Active Defenses: Blocking Known Methods of Attack
| Active defense means actively resisting known methods of attack. Active defenses include
When your network is in place, your next job is to configure it to restrict access as much as possible. This task involves blocking network traffic known to be dangerous and configuring network protocols to use the most secure communications protocols possible. Set Up Firewalls and NAT (Connection Sharing) DevicesUsing a firewall is an effective way to secure your network. From the viewpoint of design and maintenance, it is also the most efficient tool because you can focus your efforts on one critical place, the interface between your internal network and the Internet. A firewall is a program or piece of hardware that intercepts all data passing between two networks, for example between your computer or LAN and the Internet. The firewall inspects each incoming and outgoing data packet and only permits certain packets to pass through. Generally, a firewall is set up to permit traffic for safe protocols like those used for email and Web browsing. It blocks packets that carry file sharing or computer administration commands. NAT (Network Address Translation), the technology behind Internet Connection Sharing and connection sharing routers, insulates your network from the Internet by funneling all of your LAN's network traffic through one IP addressthe Internet analogue of a telephone number. Like an office's switchboard operator, NAT lets all of your computers place outgoing connections at will, but intercepts all incoming connection attempts. If an incoming data request was anticipated, it's forwarded to one of your computers, but all other incoming network requests are rejected or ignored. Microsoft's Internet Connection Sharing and hardware Internet connection sharing routers all use a NAT scheme.
The use of either NAT or a firewall, or both, can protect your network by letting you specify exactly how much of your network's resources you'll expose to the Internet. Windows FirewallOne of Windows XP's new features is the built-in Windows Firewall software. Windows Firewall was introduced in Windows XP Service Pack 2 to replace the more primitive "Internet Connection Firewall" that originally shipped with XP. (Among other things, Internet Connection Firewall left computers unprotected for 5 to 20 seconds during bootup, and untold thousands of computers were infected by viruses as a result.) Windows Firewall is enabled, or attached, on any network adapter or dial-up connection that directly connects to the Internet. Its purpose is to block any traffic that carries networking-related data, so it prevents computers on the Internet from accessing shared files, Remote Desktop, Remote Administration, and other "sensitive" functions. In fact, Windows Firewall is designed so that on all but large corporate LANs it can be used on all network interfaces without interfering with day-to-day networking use. This can help prevent the spread of viruses from one computer to another across your LAN, should one become infected. Windows Firewall is enabled by default when you install XP Service Pack 2, or install a copy of Windows XP that has Service Pack 2 built in. You can also enable or disable it manually by selecting the Change Windows Firewall Settings task on the Network Connections window (I'll tell you how to do this later in the chapter under "Specific Configuration Steps for Windows XP.") You also can tell the firewall whether you want it to permit incoming requests for specific services. If you have a Web server, for example, you'd need to tell Windows Firewall to permit incoming HTTP data. NOTE Windows Firewall has the advantage that it automatically opens up to permit incoming connections for programs like Remote Assistance and Windows Messenger. On the other hand, it's part of the very operating system it's trying to protect, and if either Windows XP or the firewall gets compromised, your computer's a goner. If I had the choice between using Windows Firewall and an external firewall device such as a commercial firewall server, or a connection sharing router with filter rules, I'd use the external firewall. But Windows Firewall is definitely better than no firewall at all. Simple File SharingWindows XP introduced a new network security model called Simple File Sharing. Before I explain this, I'll give you some background. In the original Windows NT/2000 workgroup network security model, when you attempted to use a shared network resource, Windows would see if your username and password matched an account on the remote computer. One of four things would happen:
The problem with this system is that it required you to create user accounts on each computer you wanted to reach over the network. Multiply say 5 users times 5 computers, and you had 25 user accounts to configure. What a pain! (People pay big bucks for a Windows Server-based domain network to eliminate this very hassle.) Because it was so much trouble, people usually would enable the Guest account. The problem is that Guest is a member of the group Everyone, and usually Everyone has read/write or at least read privileges on the entire hard drive and full privileges on FAT-formatted disks which have no user-level security at all. This means the user account headache invited people to make their entire computers vulnerable to abuse over their LAN and the Internet. (And, as I mentioned earlier, this is where most of your spam comes from.) Enter Simple File Sharing. On all Windows XP Home Edition computers, and as the default option on XP Professional on a Workgroup network, Simple File Sharing does four things:
