Countering the Threats
This section explores some of the options available to you to counter the threats already discussed.
Hardware
First, let s consider what you can do with the computer hardware to make your system more secure.
Physical Security of the Hardware
-
Physical security is really just a matter of common sense. Keep computer equipment, especially portable equipment such as laptops, secure. If the computer BIOS has the facility to configure a power-on password, use it. This at least will make it harder for someone to access your machine if it is stolen.
If you are unlucky enough to have your computer stolen, you have to rely on your backups to get back the information that you lost. You do have backups , don t you? You have tested them, haven t you?
The idea behind backing up your system is to allow you to rebuild it in case of some catastrophic event. This means that someone else can also build a copy of your system if they can get hold of your backups, so take care of the physical security of your backup media, too.
Hardware Failure
Pay attention to the environmental conditions that your computer is working in. Computers don t like to get hot, and excessive temperature can cause premature failure of heat-sensitive components , especially hard disk drives . There are ways of preventing the failure of a disk drive from causing loss of data, and these techniques rely on keeping the information on more than one physical disk.
The term Redundant Array of Independent Disks (RAID) is widely used to describe these solutions, and the RAID level , a combination of digits and sometimes letters , indicates how the information is stored on multiple disks.
RAID can be implemented in hardware (typically in the hard disk adapter) or in software. If you re interested in RAID, have a look at the Linux-ATA-RAID HOWTO and the Software-RAID HOWTO on your system s documentation resources, or online.
Common RAID levels are described in the table that follows .
| RAID Level | Data Positioning |
|---|---|
|
| Data is broken up into equal size chunks (64Kb and 128Kb are common), and chunks are written to every disk in the array in turn (with four disks in the array, the first, fifth, ninth, . . ., chunks of data are written to the first disk; the second, sixth and, tenth to the second disk; and so on). This pattern of data placement is called striping, and the size of each chunk of data is called the stripe width. This gives the best performance, but worst availability, because failure of any disk will result in the loss of some data. |
| 1 | Data is copied onto pairs of disks (mirrored). Good performance and availability, but it uses twice as much disk space. |
| 5 | Data is striped across multiple disks, and protected by parity information that is also striped across the disks. Good performance for reading, but writing can be slowed by the need to update parity information. Requires extra disk capacity to store the parity information. |
| 7 | Not really RAID at all, RAID 7 is also known as JBOD (Just a Bunch Of Disks). Here the information is not configured according to RAID, and your multiple disks are simply configured as one larger logical drive. It offers no fault tolerance advantages over simply using several disks individually. |
| 10 (or 0+1) | Data is striped across multiple pairs of disks. Combines performance of RAID 0 with availability of RAID 1. |
Whether RAID is suitable for you depends on how valuable you consider your information to be ”a decision that only you can make. Even if you do go for a hardware or software RAID solution for your Fedora Core 2 Linux system, please don t make the mistake of thinking that you don t need to make regular backups. Even if you set up the most extreme combination of hardware and software RAID (using software RAID to mirror data between two hardware RAID arrays, giving you effectively four copies of the data on four separate physical hard disks), the rm command can still irreversibly delete all four copies in a fraction of a second.
Local Security
So, you ve sorted out the physical security of your Fedora Core 2 system. You ve enabled the BIOS password so that only those who know it can start the machine up in the first place, and you ve taken care with the physical location so it won t get stolen and the disk drives will stay nice and cool. Should you be unlucky enough to suffer a disk drive failure, you re taking, and testing, regular backups so you re confident you can recover any lost information. What s next ?
You ll recall from the previous section, Potential Threats, that operator error was high on the list of potential threats. Computers have a nasty habit of doing exactly what you tell them to do, and not what you want them to do. So that this doesn t cause you too many problems, the trick is always to work with the lowest level of authority that you need to perform a particular task. Usually, this is not the root account.
Here s a little hypothetical example to demonstrate the potential pitfalls of using the root account for everyday tasks .
