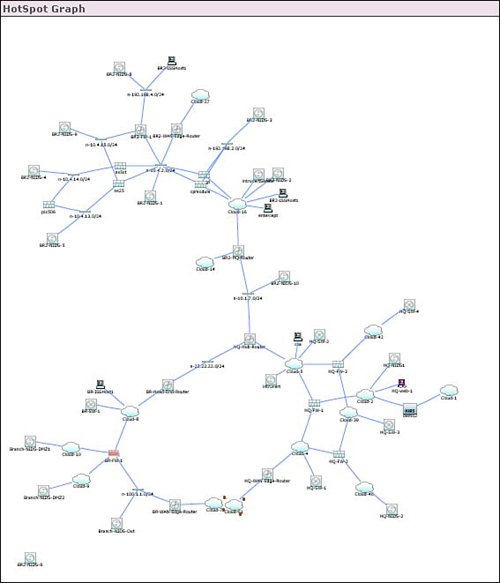
Incidents
| The focal point of the Cisco Security MARS dashboard is a list of recent incidents. In addition to the dashboard, incident information is also available by selecting the Incident tab at the top of the Cisco Security MARS GUI. All incidents are supplied with an incident ID, event type, matched rule, time, and path information. Figure 10-2 provides an example of an incident ID selected from the dashboard (highlighted). In addition to selecting an incident from the Summary Dashboard, incidents can also be selected from the Incident tab at the top of the Cisco Security MARS GUI. Figure 10-3 displays the resulting information from the incident selection in Figure 10-2. Figure 10-3 also provides an example of how an incident is displayed with the matching rule that triggered the incident and the subcomponents of the incident. Subcomponents of the incident include the following fields:
Figure 10-2. Select Incident from Dashboard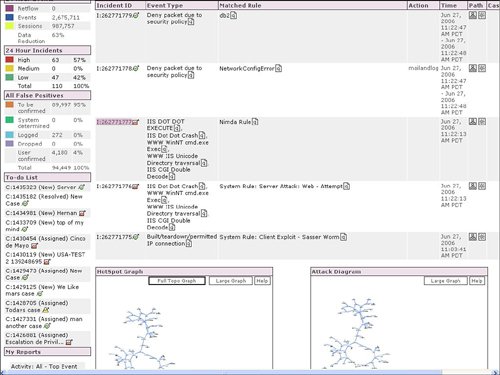 Figure 10-3. Incident Details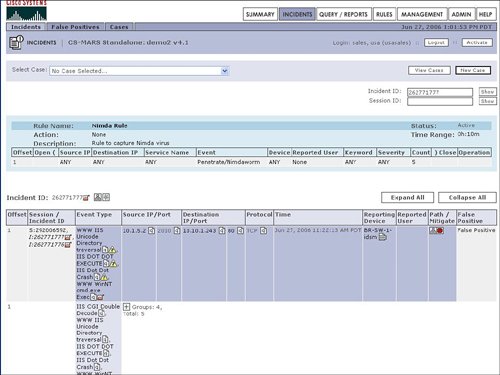 Cisco Security MARS displays security incidents to the user that may require action as opposed to simply providing a real-time viewer of IDS and firewall events. In addition to providing high-level security incidents to the user, another powerful feature of Cisco Security MARS is the ability to recommend or apply a mitigation action to stop the incident or attack. Displaying Path of Incident and Mitigating the AttackFigure 10-3 displayed details of the security incident for a Nimda worm. Selecting the red icon in the Path/Mitigate field for this incident results in the display of the path of the network attack. Figure 10-4 provides the resulting display of the path of the security incident through the network. Figure 10-4. Path of Incident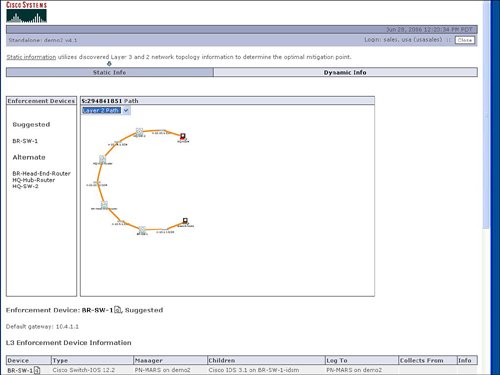 In addition to displaying the path of the network attack, Cisco Security MARS can also generate the command-line interface (CLI) commands to mitigate or stop the network attack. The CLI commands used to mitigate an attack are displayed with the path by selecting the path/mitigate option in the incident. Cisco Security MARS has the ability to automatically shut a LAN port to mitigate the attack. Cisco Security MARS will generate the CLI for an access control list (ACL) rule to stop an attack, but will not deploy the CLI. The suggested CLI recommendation is typically based upon the device closest to the source of the attack. This choice may not be the optimal mitigation point based upon the user's point of view. Cisco Security MARS allows the selection of alternate devices within the path of the network attack in case