Only a few folders get shared, and while anybody with access to the network can access them, the damage an intruder can do is limited to stealing or modifying just the files in a few folders that are known to be public. It's also much easier to use shared files and folders on your LAN. You won't be called upon or able to select which individual users get access and which don't. If you share a folder, you share it with read-only or read/write access. It's very simple indeed, and it's perfectly appropriate for home and small office LANs. Microsoft's reasoning here is that it's better to configure a somewhat looser LAN correctly than a stricter LAN poorly. For tight user control, corporations use Server-based networks. There are two down sides to Simple File Sharing: First, and most important, it's crucial that you have a firewall in place. Otherwise, everyone on the Internet will have the same rights in your shared folders as you. (That's one of the reasons for Windows Firewall, and why the Network Setup Wizard is so adamant about either installing the Firewall or disabling file sharing.) The second down side is less troublesome and probably less noticeable to most people: If you attempt to use a shared folder from another computer on which you have the same username and password, you won't get the full rights that you'd have locally. You'll be a guest like anyone else. In particular, the very handy whole-drive administrative shares like "C$" do not work when Simple File Sharing is in use. On Windows XP Professional, if you want to use the old per-user permission scheme, you can disable Simple File Sharing. You'll have more control over permissions at the cost of lots more work in configuration. Packet FilteringIf you use a hardware Internet connection sharing router (also called a residential gateway) or a full-fledged network router for your Internet service, you can instruct it to block data that carries services you don't want exposed to the Internet. This is called packet filtering. You can set this up in addition to NAT to provide extra protection. Filtering works like this: Each Internet data packet contains identifying numbers that indicate the protocol type (such as TCP or UDP) and the IP address for the source and destination computers. Some protocols also have an additional number called a port, which identifies the program that is to receive the packet. The WWW service, for example, expects TCP protocol packets addressed to port 80. A domain name server listens for UDP packets on port 53. A packet arriving at the firewall from either side is examined; then it is either passed on or discarded, according to a set of rules that list the protocols and ports permitted or prohibited for each direction. A prohibited packet can be dropped silently, or the router can reject the packet with an error message indicating the requested network service is unavailable. (If possible, I prefer to specify the silent treatment. Why tell hackers that a desired service is present even if it's unavailable to them?) Some routers can also make a log entry or send an alert indicating that an unwanted connection was attempted. NOTE For a good introduction to firewalls and Internet security in general, I recommend Practical Firewalls, published by Que; Maximum Windows 2000 Security, published by Sams; and Firewalls and Internet Security: Repelling the Wily Hacker published by Addison & Wesley. Configuring routers for filtering is beyond the scope of this book, but I'll list some relevant protocols and ports in Table 21.1. If your router lets you block incoming requests separately from outgoing requests, you should block incoming requests for all of the services listed below, unless you are sure you want to enable access to them. If you have a basic gateway router that doesn't provide separate incoming and outgoing filters, you probably only want to filter those services that I've marked with an asterisk (*).
As I said, if you use a hardware router to connect to the Internet, I can't show you the specifics for your device. I can give you a couple of examples, though. My Linksys Cable/DSL Sharing Router uses a Web browser for configuration, and there's a page for setting up filters, as shown in Figure 21.1. In this figure, I've blocked the ports for Microsoft file sharing services. Figure 21.1. Configuring packet filters in a typical Internet connection sharing router.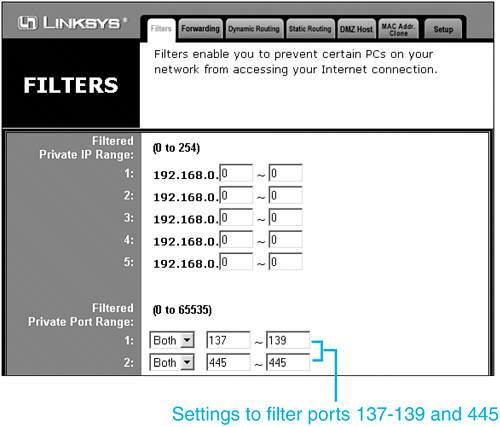 If you use routed DSL Internet service, your ISP might have provided a router manufactured by Flowpoint, Netopia, or another manufacturer. As an example, filtering is set up in a Flowpoint router through a command line interface, as shown below: remote ipfilter append input drop -p udp -dp 137:138 internet remote ipfilter append input drop -p tcp -dp 139 internet remote ipfilter append input drop -p tcp -dp 445 internet These are complex devices and your ISP will help you set yours up. Insist that they install filters for ports 137, 138, 139, and 445 at the very least. Using NAT or Internet Connection SharingBy either name, Network Address Translation (NAT) has two big security benefits. First, it can be used to hide an entire network behind one IP address. Then, while it transparently passes connections from you out to the Internet, it rejects all incoming connection attempts except those that you explicitly direct to waiting servers inside your LAN. Packet filtering isn't absolutely necessary with NAT, although it can't hurt to add it.