Suppose you need to maintain the contents of a directory called /home/foo/logs by deleting files that are more than 14 days old. You could write a simple script to do this:
#!/bin/bash LOGDIR="/home/foo/logs" cd $LGODIR find . mtime +14 exec ls \{\} \; # Use "ls" for testing, change to "rm" later
Unfortunately, there s a typo in the script (the fourth line should say cd $LOGDIR ); this means that when the cd command is run, its argument is blank (because the misspelled variable $LGODIR is not defined). The cd command makes the current working directory the $HOME directory, not /home/foo/logs as you want. The find command then finds all the files below your $HOME directory (the current working directory) older than 14 days and deletes them. (Well, it will just list them at the moment ”at least the test version of the script does not do anything dangerous). That s a pain if you re logged on as an ordinary user , but if you re logged on as root, this could well delete a lot of critical configuration information. (At least root s home directory on Fedora Core 2 Linux defaults to /root , which is a small mercy ”on some other versions of UNIX, the default home directory for root is / , so running this flawedscript on one of those could well wipe out the entire operating system.)
Passwords
The password that you use to authenticate yourself to the operating system when you log in is the only way you have of proving your identity, and thus keeping an intruder out. Your password is never stored on the Linux system (the operating system won t do it). Instead, a non-reversible mathematical function called a hash is used to combine your password with a random value (called the salt ), and the hashed password is stored by the system. When you try to log in, the password you type is once again hashed with the same salt, and the result is compared to the one stored when the password was originally set. If the values are the same, it s fairly safe to assume that the password you typed is the same as the original one, and you are allowed in.
Now, you re probably thinking that someone could look at the stored hashed passwords and deduce the original passwords by reversing the hash function. However, the hash functions are chosen to make this reversal practically impossible . However, that doesn t stop someone who has access to the hashed passwords from using a program that guesses passwords to try and guess one.
Early versions of UNIX stored the hashed passwords with other user information in /etc/passwd . Because the user information needed to be accessible to everyone (so, for example, usernames could be shown in the output of ls “l ), this also made the hashed passwords available to everyone. Modern versions of UNIX, including Fedora Core 2 Linux 9, avoid this problem by keeping hashed passwords in a separate file, called the shadow password file. On Fedora Core 2, this is /etc/shadow . Because the hashed passwords need to be accessible only to authentication programs that run with root authority, the shadow password file should be accessible only to the root user.
Choosing a Strong Password
Choosing a strong password really means to avoid weak passwords. Weak passwords are ones that can be guessed, either by humans or by password-cracking programs (that will quite happily try different permutations of words from password dictionaries for days on end without getting bored).
So, avoid passwords that can be found in a dictionary (in any language), or variations of these (for example, changing is to 1s, or os to 0s, or adding digits), passwords that someone who knows you may guess ( name of family member or pet), or anything generated in a systematic way. Include punctuation and other symbols, and make use of the fact that Fedora Core 2 Linux 9 uses MD5 password hashes that allow passwords to be up to 15 characters long.
However, some characters shouldn t be included in passwords because they can be misinterpreted as terminal control characters and cause problems when logging in. Avoid @, #, [ backspace ] , and other control characters.
For example, here are some weak passwords:
-
asdfghj (obvious keyboard pattern)
-
oozyllak (pet s name spelt backwards )
-
Pa55w0rd (trivial modification of a dictionary word)
These would have been strong passwords until they were published in this book:
-
14%-^^Ao-&
-
Z&23vvO+%
-
hjA+84ro*
However, make sure you can remember your password so you don t have to write it down. As soon as you do that, you re weakening it. A slip of paper under the keyboard is a dead giveaway.
Checking Passwords
The password-cracking programs that are useful to hackers are just as useful to you, as you can use themto identify weak passwords on your systems. Then you can get the offending users to change them before a hacker cracks them. One of the best known of these programs is simply called Crack. It requires a bit of work to build and install it, so we ll go through it step-by-step here.
Crack is a 2.5MB download. If you don t fancy downloading it, you can skip ahead to the section Running Crack, and we ll catch up with you in a moment.
Try It Out Using the Crack Program
Before you begin setting up the Crack program, you need to make a home for it. It s best to create your own directories for programs that you build and install yourself (as opposed to installing from RPM packages) so they don t interfere with system-installed packages.
