How Are You Putting Yourself at Risk?
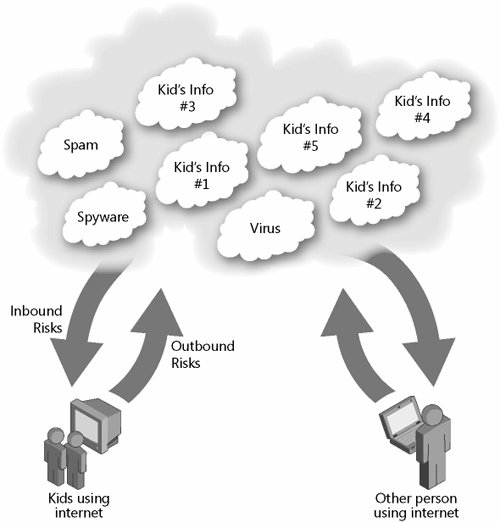
| You are in danger on the Internet from two directions: inbound and outbound (see Figure 1-1). Spam, viruses, and spyware flow toward you through e-mail, instant messaging (IM), Web sites, and so on. They can be downloaded onto your computer without your knowledge. There is much you can do to protect yourself from these threats, and most online security books focus on this kind of defense. (See "Technology Toolkit" in Part Four for my basic advice about implementing technical protections.) Figure 1-1. Risk flows both ways online.
Perhaps more dangerous are outbound risks; these occur when you willingly (though often unwittingly) reveal information about yourself through the data you put online every day. You might be providing the very information cybercriminals need to take advantage of you. Outbound risk is the focus of this book. One of the most important things you can do to reduce your own vulnerability is to grasp this one concept: Every piece of information about you is a valuable commodity. Publically available user information has the potential to be tracked, cataloged, analyzed, and sold, both legally and illegally. The fact is that many people, particularly but certainly not exclusively children, are making available a variety of information via the Web that makes them identifiable and places them at risk every day. Find Out More For more about how to avoid giving away too much information about yourself, see Chapter 5, "Step 2: Don't Tell People More Than You Should." What kind of information are people putting out there? I'm not talking about your bank account or social security numberyou wouldn't deliberately give those to strangers any more than you would hand somebody your wallet. I'm talking about seemingly useless information about you, from your favorite book to your age, the color of your eyes, and even what makes you sad or happy. Using that information and a few facts about you, such as your name and address, a predator can find you and use key information about you to either impersonate you, steal from you, or initiate a relationship. Think about what you or your friends have shared online about you, and the people out there who might use that personal information to impersonate or approach you, and then consider these statistics:
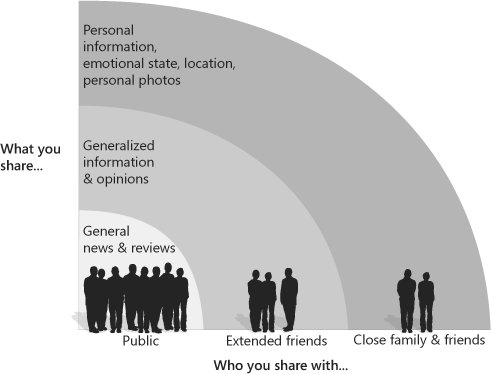
Remember that you control the level of your exposure through the information you place online. Risk is commensurate with the choices you make about the type of content you post, the breadth of contacts you make information available to, and whether you share information about others as well as yourself. The more personal the information you choose to share, the more careful you should be to share only with close friends and family (see Figure 1-2). Figure 1-2. The amount you share online should be determined by your intended audience.
Think About It Sit down and make a list of all the information about you that might interest a cybercriminal. Check off the items you've made available online in any fashion. Search on your name to see what information you can find. When you go online, think about exactly what you want to share with total strangers, and what you want to reserve for more trusted groups of people. |
EAN: 2147483647
Pages: 157