Networking
These days, networking is part of daily life. Whether you are sending e-mail from your desktop PCs or using the Internet for shopping, networking is at the heart of it. In fact, there are a number of different types of network:
-
A local area network (LAN) is a network that covers a limited geographical area.
-
A metropolitan area network (MAN) covers a geographic area such as a city or suburb.
-
A wide area network (WAN) may span a wide geographic area, spread over many states or countries . The Internet is an example of a WAN.
To facilitate communication across these networks, you have protocols . A protocol is a standard language by which two (possibly dissimilar) systems can communicate. For example, TCP/IP is the protocol that allows different machines to participate together to make the Internet work.
| Note | For more information about Networking protocols such as TCP/IP, AppleTalk, X.25, Frame Relay, ISDN, PPP, SLIP, PLIP, and so on, try www.tldp.org/LDP/nag2/index.html and www.tldp.org/HOWTO/Networking-Overview-HOWTO.html . |
Fedora Linux and Networking
Fedora 2 comes bundled with lots of networking applications and utilities that will help you meet your networking requirements. The following table categorizes and lists the networking applications that come with Fedora 2:
| Application Type | Application Name | Description |
|---|---|---|
| Web server | httpd | The widely used Apache HTTP server. |
| FTP server | vsftp | A very secure FTP server. |
| File server | sambasambasamba-client | The SAMBA server provides file sharing between SMB-enabled machines (such as Windows and Linux machines). SAMBA client programs are designed to access SMB shares. |
| Print server | cups | CUPS printing service and the drivers to use it. |
| Mail server | sendmail | A widely used mail transport agent. |
| DHCP server | dhcp | A DHCP server and relay agent. |
This chapter discusses some of these applications and helps you to get your Linux machine acting as a full-fledged network server.
Why Is Linux Good for Networking?
One of the most significant factors in choosing the hardware and software for a network is the total cost of ownership (TCO) . This is the cost of purchase, setup and configuration, and maintenance. If you sit down and analyze the requirements of different parts of network architecture, you ll quickly find that the free, open nature of Linux systems lends itself better to some parts of a network than others.
Linux is a particularly good choice for supporting network applications (such as file servers, Web servers, and mail servers):
-
The cost of purchase (both of the operating system and the software itself) is low. Cost of setup should generally also be favorable, particularly given the advances both in recent releases of network applications and in Fedora 2 itself, and the vast body of knowledge in the open source community that is available via Web sites, news groups, and local Linux users groups. (Many enterprise-level solutions companies such as Red Hat, IBM, Hewlett Packard, and Sun Microsystems have also started providing commercial-level support for Linux servers.)
-
The stability and reliability of the operating system is also influential because an unstable or unreliable system brings maintenance costs. Linux is a good choice for network applications because it makes the grade in these areas. Moreover, Linux is ready for high-availability environments (see www. ibiblio .org/pub/Linux/ALPHA/linux-ha ).
-
Other factors influencing TCO include the scalability, flexibility, and security of the system:
-
By choosing a Linux operating system and open source networking applications, you have access to the source code of both the system and the application. This puts you in a position to adapt the applications to achieve whatever aims you need.
-
You ve already seen evidence in this chapter that Linux is capable of being deployed in both small- and large-scale networks.
-
Red Hat Linux installs by default with a minimum of good-practice security, and can be further enhanced with a combination of open source security tools and good practice (see Chapter 10).
-
Linux is also great for services that can be replicated (for example, DNS). You can configure such machines cheaply, and replicate them. Then, if one machine fails, it should be possible to replace it cheaply. In the meantime, the replicate servers keep on working to provide the service.
By contrast, Linux is not a common choice for basic infrastructure, such as routers, hubs, and switches. While Linux is capable in this area, it s desirable only when the low cost of PCs is the major selection criteria. In a more business-critical role, where reliability will count for more than minimum purchase price, dedicated hardware is still the most popular choice.
You can find more information about TCO comparison between Fedora 2 and other UNIX flavors at www.redhat.com/whitepapers/services/tco.pdf .
Assumptions for Network Setup
In the demonstrations in this chapter, we ve used a network setup that may not be the same as your own environment. You can choose your own server, connectivity devices (switch, hub, and direct cable connection), IP address scheme, and hostname to set up networking in a way that suits your own requirements. This section notes the network settings that we ve used. To facilitate, an explanation of the terms used follows .
The network topology refers to the shape or layout of the network. It defines how different systems in a network are connected and communicate with each other. The ideal topology of a network depends on the size of the network, the requirements of its users, and the policies of the company or organization.
Figure 9-1 shows an ideal network topology.