Crack doesn t require root privileges to run (but you do need to be root to get at the shadow passwords to feed Crack later on), so you ll download, configure, and build it as an ordinary, unprivileged user.
-
The first thing you ll do is create a home for Crack. Open a terminal window (Main Menu>System Tools>Terminal) and type the following commands at the prompt:
% cd % pwd % mkdir crack
The cd command on its own makes the current working directory the home directory for the user running the command. (This should be the current directory for a newly opened terminal session anyway, but we ve included it here in case you re trying this out in an existing window.) The pwd command shows you the current working directory to confirm you re where you expect to be, and then the mkdir command creates a directory called crack . This is where you re going to install the Crack program.
-
Once you have a home for Crack, you need to get a copy of the program.
The easiest way to download the Crack program is through the Mozilla Web browser. Start the browser, and then point it to ftp://ftp.cert.dfn.de/pub/tools/password/Crack/ . You should be presented with a list of files in a directory. Click the file called Crack_5.0a.tar.gz , and when a dialog box appears asking you what you want to do, select Save to disk and click OK. Browse to the crack directory you ve just created and click OK.
If you have trouble connecting to the FTP site listed in the preceding paragraph, you can try ftp://ftp.cerias.purdue.edu/pub/tools/unix/pwdutils/crack/ instead.
-
The next step is to unpack the downloaded file. The letters .tar.gz at the end of the file indicate that it is a tape archive (TAR) format file that has been compressed with GNU Zip. (You ll sometimes see .tgz at the end of a file to indicate the same thing.) You need to uncompress and untar the file.
Go back to the terminal window and type the following commands:
% cd crack % tar xzvf Crack_5.0a.tar.gz
The tar command extracts the files ( x switch) from a compressed archive file ( z switch) called Crack_5.0a.tar.gz (-f Crack_5.0a.tar.gz) and prints the filenames as they re extracted ( v switch). Notice that the files go into directories under c50a/ and that these directories are created as required (see Figure 10-1).
-
Now you need to make a few configuration changes to the Crack source code before it will build and run successfully on your Fedora Core 2 Linux system. First, you need to edit the Crack script. Change to the c50a directory and open Crack in the Gnome text editor by running these commands:
% cd c50a % gedit Crack
-
A text editor window pops up. Scroll through the file to the section that says the following:
# # now pick your compiler #
Fedora Core 2 Linux ships with the GNU C compiler called gcc , so the gcc 2.7.2 section is what you need to use (even though you ve got gcc version 3.2). Place # characters at the start of the lines for vanilla unix cc to turn them into comments (a process known as commenting out the code), and remove the same characters from the corresponding lines in the gcc 2.7.2 section. You also need to use the stdlib crypt() routine, so remove the # from the start of the LIBS=... line.
When you re finished, the modified Crack file should look like Figure 10-2.
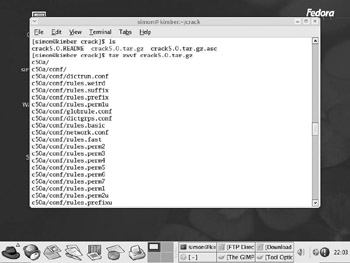
Figure 10-1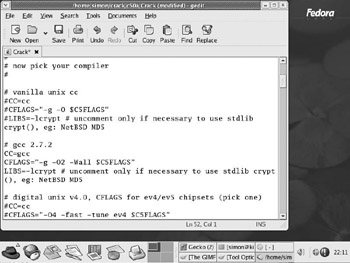
Figure 10-2 -
Save the changes and exit gedit .
-
Fedora Core 2 Linux does not use the standard DES algorithm to encrypt passwords, but uses a stronger algorithm based on Message Digest 5 (MD5). Crack is set up to use DES by default, so you need to change this. The following steps are given in the Crack 5.0a README file, so type them in at the command line prompt:
% mv src/libdes src/libdes.orig % cd src/util % cp elcid.c,bsd elcid.c
Note If asked to overwrite elcid.c , answer y .
