Configuring Shared Services
After you have installed an SSP, its configuration is performed from a dedicated, isolated administration interface. This interface can be reached from Manage This Farm's Shared Services page, as shown in Figure 8-10 or, alternatively, can be bookmarked in the browser for future administration.
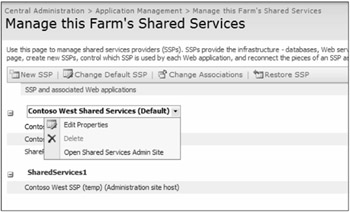
Figure 8-10: Select the drop-down menu and click on Open Shared Services Admin Site to configure an SSP.
On entering SSP administration, notice that it is simply another site collection based on a highly specialized template. Although it can be modified like any other site collection, doing so is generally a bad idea and can cause issues down the road. For that reason, only modify settings, such as security, that will not be affected by future service packs and releases.
Assigning Administrators
After creating an SSP, you must assign administrators to the site collection for management. By default, farm administrators do not have access, unless defined during SSP creation. You can manage users and groups for an SSP in the same way as any other site collection. Refer to Chapter 4, "Creating Site Collections," for more information on managing users and groups.
Managing User Profiles
Managing user profiles and properties is fundamental to managing and surfacing personal information about your users. User profiles are associated with one or many Active Directory accounts and have an associated My Site if enabled. You can map profile properties to almost any authentication provider, including Active Directory objects, third-party LDAP providers, and database authentication providers. In addition, you can give users the ability to surface any information they choose. This section explains how giving users the ability to manage their profiles can assist when creating audiences for the purpose of targeting.
A user profile contains the following elements:
-
Personal Site information
-
Primary Active Directory account
-
First name
-
Last name
-
Name
-
Customizable fields
You can manage the customizable fields provided or add as many custom fields as required by your organization.
Defining Import Sources and Connections
Before user profiles are available for use, you must define the source for your user profile imports. Although you can create user profiles manually, most organizations have at least one default import source, which is usually the Active Directory. You can define additional import sources from any LDAP version 3 or later, Active Directory, Business Data Catalog connection, or a single OU in an Active Directory forest.
Setting the Default Import Source
Most organizations define their primary Active Directory Forest as the default source for their user profile imports. You can define the default import source from either Shared Services Administration > User Profiles And My Sites > User Profiles And Properties > Import Source, or Configure Profile Import, as shown in Figure 8-11.
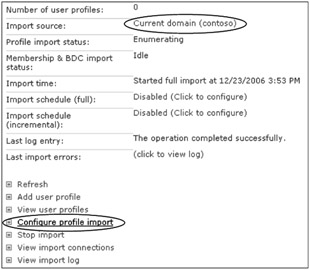
Figure 8-11: You configure the default import source from Profile And Import Settings.
You can define the profile import source as a domain, forest, or custom source. In a small to medium environment, most likely you will choose between a domain or forest. If all of your users are in a single domain in a forest, then it doesn't matter which you choose. However, if you have users in multiple domains within a forest, selecting Entire Forest eases the burden of creating an import connection for every domain. Be aware that all accounts, including services and administrators, are imported and that an associated user profile is created for each one.
Configure the import source from Configure Profile Import, as shown in Figure 8-12. You can only select one import source from this interface.
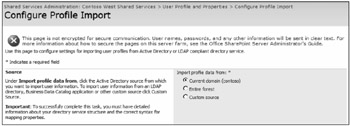
Figure 8-12: Select Current Domain or Entire Forest to define an import source.
The following items must be configured to successfully define the default import connection:
-
Source As discussed, the source can be the Current Domain, an Entire Forest, or a Custom Source.
-
Default access account The default access account that is used to connect to the defined LDAP and import user profile data is the default Search Content Access Account. It is recommended that you change this account and not use the default access account because it could be modified by another administrator, effectively disabling user profile imports from this source.
-
Full import schedule You have very granular control over how your profiles are imported. If your environment isn't changing rapidly, consider a monthly or longer Full Import Schedule. After the initial import is completed successfully, you should only need to run a full import after changing the access account or source or if you suspect the user profile index is corrupted.
