case, it may want to secure only those packets destined to the geographically distributed branchs as these packets traverse the Internet. The IPSec implementation provides security by tunneling the packets.
The router implementation has the following advantages:
Ability to secure packets flowing between two networks over a public network such as the Internet.
Ability to authenticate and authorize users entering the private network. This is the capability that many organizations use to allow their employees to telecommute over the Internet to build its VPN or intranet. Previously, this was possible only over dial-ups (dialing through modem directly into the organization).
There are two types of router implementation:
Native implementation: This is analogous to the OS integrated implementation on the hosts. In this case, IPSec is integrated with the router software.
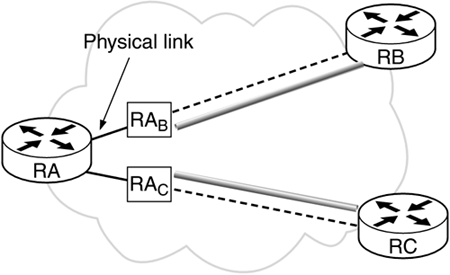
Bump in the Wire (BITW): This is analogous to BITS implementation. In this case, IPSec is implemented in a device that is attached to the physical interface of the router. This device normally does not run any routing algorithm but is used only to secure packets. BITW is not a long-term solution as it is not viable to have a device attached to every interface of the router.
The network architectures for these implementations is shown in Figure 4.4.
Figure 4.4a. Native implementation deployment architecture.
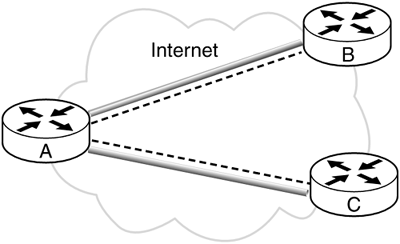
Figure 4.4b. BITW deployment architecture.
The IPSec implementation on routers has many implications on the packet-forwarding capabilities of the router. The routers are expected to forward packets as fast as possible. In fact, we are already seeing core routers that can forward up to 30 million packets per second! Although IPSec may not be used in the core of the Internet, the implementations should still be concerned about efficiency. The packets that do not require security should not be affected because of IPSec. They should still be forwarded at normal rates. Many implementations make use of some hardware assists to perform public key operations, random number generation, encryption/decryption, and calculating hashes. There are specialized chipsets that assist the basic router hardware with security operations.
Another issue with router implementation is IPSec contexts. Memory on the routers is still a scarce commodity, although this is changing fast with memory prices falling rapidly. As the router has to store huge routing tables and normally does not have huge disks for virtual memory support, maintaining too many IPSec contexts is an issue.
| Top
IPSec (2nd Edition) ISBN: 013046189X
EAN: 2147483647 Year: 2004
Pages: 76 Authors: Naganand Doraswamy, Dan Harkins
flylib.com © 2008-2017. If you may any questions please contact us: flylib@qtcs.net |