-
There s one other small modification to make. The Fedora Core 2 9 shadow password file uses salts that contain characters that the shipped version of Crack interprets as invalid (because they re not in the list of valid characters). For the purposes of this exercise, we ll modify the routine that checks for the validity of the hashed passwords to accept these characters. The routine as shipped checks that each character in the ciphertext (hashed password) is in a list of allowed characters. We ll switch things around so it checks that none of the characters is in a list of disallowed characters.
Edit the elcid.c source file by typing gedit elcid.c . Find the function elcid_invalid(ciphertext) and make the following three changes:
-
Change the name of the variable validchars to invalidchars .
-
Change the value of this variable to ! .
-
Remove the ! in the line starting if (! strchr ... to reverse the sense of the logic.
When you re finished, it should look like Figure 10-3.
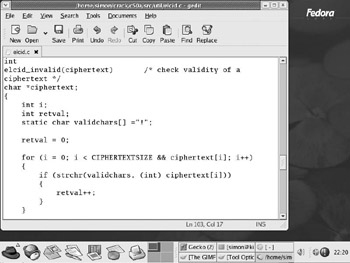
Figure 10-3 -
-
Save the changes and exit gedit .
-
Now you re ready to compile the Crack program. This is done by invoking the Crack script with the switch -makeonly . So, change the directory back to $HOME/crack/c50a and run the following command:
% ./Crack makeonlyNote Note that you need to specify where to find the Crack program by giving the directory ” ./ means the current directory. Unlike Microsoft Windows, Linux and other UNIX variants do not include the current directory on the search path unless explicitly told to do so. That s never a good idea for the root account, as you really want to be sure the root user is running programs in the correct system locations and not other programs lying around that happen to have the same name.
-
When Crack is invoked with the “makeonly option, it makes the required program files. Make sure that it finishes with the message Crack: makeonly done .
-
Next, you need to make the password dictionaries that Crack will use to try and guess the passwords on your system. Do this by running ./Crack “makedict .
-
Again, make sure that this finishes with the message Crack: makedict done .
-
Before you can try out your newly built Crack program, you need to get it some passwords to work on. The information Crack requires is held on Fedora Core 2 Linux systems in /etc/passwd and /etc/shadow , and these need merging into a single file. Fortunately, there s a utility provided with Crack that will do just that for you.
-
Note that you must be root to read /etc/shadow , and because the merged file contains information useful to a potential hacker (the encrypted passwords from the shadow password file), you need to make sure that it too has restricted access. The best way to do this is to create an empty file with the correct permissions (by setting your umask), and then append the sensitive data to the file. (You could create the file with default permissions and then tighten them up, but there is a chance that someone could open the file before you ve changed the permissions.) You ll change the ownership of the file back to the user under which you want to run Crack to avoid having to do that as root.
-
So, run the following commands to create the merged file that is suitable for Crack to work on:
% su root # umask 077 # touch passwords.dat # scripts/shadmrg.sv > passwords.dat # chown user1 passwords.dat # ls l passwords.dat # exit
-
All you have to do now is run the following command to start Crack guessing at the passwords your users have set to see if there are any weak ones:
% ./Crack passwords.dat -
When you see the word Done , it doesn t mean that Crack has finished guessing passwords. (If passwords could be guessed that quickly, we might as well not bother with them at all!) What it does mean is that Crack has started a background process running that will spend the next hours, or even days, guessing the passwords in the passwords.dat file and logging any matches that it finds. Use the following command to find the background process:
% ps ef grep crackIf you want to stop the background Crack process, the correct way to do this is to run the following:
$HOME/crack/c50a/scripts/plaster.How do you find out how Crack is doing? Simply run the Reporter script that is in the same directory as the Crack program. To find out any passwords that have been guessed, type the following command in the command line window:
% ./Reporter quietIf you leave off the “quiet switch, you'll get some warning messages about locked accounts and accounts where there is no valid password. Expect several of these to show up, because accounts used for running system services such as printing and Web serving (such as lpd andapache) will normally be configured in this way to prevent anyone from logging in as thoseusers.
Caution A final word of warning when using Crack or any other password-cracking program: Make sure that you are authorized to do this by the appropriate person, preferably in writing.
EAN: 2147483647
Pages: 170