-
Incremental import schedule Incremental imports are meant to import the delta from the last incremental or full import. Most organizations set this schedule to daily or weekly, depending on the rate at which your Active Directory changes. Keep in mind that user profile imports do more than just populate added users; properties, such as phone numbers and managers defined in Active Directory, are also updated.
Configuring Custom Import Sources
To configure custom import sources, whether they are Active Directory or other, browse to Shared Services Administration > User Profiles And My Sites > User Profiles And Properties and select View Import Connections, as shown in Figure 8-13.
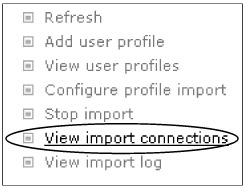
Figure 8-13: To view and create import connections, select View Import Connections.
The default import connection should already be listed with the type, source, Search Base, and Active Directory throttling status (Server Side Incremental). You can edit an existing source by hovering the mouse over the drop-down menu or create a new one by selecting Create New Connection. To create a new connection other than a Business Data Catalog (BDC) connection, you must configure the following items.
-
Type You must specify the type of connection you are creating-Active Directory, third-party LDAP, Business Data Catalog, or Active Directory Resource. Depending on which type you select, you are presented with a different set of parameters.
The Business Data Catalog is beyond the scope of this book. For more information on configuring the BDC user profile properties, see http://msdn2.microsoft.com/en-us/library/ms585895.aspx.
-
Connection name If you select LDAP or Active Directory Resource, you must input a connection name. This name enables multiple connections to individual containers/resources inside these LDAP directories. Because an Active Directory connection includes all username attributes therein, a connection name is not required.
-
Domain name When selecting Active Directory as the import source, you must define the domain name for the connection. You have the option to auto-discover the domain controller (preferred), or if you have a specialized installation, you may specify a domain controller. This second option may be necessary when your server farm exists in a screened subnet and you want to localize Active Directory traffic to that subnet. If you specify a domain controller, be aware that user profile imports and updating will cease if that domain controller should fail for any reason.
Note A good situation in which to use multiple Active Directory domains is when your server farm is located in a resource forest, with no generic user authentication accounts. In this model, you set up an import connection (source) for every domain in which your authentication accounts reside. Doing so limits the visibility of your resource forest accounts.
-
Directory Service name If you are establishing an import connection with a third-party LDAP, you must define the server name hosting the directory. Because auto-discovery isn't enabled for third-party LDAPS, this server needs to be documented to prevent user profile import failures, should it cease to function.
-
TCP port /SSL You also need to define the port and select whether to use SSL. Once again, using SSL may be necessary if your server traffic will traverse public networks. The default ports work for most installations.
-
Server Side Incremental Choose Server Side Incremental if you plan to schedule incremental profile imports. This feature reduces the overhead of your domain controllers when performing frequent imports.
Caution If you enable Server Side Incremental in conjunction with a Windows 2000 Server Active Directory, the content access account must have the Replicate Changes permission.
-
Master forest connection settings (Active Directory resource only) When specifying an individual resource in an Active Directory for user profile imports, you must define the connection parameters:
-
The domain name should be the Forest root domain.
-
Auto-discover the domain controller when possible; otherwise specify the single domain controller to use.
-
The default LDAP port is 389; the default SSL-secured LDAP port is 636.
-
Specify the account with sufficient permissions to import user profiles. Use of the default account is discouraged.
-
-
Provider name (LDAP only) If you use a third-party LDAP for user profiles, you must enter the provider name.
-
Username attribute If you are using Active Directory, you cannot specify the username attribute because it is always distinguishedname. If you are importing from a third-party LDAP, however, you need to define the username attribute, which is usually uid.
-
Search settings You can auto-fill the root search base or enter one manually. If you are targeting a subtree item in the directory, you need to append the auto-filled root search base with the targeted OU, as an example. You may further limit the objects imported by selecting the user filter and scope.
Tip You can further limit the performance impact on your domain controller(s) by specifying the page size and page time out settings. But, if these are too restrictive and you have Server Side Incremental enabled, you may get erratic import results.
