Workstation Imaging Policy
ZENworks for Desktops 4 has the capability to image a workstation and then to apply that image back to the original or other workstations. See Chapter 14, "Imaging a Workstation," for more detailed information on the functionality of the ZENworks for Desktops 4 imaging system. The placement of an image associated with an Image object in the directory onto a workstation can occur three ways in ZENworks for Desktops 4.
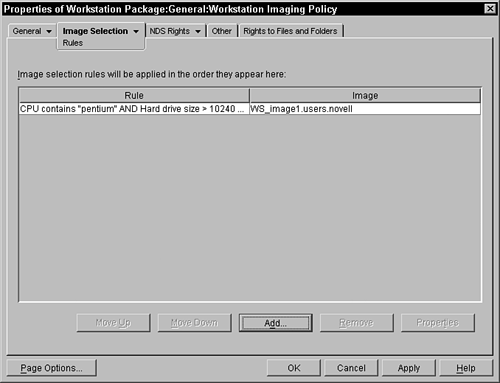
Each of these ways results in the workstation being imaged with the image associated with the workstation or determined by the imaging agent that resides on the server. The way that the workstation finds the imaging server is when the imaging boot diskettes are created, the administrator can specify either an IP or a DNS name for the server. This information is saved on the diskettes or in the special boot partition. The Workstation Imaging Policy comes into effect if the workstation is to be imaged and there is no image associated with the workstation object and the policy is activated. This policy enables the administrator to create a set of rules that can govern when a particular image should be used, based on some basic information from the workstation. The imaging server follows the list of rules in the policy until one of the rules is satisfied. The rule that is satisfied results in an associated image that is then applied to the workstation. Rules PageThis page enables the administrator to input the rules and associated images that the system uses to determine the image to place on a specific type of workstation. Figure 9.9 shows a sample of this page. Figure 9.9. Rules page for a sample Workstation Imaging Policy of a Workstation Policy Package.
You must first press the Add button to add rules to the list. Once you have added several rules, you can then select a specific rule and change its order in the list, look at its properties, or remove the rule. When you choose the Add button, a dialog box appears, in which you add the rule to the policy. Use the browse button next to the Use this Image field to browse to an image object in the tree that is associated with an image file on the image server. Once the image object is selected, you can identify the rule that is associated with this image. You can currently have six key/value pairs about the workstation to compare in order to determine which image to use. In the middle of this dialog box, you can see the six potential equations that you can generate to determine whether the image should be used. The equation is made up of a series of True/False statements that are combined with AND and OR logic. You construct the statement by filling in the drop-down statements. (The resulting statement is displayed in a more English-like view to help you understand the equation.) The logic for the AND and OR operators is strictly left to right in the equation. In the Rule Description box, parentheses are added to the equation to help the administrator understand how the rule is evaluated. You cannot insert the parentheses; they are automatically inserted and are not under user control. Select the key you want to examine via a drop-down dialog box. The keys that you can choose from are the following:
When the workstation is booting the imaging system, it is in reality booting up the Linux operating system and running the tools that are included in the imaging system. The values for the keys described previously are values that the Linux system can report to the software. In order to discover what a system reports to Linux, you need to boot a sample workstation with the Imaging system boot disk and run the Img information command. This displays the information that is sent to the image server about the workstation. This information includes the data values that you put into the key comparison equations for your rules. You can also get this information from an image by opening the image in the ZENworks image editor and choosing properties on the image root. See Chapter 14, for more detailed information on the functionality of the ZENworks for Desktops 4 imaging system. The next step of the equation involves specifying the operator. Two types of operators exist: String and Integer operators. The Hard drive size and RAM fields are treated as integers, whereas all of the other fields are treated as strings. A case-insensitive string compare is performed to determine operator results. The string operators are contains, doesn't contain, begins with, and equals. The integer operators are =, <>, >, >=, <, and <=. These operators perform expected comparisons between the key value supplied by the workstation to the imaging server and the value that you place into the value field of the equation. The following meanings are placed with each operator:
The next field in the operation is where you enter the value that you want to compare. The far right field enables you to extend the operation to additional key/value comparisons. Your choices currently are AND and OR. The Boolean operators are evaluated strictly from left to right. For example if the following rules were entered into the policy:
The resultant evaluation would be (Hard drive < 60MB AND RAM < 16 MB) OR (RAM > 31MB). This would result in giving the image to any system that has a disk smaller than 200MB with less than 16MB of RAM. This would also give the image to any system that has more than 31MB of RAM regardless of the size of the hard drive. You can view the precedence of the equation; complete with parentheses, on the bottom half of the screen as you introduce new key/value pairs into your rule. Once your set of key/value pairs have been entered and you have reviewed your equation at the bottom of the screen, you press the OK button to include the rule into the imaging system. You are returned to the original Rules page with the rule that you had entered placed on the screen. Once again, from this page, after you have entered some rules you can then specify the order in which the rules are evaluated. After selecting a rule you can move that rule in the order by pressing either the Move Up or the Move Down buttons. As the imaging server is evaluating the rules, the first rule that results in a TRUE evaluation results in that imaging being supplied to the workstation. |
EAN: 2147483647
Pages: 198