the user does not wish to mitigate the attack at the device that is closest to the source of the network attack. Figure 10-5 displays the suggested CLI to configure an access list to stop the Nimda attack. Figure 10-5. Suggested CLI to Mitigate the Attack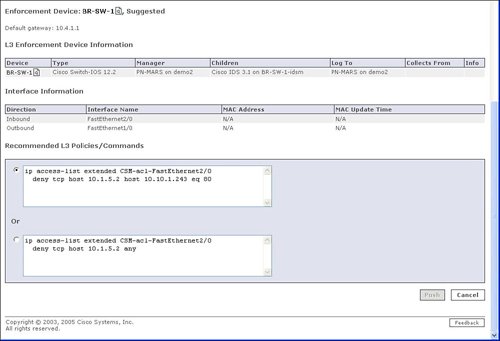 Hotspot Graph and Attack DiagramCisco Security MARS relies heavily on SNMP to gain topological awareness of the network. Cisco Security MARS requires SNMP read access to construct a Layer 3 and Layer 2 topological map of the network. Cisco Security MARS uses Simple Network Management Protocol (SNMP) to gather information about the device. Cisco Security MARS also uses SNMP and a seed device to discover the neighboring devices for each known device in the network. A seed device is a starting device to discover the network by attempting to discover every device known by the seed device and then attempting to discover every device known by each newly discovered device. SNMP allows Cisco Security MARS to create the hotspot graph and the attack diagrams. Use of SNMP by Cisco Security MARS is complemented by the integrated network scanner. The integrated network scanner is used to gain information about the hosts and applications that exist on the network. Cisco Security MARS combines the device discovery of SNMP with the scanning information about the hosts and applications to construct the hotspot graph. Cisco Security MARS uses the host scanning for OS and application fingerprinting. OS and application fingerprinting is used to assist in ensuring that an incident is relative to the target and valid. For example, a detected Windows exploit attack against a Linux server is not a valid incident. Both the hotspot graph and the attack diagram can be displayed on the main Cisco Security MARS dashboard. Figure 10-6 provides a sample of a hotspot topology graph. In our example, the hotspot diagram displays the network for the Nimda incident on the dashboard. Figure 10-6. Hotspot Graph The hotspot graph displays the path of the incident or attack across the network. An attack diagram allows the user to highlight a vulnerable path between two points in the network and receive a display of the session IDs of the events that are incorporated into the security incident. Figure 10-7 provides an example of an attack diagram for the Nimda incident. Both the hotspot graph and the attack diagram are launched from the icons next to the incident ID from the details on the incident. The hotspot graph and attack diagram on the dashboard typically correspond with the latest incident listed on the dashboard. Figure 10-7. Attack Diagram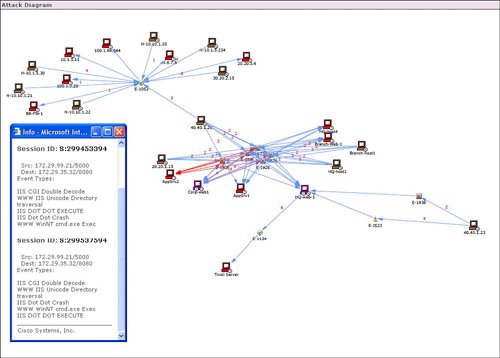 |
EAN: 2147483647
Pages: 112