-
Authentication By default, the access account is the account specified for content search and indexing. Using a dedicated account is recommended for stability and security. This account can be audited and limited as required.
Once you have configured custom import sources, you must use the View Import Connections interface for all future import sources. Selecting either Domain or Entire Forest deletes all Custom Sources you have defined.
Viewing Import Log
This version of SharePoint Server brings a robust crawl log capability. The full description of this functionality is provided under Search and Indexing administration, but it is worth noting that you can view the profile import log from Shared Services Administration > User Profiles and Properties > View Import Log. This interface allows you to filter based on Content Sources (import connections), date, status type, and status message. If you have errors during importing, consider increasing the verbosity of the logging in Central Administration > Usage Analysis, and view the logs for import errors.
Modifying User Profiles
To view an existing user profile, browse to Shared Services Administration > User Profiles And My Sites > User Profiles And Properties. Select View User Profiles, as shown in Figure 8-14. This can only be done after performing at least one profile import.
Figure 8-14: After importing user profiles, you can view individual profile details by selecting View User Profiles.
Select the View User Profiles hyperlink to see existing user profiles. If you have several hundred or thousands of user profiles, you can filter the user list using the drop-down menu shown in Figure 8-15.
Figure 8-15: Filter the list based on criteria that best fit your environment.
To edit an account, select Edit from the profile's drop-down menu. From here, you can directly edit properties that are used in My Sites and Global Audiences (SSP Audiences). Policy restrictions, such as changing the Show To group, are limited here for any user in his or her My Site, including administrators. Notice that you can manage personal sites from here in conjunction with editing profile details.
From the same management interface, you can also create a new profile; however, the user must have an account in the directory. You can modify all available user properties. You might manually add a profile to a remote LDAP directory or when repairing user profiles in between profile imports.
Configuring User Profile Properties
User profile properties are used throughout your SharePoint Server farm for functions, such as search scopes and audiences. SharePoint Server 2007 ships with a number of profile properties, but also populates the available properties when crawling import connections (sources). You can create custom profile properties and map those properties to custom attributes in your connected LDAP directories. Profile properties are a very powerful way to expose personal information about individuals in your organization, such as skill sets and personal interests. This information can be indexed or included in audiences, thereby surfacing critical institutional knowledge. For example, you could index a profile property that collected critical skills information, such as database administration. By indexing this information, you can then search for all individuals with that skill set. By default the following sections are included:
-
Details
-
Contact Information
-
Custom Properties
You may add additional sections to ease management of properties by selecting New Section and completing the required information.
Adding New Properties
You can create custom properties, perhaps for divisional or subsidiary information. These can be fields that are mapped and imported from an LDAP directory or specified by the user. New properties are useful when creating search scopes and creating audiences. For example, you might create a property named Division and map it to a correlating attribute in Active Directory. This could then allow you to create a search scope to only search documents by people in a single division. To create a new property you select Add Profile Property, as shown in Figure 8-16. You can also create a new property from User Profile Properties, as shown in Figure 8-17.
Figure 8-16: Select Add Profile Property from the User Profiles Properties interface.
Figure 8-17: Select New Property from the View Profile Properties interface.
As you select and deselect options in this interface, the page will post back. After the page refreshes, the available options change. These changes will be noted as the options are defined.
-
Name The name cannot be changed, so take due care when naming user properties. Your organization should define a common naming structure to make managing user properties easy. The name must meet the specifications of RFC2396; that is, it must start with a letter and cannot contain spaces or special characters, except ".", "+", or "-".
-
Display name The display name is for ease of identification and is not subject to the same restrictions as Name. The Display name should be easily identified by users and administrators for it to be useful.
-
Edit languages You can only have one property Name, but you can associate many language-specific Display Names with the property Name. This feature allows users to see the Display Name of the property in their language. To add language-specific Display Names, select Edit Languages. On opening the page, you have the ability to Add Language, edit an existing entry, or delete a current entry, as shown in Figure 8-18.
-
Type Numerous property types are available; the following list details all options.
-
String is the most common property type. It can be a combination of any characters, but cannot be longer than 400 characters. String is the only possible property type if you wish to allow multiple values.