You learned how to configure Windows Internet Connection Sharing in Chapter 19, so I won't repeat that information here. CAUTION Microsoft's Internet Connection Sharing (ICS) blocks incoming access to other computers on the LAN but unless Windows Firewall is also enabled, it does not protect the computer that is sharing the Internet connection. If you use ICS you must enable Windows Firewall on the same connection. Together, they provide adequate protection for all of your computers. If you have built a network with another type of router or connection sharing device, you must follow the manufacturer's instructions or get help from your ISP to set it up. TIP Not all ISPs will help you set up a connection-sharing router. These devices just cut into their revenues. Your ISP may even forbid their use. Better check first, before asking for help in installing one. Personally, I think that the additional security that they provide justifies their use even if the ISP doesn't like them. Add-On Products for WindowsThere are many commercial products called Personal Firewalls, designed for use on PCs. Products such as Zone Alarm and Zone Alarm Pro (www.zonelabs.com), McAfee Personal Firewall (www.mcafee.com), Sygate Personal Firewall (www.sygate.com), Norton Personal Firewall (www.symantec.com), and Black Ice Defender (www.networkice.com) range in price from free to about $50. Now that Windows includes an integral firewall, these add-on products may no longer be necessary, but you may still want to investigate them for the additional reporting and outbound-traffic-monitoring they provide. Secure Your RouterIf you use a router for your Internet connection and rely on it to provide network protection, you must make it require a secure password. If your router doesn't require a password, anyone could connect to it across the Internet and delete the filters you've set up. Most routers as configured by the manufacturers and ISPs do not require a password. To lock down your router, you'll have to follow procedures for your specific router. You want to do the following:
If you don't want to attempt to lock down your router, your ISP should do it for you. If your ISP supplied your router and you change the password yourself, be sure to give the new password to your ISP. Set Up Restrictive Access ControlsPossibly the most important and difficult step you can take is to limit access to shared files, folders, and printers. You can use the guidelines shown in Table 21.2 to help organize a security review of every machine on your network. I've put some crucial items in boldface.
Keep Up-to-DateNew bugs in major operating systems and applications software are found every week, and patches and updates are issued almost as frequently. Even Microsoft's own public servers have been taken out by virus software! Software manufacturers including Microsoft have recently become quite forthcoming with information about security risks, bugs, and the like. It wasn't always the case, as they mostly figured if they kept the problems a secret, fewer bad guys would find out about them, and so their customers would be better off. (That, and it saved them the embarrassment of admitting the seriousness of their bugs.) Information is shared so quickly among the bad guys now that it has become essential for companies to inform users of security problems as soon as a defensive strategy can be devised. You can subscribe to the Microsoft email Updates security bulletin service at www.microsoft.com/security. The following are some other places to check out: www.ntbugtraq.com www.sans.org www.cert.org www.first.org www.cs.purdue.edu/coast/ www.greatcircle.com Usenet newsgroups: comp.security.*, comp.risks Some of these sites point you toward security-related mailing lists. You should subscribe to Microsoft Security Advisor Bulletins at least. Forewarned is forearmed! |
EAN: 2147483647
Pages: 450
 To learn more about this topic,
To learn more about this topic,