Identifying VLANs
|
As frames are switched throughout the internetwork, switches must be able to keep track of all the different frame types, plus understand what to do with them depending on the hardware address. And remember, frames are handled differently according to the type of link they are traversing.
There are two different types of links in a switched environment:
Access links This type of link is only part of one VLAN and it’s referred to as the native VLAN of the port. Any device attached to an access link is unaware of a VLAN membership—the device just assumes it’s part of a broadcast domain, but it has no understanding of the physical network.
Switches remove any VLAN information from the frame before it’s sent to an access link device. Access link devices cannot communicate with devices outside their VLAN unless the packet is routed through a router.
Trunk links Trunks can carry multiple VLANs and originally got their name from the telephone system trunks that carry multiple telephone conversations.
Trunk links are 100Mbps or 1000Mbps point-to-point links between two switches, between a switch and router, or between a switch and server. They carry the traffic of multiple VLANs—from 1 to 1005 at a time. You can’t run them on 10Mbps links.
Trunking allows you to make a single port part of multiple VLANs at the same time. This can be a real advantage. For instance, you can actually set things up to have a server in two broadcast domains simultaneously so that your users won’t have to cross a Layer 3 device (router) to log in and access it. Another benefit to trunking is when you’re connecting switches. Trunk links can carry some or all VLAN information across the link, but if the links between your switches aren’t trunked, only VLAN 1 information is switched across the link by default. This is why all VLANs are configured on a trunked link unless cleared by an administrator by hand.
Figure 2.15 shows how the different links are used in a switched network. Both switches can communicate to all VLANs because of the trunk link between them. And remember, using an access link only allows one VLAN to be used between switches. As you can see, these hosts are using access links to connect to the switch, so that means they’re communicating in one VLAN only.
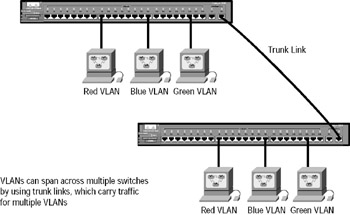
Figure 2.15: Access and trunk links in a switched network
Frame Tagging
You can also create your VLANs to span more than one connected switch. In Figure 2.12, hosts from various VLANs are spread across many switches. This flexible, power-packed capability is probably the main advantage to implementing VLANs!
But this can get kind of complicated—even for a switch—so there needs to be a way for each switch to keep track of all the users and frames as they travel the switch fabric and VLANs. (Remember that a switch fabric is a group of switches sharing the same VLAN information.) This is where frame tagging comes in. This frame identification method uniquely assigns a user- defined ID to each frame. Sometimes people refer to it as a VLAN ID or color.
Here’s how it works: Each switch that the frame reaches must first identify the VLAN ID from the frame tag. Then it finds out what to do with the frame by looking at the information in the filter table. If the frame reaches a switch that has another trunked link, the frame is forwarded out the trunk link port.
Once the frame reaches an exit to an access link, the switch removes the VLAN identifier. This is so the destination device can receive the frames without having to understand their VLAN identification.
VLAN Identification Methods
So VLAN identification is what switches use to keep track of all those frames as they’re traversing a switch fabric. It’s how switches identify which frames belong to which VLANs.
There’s more than one trunking method:
IEEE 802.1q Created by the IEEE as a standard method of frame tagging, 802.1q actually inserts a field into the frame to identify the VLAN. If you’re trunking between a Cisco switched link and a different brand of switch, you have to use 802.1q for the trunk to work.
| Note | The basic purpose of ISL and 802.1q frame-tagging methods is to provide interswitch VLAN communication. |
LAN emulation (LANE) LANE is used to communicate multiple VLANs over ATM.
802.10 (FDDI) Employed for sending VLAN information over FDDI, 802.10 uses a SAID field in the frame header to identify the VLAN. This is also proprietary to Cisco devices.
There’s one other trunking method you must know about. It’s the Inter- Switch Link (ISL) protocol.
Inter-Switch Link (ISL) Protocol
The Inter-Switch Link (ISL) protocol is proprietary to Cisco switches, and it’s used for Fast Ethernet and Gigabit Ethernet links only. ISL routing can be used on a switch port, on router interfaces, and on server interface cards to trunk a server. This is a very good approach if you’re creating functional VLANs and you don’t want to break the 80/20 rule. A trunked server is part of all VLANs (broadcast domains) simultaneously, so users don’t have to cross a Layer 3 device to access it.
ISL is a way of explicitly tagging VLAN information onto an Ethernet frame. This tagging information allows VLANs to be multiplexed over a trunk link through an external encapsulation method, which allows the switch to identify the VLAN membership of a frame over the trunked link.
By running ISL, you can interconnect multiple switches and still maintain VLAN information as traffic travels between switches on trunk links. ISL provides a low-latency, full wire-speed performance, in contrast to Fast Ethernet, which uses either half- or full-duplex mode.
| Note | Cisco created the ISL protocol, and so it’s proprietary in nature to Cisco devices only. If you need a non-proprietary VLAN protocol, use the 802.1q described in the Sybex CCNP: Switching Study Guide. |
Anyway, ISL is an external tagging process, which means the original frame isn’t altered—it’s only encapsulated with a new 26-byte ISL header. It also adds a second four-byte frame check sequence (FCS) field at the end of the frame. Because the frame has been encapsulated by ISL with information, only ISL-aware devices can read it. These frames can be up to a whopping 1,522 bytes long, and devices that receive them may record them as a giant frame because it’s over the maximum of 1,518 bytes allowed on an Ethernet segment.
On multi-VLAN (trunk) ports, each frame is tagged as it enters the switch. ISL NICs allow servers to send and receive frames tagged with multiple VLANs so they can traverse multiple VLANs without going through a router. This is good because it reduces latency. ISL makes it easy for users to access servers quickly and efficiently without having to go through a router every time they need to communicate with a resource. This technology can also be used with probes and certain network analyzers, and administrators can use it to include file servers in multiple VLANs simultaneously.
ISL VLAN information is added to a frame only if the frame is forwarded out a port configured as a trunk link. The ISL encapsulation is removed from the frame if the frame is forwarded out an access link. This is an important ISL fact, so make a mental note and don’t forget it!
|
EAN: 2147483647
Pages: 201