Testing, Logging, and Monitoring
| Testing, logging, and monitoring involve testing your defense strategies and detecting breaches. It's tedious, but who would you rather have be first to find out that your system is hackable: you or "them"? Your testing steps should include
You can't second-guess what 100 million potential "visitors" might do to your computer or network, but you should at least be sure that all your roadblocks stop the traffic you were expecting them to stop. Test Your DefensesSome companies hire expert hackers to attempt to break into their networks. You can do this too, or you can try to be your own hacker. Before you connect to the Internet, and periodically thereafter, try to break into your own system. Find its weaknesses. Go through each of your defenses and each of the security policy changes you made, and try each of the things you thought they should prevent. First, connect to the Internet, visit www.grc.com, and view the Shields Up page. This Web site attempts to connect to Microsoft Networking and TCP/IP services on your computer to see whether any are accessible from the outside world. Click the Test My Shields! and Probe My Ports! buttons to see whether this testing system exposes any vulnerabilities. This is a great tool. (Its author, Steve Gibson is a very bright guy and has lots of interesting things to say, but be forewarned, some of it is a bit hyperbolic.) NOTE If you're on a corporate network, contact your network manager before trying this. If your company uses intrusion monitoring, this probe might set off alarms and get you in hot water. As a second test, find out what your public IP address is. If you use a dial-up connection or Internet Connection Sharing, go to the computer that actually connects to the Internet, open a Command Prompt window, and type ipconfig. Write down the IP address of your actual Internet connection (this number will change every time you dial in, by the way). If you use a sharing router, you'll need to get the actual IP address from your router's Status page. Then, enlist the help of a friend, or go to a computer not on your site but out on the Internet. Open Windows Explorer (not Internet Explorer) and in the Address box, type \\1.2.3.4, except in place of 1.2.3.4 type the IP address that you recorded earlier. This will attempt to connect to your computer for file sharing. You should not be able to see any shared folders, and you shouldn't even be prompted for a username and/or password. If you have more than one public IP address, test all of them.
If you have installed a Web or FTP server, attempt to view any protected pages without using the correct username or password. With FTP, try using the login name anonymous and the password guest. try to copy files to the FTP site while connected as "anonymous"you shouldn't be able to.
If you are not able to view protected Web pages or folders even after providing the correct password, see "Can't View Protected Web Pages" in the "Troubleshooting" section at the end of this chapter. Use network testing utilities to attempt to connect to any of the network services you think you have blockedfor example, SNMP.
Attempt to use Telnet to connect to your router, if you have one. If you are prompted for a login, try the factory default login name and password listed in the router's manual. If you've blocked telnet with a packet filter setting, you should not be prompted for a password. If you are prompted, be sure the factory default password does not work, because you should have changed it.
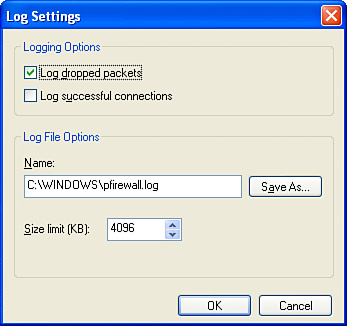
Port scanning tools are available to perform many of these tests automatically. For an example, see the Shields Up Web page at www.grc.com. I caution you to use this sort of tool in addition to, not instead of, the other tests I listed here. Monitor Suspicious ActivityIf you use Windows Firewall, you can configure it to keep a record of rejected connection attempts. Open the properties page of the firewalled connection, select the Advanced tab, click Settings, select the Advanced tab, and under Security Logging, click Settings (phew!) to get to the Log Settings dialog shown in Figure 21.2. Figure 21.2. Enable logging to see what Windows Firewall is turning away.
Inspect the log file periodically by viewing it with Notepad. NOTE If you use a dial-up connection, the firewall log is less useful. It will accrue lots of entries caused by packets left over from connections made by the dial-up customer who had your temporary IP address before you got it. They'll continue to arrive for a while, just as junk mail does after a tenant moves out. |
EAN: 2147483647
Pages: 450