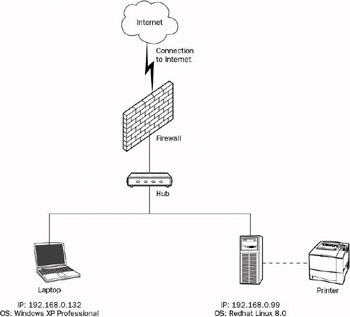
Figure 9-1
This diagram shows a client machine (in the form of a Windows 2000 Professional laptop), and a server (running Fedora 2, and supporting some of the services described in this chapter. They are connected via an internal network, and protected from the Internet by a hub and a firewall.
Your network topology might look different. For example, if you have a smaller network, it s possible that you don t have a hub, and that your firewall is not a dedicated machine but a piece of software hosted by your Linux server machine. If you have only a single machine, it can double as both the server and client machines in this diagram (being a client of its own services).
Note that both the user s laptop and the server machine have been assigned an IP address ”this is used to uniquely identify the computer (or other device) within a TCP/IP network. An IP address is a 32-bit binary address in the form of four decimal values. Each of these four decimals represents an 8-bit value (an octet), and is in the range 0 to 255. This format is known as dotted quad notation .
In fact, the TCP/IP network is divided into different class networks. The important classes are defined in the following table.
| Class | Values | Description |
|---|---|---|
| Class A | 1.x.x.x to 127.x.x.x | The first octet specifies the network number, and the remaining octets specify the host within the network. This class supports about 1.6 million hosts per network. |
| Class B | 128.0.x.x to 191.255.x.x | The first two octets specify the network number, and the remaining octets specify the host within the network. This class supports 16,320 networks with 65,024 hosts each. |
| Class C | 192.0.0.x to 223.255.255.x | The first three octets specify the network number, and the remaining octets specify the host within the network. This class supports nearly two million networks with up to 254 hosts each. |
| Class D | 224.0.0.0 to 239.255.255.255 | These are reserved for multicast groups. |
| Class E | 240.0.0.0 to 254.255.255.254 | These are reserved for special purpose use. |
The TCP/IP networks can also be divided by public and private IP addresses:
-
Your Internet service provider (ISP) assigns you your public IP address. In fact, this IP address is allocated to the ISP by the Internet Assigned Numbers Authority (IANA ” www.iana.org ). It s your public IP address that identifies you on the Internet.
-
Private IP addresses are those (like the addresses used in the preceding diagram) that identify a device within a private or non-Internet-connected network. Three TCP/IP network address ranges are reserved for use in private networks: 10.0.0.0 “10.255.255.255, 172.16.0.0 “172.31.255.255, and 192.168.0.0 “192.168.255.255.
A netmask is a 32-bit string that hides the network part of an IP address, so that only the host (computer) part of the address remains. For example, the netmask 255.255.255.0 looks like an IP address, but in fact hides the first 24 bits of the IP address so that only the last 8 bits remain (recall that 255 is the decimal representation of the binary 11111111). The netmask 255.255.255.0 is commonly used for Class C IP addresses to reveal the specific host computer address publicly .
The following definitions will also be useful here:
-
A gateway is a host that is connected to two or more physical networks, and allows messages to switch between them.
-
The term hostname refers to the unique name of the machine, so that it can identify itself on the network.
-
Finally, the domain name system (DNS) is a distributed database that translates domain names into IP addresses and vice versa. For example, DNS translates the domain name www.linux4biz.net to the IP address 66.103.135.76 .
With all that in mind, let s return to those two machines on our sample network ”the Fedora 2 server machine and the Windows 2000 client laptop machine. Following are the network configuration settings we used for those two machines in this chapter.
The Fedora 2 server machine is set up as a firewall and router, and has Internet connectivity. Over the course of the chapter we ll show how it can be configured as a File server, Print server, DHCP server, FTP server, Web server, or Mail server.
| Server | Value |
|---|---|
| Operating system | Fedora 2 |
| IP address | 192.168.0.99 |
| Netmask | 255.255.255.0 |
| Hostname | linux4biz |
The laptop is a simple client machine, designed for a user and ( potentially ) sharing resources with other similar machines on the network.
| Setting | Value |
|---|---|
| Purpose | A Client laptop system to be used to share resources configured on a Linux server |
| Operating system | Windows 2000 Professional |
| IP address | 192.168.0.132 |
| Netmask | 255.255.255.0 |
| Hostname | Win |
As we ve said, your network topology, and the network configuration of your machine(s), may be different; but many of the principles in this chapter remain the same, and you should be able to get any of these services going regardless of your own environment.
We will assume that you have root access to the Fedora 2 server. The chapter uses the terms Linux server and client to refer to the Fedora 2 server machine and the Microsoft Windows 2000 client machine, respectively.
EAN: 2147483647
Pages: 170