-
Big Integer allows only whole numbers, with no decimal. The length is not configurable. The field must be in the range of -9223372036854775808 to 9223372036854775808, or the user will get an error populating the field.
-
Binary property types can only be mapped to a directory attribute. It is useful for mapping user IDs and other security IDs (SIDs). The length must be in the range of 1–7500.
-
Boolean will show a check box that the user can select for Boolean search function.
-
Date provides an entry for a valid date and a calendar drop-down menu for date input. It can be used for user input or mapped to a directory attribute, such as account expiration. Figure 8-19 shows an example of what the property looks like when enabled for user input.
-
Date No Year requires user input in the form of Month ##, for example, March 15.
-
Date Time provides the same drop-down calendar as Date, but also includes drop-down controls for the hour and minute. Figure 8-20 shows an example of a Date Time property in a user profile.
-
E-mail simply requires an @ symbol in the entry. There are no other checks in place for this property.
-
Float provides a method for gathering floating point numbers. It does not accept non-numerical characters, and its length is limited to 50, which is not configurable.
-
HTML allows user entry of HTML code, up to a length of 3,600 characters. It also provides a rudimentary in-screen HTML editor. Figure 8-21 shows an example of the editor included with the HTML property.
-
Integer is similar to Big Integer, except that the acceptable range is -2147483648 to 2147483647.
-
Person provides user entry requiring a match to a user in the directory. It also provides a name checker and the People Picker, as shown in Figure 8-22.
Tip If you see the database-link icon, as shown in Figure 8-23, the property is mapped to a directory attribute.
-
Unique Identifier should only be used to map the unique identifier associated with an account in the directory service.
-
URL forces user entry in the form of ftp://, http://, file://, or https://, appended with the server host.
-
-
Allow multiple values Multiple values can only be selected when choosing a property type of String. You must also define the value separator, either "," or ";".
-
Allow choice list To allow a choice list, you must once again choose the property type String. After checking Allow Choice List, the screen posts back, and Choice List Settings appears further down the screen, as shown in Figure 8-24.
-
User description The description can be changed any time during or after the property creation. The description annotates the property field and can be used to instruct users on the proper naming conventions or may remind users of Human Resources policies. You can have several language-defined descriptions, with users seeing the description you have defined for their language. Figure 8-25 shows a sample user description.
-
Policy setting The property privacy policy setting defines the status of the property and whether or not valid data are required for the property. If the policy setting is set to disabled, the property is not available or visible to the user. If set to Optional, then the user can choose to leave the field blank. Conversely, selecting Required forces user valid entry into the field before saving the profile.
-
Default privacy setting Privacy settings define who can see the defined value of the property. Be careful when selecting Everyone when there is confidential information, such as home phone numbers. Information like Division, however, should probably be viewable by everyone. It is not possible to add groups of users to the default choices.
-
User override If you do not select User Can Override, then the property privacy setting cannot be changed by the user. If you wish to allow your users to change the privacy settings for this property, select the override check box. Figure 8-26 shows the difference between a property privacy policy allowing user override and one that does not.
-
Replicable If you wish to replicate this property as user information for all site collections, you must select Replicable. To replicate a user profile property, the policy setting must be enabled, the privacy setting must be configured for everyone, and User Can Override cannot be selected because doing so would break the replication.
Important If you later choose to turn off Replicable, be aware that previously replicated user data to site collections are not removed.
-
Edit settings Allowing users to edit settings allows them to change the field at any time. Although this ability is useful for some items, such as skill sets, you never want to allow the editing of properties mapped to your LDAP or Active Directory. For example, if you have defined the attributes division and manager in Active Directory and mapped those to properties in the user profile, you do not want the users overwriting this information because it will be overwritten in the next import.
-
Display settings To show a profile in the properties section of the user's profile page, you must select the default privacy setting of Everyone. This setting makes this option available for the users to show on their My Site. You can also choose to see the property on the edit details page, and show changes in the Colleague Tracker Web Part.
