Chapter 3: Implementing Password Security
Although user accounts are the foundation upon which secure Windows Vista systems are built, the security they provide is only as good as the passwords that protect them. In fact, one could make a compelling argument that implementing user accounts with weak passwords is the same as not having any security at all. Part of the issue revolves around the fact that most users opt for simple passwords that are easy to remember, but people and their bad password habits are not the only culprits. A variety of hacking tools and password recovery programs also exist, capable of cracking and resetting even the most secure and complex passwords under the right conditions.
User accounts represent one of the first lines of defense on a Windows Vista system, but the need for good password practices hardly ends there. If you use the Internet, chances are that you have a myriad of different usernames and passwords configured to access different web sites. Although some of these may not represent a security risk - such as the one used to access the members area of your favorite gardening web site - others may be associated with services where rock-hard security is essential, as with online banking. Unfortunately, most users not only use weak passwords, but also compound the issue dramatically by using the same weak password for different user accounts.
If you're serious about security, you'll want to be absolutely sure that the passwords you use are actually capable of protecting your accounts. This chapter explains how to select good passwords, how to test password strength, and the importance of changing passwords regularly as serious threats like spyware proliferate. Along the way you'll also learn how to configure Windows Vista to enforce password and account lockout policy settings on users, how to get some help when it comes to remembering passwords, and how logon security can be completely compromised with the right tools and techniques.
Password Security
Passwords have always presented one of life's great quandaries. On the one hand you can select different complex passwords for each and every one of your user accounts, but what good is a strong password if you can't remember it? On the other hand, using similar (or even the same) weak passwords for every account virtually assures that you'll never forget it, but offers the equivalent of no real protection at all. The bottom line is that each user account password must be unique and complex to offer a high degree of protection. However, it's equally important for you to be able to remember your passwords. The good news is that striking this balance is not as difficult as most people make it out to be, although it does require a little effort and dedication on your part.
Selecting good passwords for user accounts involves three primary steps:
-
Choosing strong passwords
-
Avoiding common password "mistakes"
-
Changing your passwords frequently
Each of these steps is looked at in more detail in the following sections.
Choosing Good Passwords
It's a question for the ages - what makes a password good and strong? The answer isn't all that difficult, but there is definitely a formula of sorts involved. A strong password should always:
-
Be comprised of at least 8 characters at an absolute minimum. The longer the password, the better, and Windows Vista supports user account passwords up to 127 characters in length.
-
Include both uppercase and lowercase letters.
-
Include numbers.
-
Include at least one (but preferably a few) special characters such as the following:
` ~ ! @ # $ % ^ & * ( ) _ + - = { } | [ ] \ : " ; ' < > ? . / ,as well as spaces and so on. Alt+ characters (those that require you to press down the Alt key and use number keys to access special non-ASCII characters) are also valid and a great option to increase password security.
If you follow these suggestions your password will be difficult for others to guess. However, going above and beyond the suggested minimums makes for an even stronger password, and one that will be exceptionally difficult for even the most advanced hacking tools to compromise. In other words, an 18-character password that includes both upper-and lower-case letters, a couple of numbers, and a few different symbols should keep your account well protected from malicious users commandeering even the latest and greatest hacking tools.
Although the complex 18-character password sounds great in theory, it's not hard to imagine how difficult it can be to remember, especially if chosen randomly. The password Y6 we)+Av*f6jJcvsI45 is certainly strong, but will do you little good if you can't remember it.
One of the easiest ways to create a strong password is to make it a derivative of something you'll remember. For example, if you often find yourself daydreaming about bass fishing, consider a password like NxtGR8*Trp4~Bas5. Loosely, this would translate to something you could remember, like "next great (fishing) trip for bass". Every element of an industrial-strength password is there: upper-and lower-case letters, a few numbers (replacing similar-looking or - sounding letters), and a couple of symbols thrown in for good measure. Remembering a password like this is surprisingly easy after typing it a few times, especially if it's related to something you're interested in or looking forward to.
Common Password Mistakes
If you follow the advice about creating good passwords, you're already on the right track. However, there are still a few common password pitfalls that you'll want to avoid.
A strong password should never:
-
Include any part of your username or full name, or the names of friends, family members, places, and pets that would be easy for others to guess.
-
Include personal information such as your birthday, phone number, address, tax identification number, or other potentially sensitive personal/family/business information.
-
Be the same as (or similar to) any other password you use.
