Considering Client-Server Networks
As the number of users grows, the peer-to-peer network model loses its value and eventually becomes unfeasible. Also, large or growing companies might have different needs than a small company has. The needs might include support for hundreds of users or the creation of a centralized order processing system that can be accessed by retail stores and on the Internet. However you size it up, the needs require a powerful and flexible model.
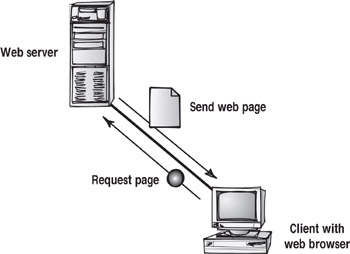
The client-server network was designed specifically to meet the complex and challenging needs of larger organizations. The name client-server originates from a design that requires some tasks to be completed by the user's workstation and other tasks to be processed centrally on a server. As an example of a client-server model, consider a user accessing a site on the World Wide Web.
In this graphic, a user at a workstation opens a web browser. The web browser is the client application. The user enters the URL of a website into the browser, which then makes a request to the web server for that site. The server sends the page with all its Hypertext Markup Language (HTML) code. Now that the server has completed its job, the client application is responsible for converting the HTML into a web page.
Hypertext Markup Language (HTML)
A text-based scripting language that is used in the creation of web pages to control the presentation of text and graphics. It can also be used to add functionality to the web page for navigation or for interfacing with other technologies like databases and multimedia.
domain model
Logically groups computers, users, and groups into a domain. Users log on to the domain and have access to any resources within the domain to which their user account has permission.
When Appropriate
Deciding between a peer-to-peer model and a client-server model is not as difficult as it may seem. First, the client-server model can be recommended to companies of all sizes and should be the first choice when there are 15 or more users. Second, you should consider potential growth. You might be a company of 10 people now, but plans might include increasing person nel to 20 or more in a short time. Planning for that growth can have a significant effect on cost savings and user productivity. Finally, certain application needs, especially those involving the Internet, require a client-server model. Common applications for centralizing resources include messaging (for example, e-mail), file and print sharing, databases, and fax/voice services.
The client-server network offers several key advantages:
-
Administration is centralized.
-
This model provides centralization of resources for easier backups.
-
Multiple levels of network security exist through management of usernames and passwords and through controlled access to network resources.
-
The network offers performance and reliability that can grow as demand grows.
However, the client-server model has some drawbacks:
-
A dedicated server is normally required.
-
It requires a more experienced administrator to install and manage the network than the peer-to-peer network model does.
-
It needs duplicate administration if users have to access more than one server.
Common OS Examples
Common examples of software that supports the client-server model include:
-
Novell NetWare versions 3, 4, 5, and 6
-
Unix
-
Linux
-
Windows 2000 Server and Windows Server 2003
-
AppleShare IP 6.1
-
Apple OS X Server
primary domain controller (PDC)
A PDC is used in an NT domain. The PDC contains the read-write copy of the domain accounts administration database, called the Security Accounts Manager (SAM).
Security Accounts Manager (SAM)
A database on NT servers that contains the relationship between who a user is and the level of security access that the user has to resources on the network.
backup domain controller (BDC)
Used in NT domains, it has read-only copies of the PDC accounts database. BDCs serve two primary functions: They offload logon authentication requests from the PDC, and they provide fault tolerance. If the PDC fails, the BDC can be promoted to a PDC.
authentication
A process that requires a user to enter an ID and a password and then be verified by the software to gain access to resources.
|
|