-
Choice list settings (requires Allow Choice List to be checked) You can define a choice list for the users or allow users to input their own field values, as shown in Figure 8-27. To add a choice list, check Defined Choice List, decide whether to allow users to add to the choice list, and select Add A New Choice…. Alternatively, you can import choices from a text file with the values separated by a carriage return <Enter>.
-
Search settings Aliased properties are treated as equivalent to the username and user ID when searching for items authored by a user or audience targeting. You can also specify whether to index the property. Items such as home phone number may not be indexed in your organization.
-
Property import mapping You can create custom profile properties and map the field value to an attribute in a connected LDAP, such as Active Directory. There are 22 default values already mapped, including account name, work number, office, department, and title. You can add to these fields such values as division, language, nationality, and so forth. Map these properties back to attributes defined in your Active Directory.
Tip You can change the order in which the properties are displayed to the user by selecting the up or down arrows, as shown in Figure 8-28. If you need to move an item several spaces, it can be very time consuming.
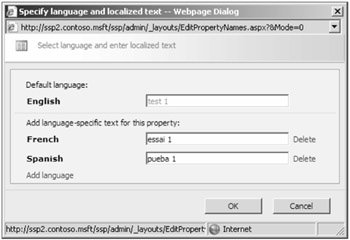
Figure 8-18: You can add, modify, or delete language-specific display names from a user-friendly interface.
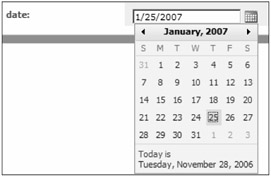
Figure 8-19: The Date property allows user input through a drop-down calendar control.
![]()
Figure 8-20: The Date Time property shows the hour and minute drop-down controls.
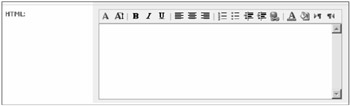
Figure 8-21: The HTML property type provides an HTML editor for user entry.
![]()
Figure 8-22: The Person property requires a valid user from the directory service to be entered.
![]()
Figure 8-23: The database-link icon represents a mapped directory property.
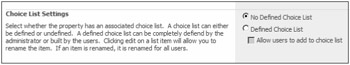
Figure 8-24: The Choice List Settings menu only appears after selecting Allow Choice List.
![]()
Figure 8-25: Use the user description only when necessary because it increases the size of the page.
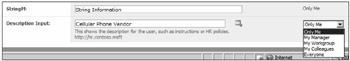
Figure 8-26: The example of a custom property, StringM, does not allow the user to change the privacy setting, but Description Input allows the change through the privacy setting drop-down.
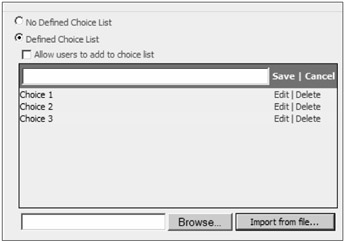
Figure 8-27: Check Defined Choice List and select Add A New Choice… to add choices.
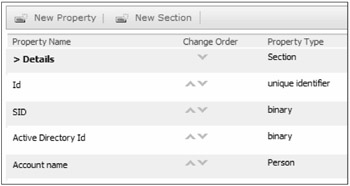
Figure 8-28: To change the order of a property, select the up and down arrows.
You can edit existing properties, but many fields, such as type, policy settings, and name, are locked. You cannot change fields such as Name and Type, but you can always change the Display Name, add languages to Description and Display Name, and modify the directory mappings.
| Note | You can manage all user profile property policies from a single location in Shared Services Administration > User Profiles and My Sites > Profile Services Policies. |
Using Personalization Services
Although much of SharePoint Server's personalization occurs in the My Site configuration, some is configured for all users who connect to Web applications associated with an SSP. You can personalize the views of My Site horizontal navigation bar (Top Link Bar) and define Save As locations for Office applications.
Published Links to Office Client Applications
To publish links to Office applications such as Word or Excel, you must select Published Links To Office Client Applications in Shared Services Administration, as shown in Figure 8-29. The users will then have this location as an option in the Office application Save As menu.