-
Be comprised of regular English-language words, phrases, or acronyms.
| Caution | Hackers know that most people use weak passwords, and usually ones based on personal information. The sad reality is that far too many users rely on easily guessed details (child and pet names, favorite sports team, and so on) to protect even their most confidential user accounts. If you've fallen into this common trap, don't panic. Instead, make a point of changing all your passwords to strong, secure alternatives today. |
Additionally, to keep your passwords strong, never:
-
Share your passwords with anyone, including friends and family.
-
Use the same or similar password for different user accounts.
-
Write your passwords down in a way that it will be accessible to other users.
-
Use the same password for any extended period of time.
| Caution | Never provide a password when asked for it by others, or share it with friends. Passwords are like the PIN numbers associated with bank or credit cards, and should be treated in the same way. If you ever feel like any of your passwords has been compromised, change it immediately. |
You may feel as though you've come up with a suitable and brilliantly strong password, but it never hurts to take it for a test drive. Although there are many different programs designed to test password strength, you can also gauge the strength of your passwords on the http://www.SecurityStats.com web site. This site includes a tool that enables you to input your proposed password, and then scores it against a number of password best practices.
To test a proposed password with this tool, follow these steps:
-
Click Start → Internet Explorer (or open your preferred web browser).
-
In the Address bar, type http://www.securitystats.com/tools/password.php and press Enter.
-
Enter a variation of your proposed password in the text box on this page. Don't use the exact password that you intend to use, but rather one that is similar. For example, if the password whose strength you want to test is NxtGR8*Trp4~Bas5, enter something like MjtFG4*Rto3#Das9.
-
Click Submit. The password will be analyzed and then rated as shown in Figure 3-1. If necessary, use the suggestions provided on this page to help you create a stronger alternative password.
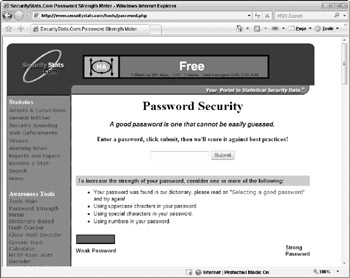
Figure 3-1: The Password Strength Meter is a free testing tool at http://www.SecurityStats.com.
Perhaps the most common reason why many users don't take password security as seriously as they should is that they don't believe that anyone would be interested in their personal information or communications. In other words, their computer (or their online user accounts) contains nothing of intrinsic value to others.
Unfortunately, these users are amongst the primary targets for hackers, spyware programs, and viruses. Every PC contains useful information about its users, from details such as credit card numbers to private e-mail messages. Ultimately, this information can be used for purposes as malicious as identity theft, blackmail, and spying, to more innocent activities like displaying targeted on-screen advertising messages.
These issues have become especially prevalent of late with the wildfire-like spread of spyware programs and dangerous viruses. Many of these pests are designed to steal personal information from your PC and then forward it to servers on the Internet without your knowledge. Others are even more dangerous in that they install programs that allow others to access and control your PC remotely, or capture each and every one of your keystrokes, making everything you type potentially accessible to hackers or other malicious third parties.
It's been estimated that up to 90 percent of all home and small office computers are infected by spyware and other similar exploits. If even a very small percentage of these systems have dangerous remote control programs or keystroke loggers installed, that's very bad news indeed. If you suspect (or know) that one or more of these pests has infected your computer, it's important to completely remove them, and then immediately change the passwords associated with all of your sensitive user accounts. If you don't, you're running the risk that someone out there on the Internet may already have complete access to some or all of your user accounts.
| Cross Reference | You'll learn more about protecting against virus threats in Chapter 9, and fighting spyware and related issues in Chapter 10. |
Changing Passwords Regularly
Creating strong passwords for your user accounts is critical; not letting them get stale as a result of prolonged use is equally important. As a rule, make a point of changing all important user account passwords regularly, say once every 30 to 90 days. Changing your passwords more frequently helps to improve overall user account security, whereas using the same passwords for extended periods increases your risk exposure. Later in this chapter you'll learn how to configure Windows Vista (Business, Enterprise, or Ultimate edition) systems with password policy settings to enforce more secure user account password practices.
| Note | When they feel comfortable with a password, most users will go to great lengths to avoid changing it. Perhaps human nature is to blame, but think of the process as being similar to eating your vegetables or taking your vitamins. Even though some may not taste all that appealing to begin with, they're good for you. The same can be said for passwords - although changing frequently may seem like a terrible pain, you'll be better off (security-wise) in the long run. At the end of the day, the pain associated with a serious breach of your personal privacy is much worse than the brief pinch experienced when the time to change passwords arrives. |
EAN: 2147483647
Pages: 135