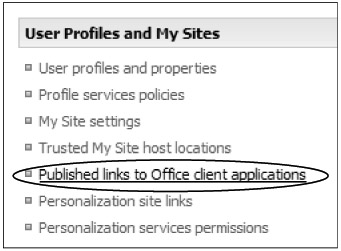
Figure 8-29: To publish links to Office client applications, select the administration link.
Personalization Site Links
Personalization site links provide an easy method to provide important information to your users. You must specify a Web address, owner, and description, but be aware that the description is the Top Link Bar name. If you wish to target a specific audience, you can use Global (this SSP) audiences or Active Directory distribution and security groups. Figure 8-30 shows an example of a My Site with a Top Link Bar tab name. This is the portal home that can be used for instant navigation.
Figure 8-30: The description shows as the tab name on the Top Link Bar.
You can use this as a quick navigation method for internal or external sites, such as expense reports, news, human resources policies, or whatever your specific needs may be. Be aware that having too many tabs makes the screen cluttered and less user friendly. Using audiences makes the user experience much better.
Configuring Audiences
Audiences created in Shared Services Administration are also referred to as Global Audiences. Be aware that these are not truly global because they will only exist in a single SSP; therefore only the intra-farm Web applications that are associated with this SSP or Web applications in an inter-farm shared services arrangement will be able to find and use them. You may also target audiences from site collections using Global Audiences, Active Directory security and distribution lists, or SharePoint site groups.
Creating Audiences
To create an SSP audience, enter the Audiences management interface from Shared Services Administration. By default, there is only one audience created, and it is named All Site Users. To add new audiences, select the New Audience tab, as shown in Figure 8-31.
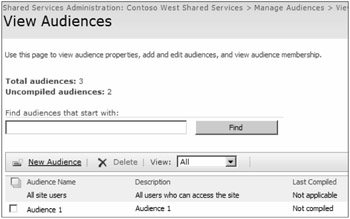
Figure 8-31: Select the New Audience tab to create global audiences.
-
Name You must name your audience. Use care when creating audiences because your users will use them to target content. Changing this name after the fact can break your site collection functionality.
-
Description The description is optional, but is a good idea. Letting your users know what the details of the audience are, such as Top Level Managers, can keep the need-to-know purpose of audiences intact.
-
Owner You must specify the owner of this audience. This owner can change the rules, so be careful to whom you assign the role.
-
Rules Two choices are available.
-
Satisfy All Of The Rules requires that every rule defined for the audience be met before users are added. If this is too restrictive, you may not have members in your audience!
-
Satisfy Any Of The Rules is used more often; it allows for any combination of the rules to be met in order to insert a member into this audience. However, remember that an issue with a poorly created rule set can result in an audience that is much larger than expected.
After choosing OK, you are taken to a screen to begin creating rules. Although you can create multiple rules for a single audience, you can only create one per screen. You have two options for the operand in a rule: User or Property. Select the User operand when defining distribution or security groups or possibly the management hierarchy in your organization. Selecting Property as your operand allows you to create audiences based on any of the custom properties defined in your user profiles.
-
-
Add rules You can add rules at any time. To add a rule, browse from Shared Services Administration to Manage Audiences > View Audiences > Audience Rules and select Add Rule. You may add as many rules as you like, but you should always view the membership after compiling to verify you have the correct end result.
Using Audiences
It is very important to understand that audiences are not a security authorization mechanism. They are simply a way to present applicable information to users by targeting relevant information in an interface. You can limit the viewing of almost anything in this version of SharePoint Server, including Web Parts, documents, lists, Top Link Bars, and much more. Your users can also take advantage of these audiences in lists and document libraries.
Office SharePoint Usage Reporting
Usage analysis processing is used to report how sites are used, including their files, users, bandwidth, and more. To enable usage analysis processing, you must first enable Windows SharePoint Services processing in Central Administration. Figure 8-32 shows where to enable this in Central Administration > Operations > Logging And Reporting > Usage Analysis Processing. You may also enable search query logging to run reports on search and indexing.
Figure 8-32: You must enable Usage Analysis Processing in Central Administration before you can enable SSP usage reporting.
EAN: 2147483647
Pages: 110