Testing Security Policy Using the Evaluate Assembly Wizard
| for RuBoard |
The tool provides a wizard that will help you analyze the current state of security policy with respect to any assembly. The Evaluate Assembly Wizard allows you to test the following conditions:
-
What the permissions are that an individual policy level, or all three policy levels combined, will grant to a specific assembly
-
What code groups are at an individual policy level or in all policy levels that apply to a specific assembly
The first feature will help you find out exactly what permissions policy will give to an assembly, and also the permissions each policy level contributes to the assembly's overall set of granted permissions. The second feature, testing what code groups apply to a specific assembly, can then be used to find exactly what subset of the code group hierarchies at each policy level contribute to the set of permissions granted from security policy. To put it succinctly, the first feature lets you know what permissions an assembly gets from the security policy, while the second feature shows you from where these permissions came.
NOTE
You should recall a few facts about the way the security model is designed before using this Wizard. First, the set of permissions granted at a specific policy level is intersected with the permissions granted at other policy levels. Also, the actual permission grant that an assembly receives at runtime of the assembly may differ from the set of permissions the policy hands to that assembly as shown by the Evaluate Assembly Wizard. Remember that the calculation of the assembly's permission grant set is not complete until the requested , refused , and optional permissions that an assembly has declared are taken into account. For example, although an assembly may be given full trust to access all protected resources by security policy, it may refuse to be given any access to the file system and registry and therefore would end up not receiving these permissions. If such an assembly then foolishly tried to access the file system, it would still generate a security exception, despite the fact that the administrator has set security policy such that it receives full trust, as shown by the Evaluate Assembly Wizard. Such situations are programming mistakes that an administrator will not be able to fix via a security policy change. You should contact the software vendor if that case occurs.
The following are a few scenarios that demonstrate typical situations of use for this wizard:
-
You have introduced a new code group to alter the permissions a given assembly or set of assemblies receives. To ascertain that the policy change has the desired effect, you use the Evaluate Assembly Wizard to browse to an affected assembly and check the permissions that this assembly now receives after your policy change. If it is different from what you expected, reuse the Wizard to check which code groups in security policy apply, to make sure your newly introduced code group matches the assembly, and that there are no other code groups interfering with the intended results.
-
An assembly generates an unexpected security exception. You use the Evaluate Assembly Wizard to find out the exact level of permissions granted by policy to the assembly, and then find out which code groups are responsible for the given permissions. This will help you greatly to pinpoint places in security policy that may need to be adjusted to enable the assembly in question.
-
An assembly that should not be allowed to execute or access a variety of resources given your understanding of current security policy does so anyway. You can use the Evaluate Assembly Wizard to find out the permissions the assembly actually receives from security policy, and then reuse the Wizard to find the code groups that apply to this assembly causing the unexpected permissions grant.
To start up the Wizard, simply right-click the Runtime Security Policy node and click the Evaluate Assembly Wizard option. This will bring up the Wizard start page shown in Figure 18.24.
Figure 18.24. The Evaluate Assembly Wizard's start page.
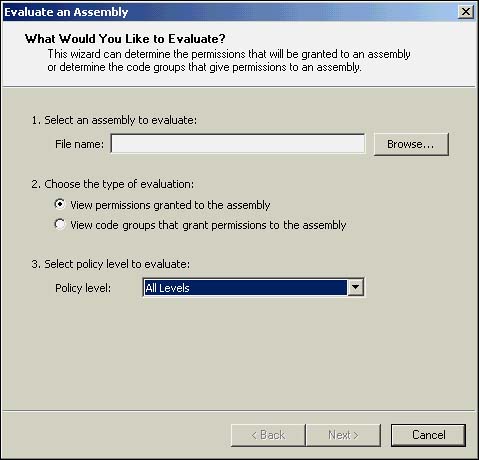
On this page, you should first browse to or simply enter the path to an assembly you want evaluated. All of the assembly's evidence will be taken into account in the evaluation the Wizard does, so choose the assembly carefully .
NOTE
As of the date of writing of this book, it was not possible to browse to an assembly location based on the http:// protocol.
After selecting an assembly to be evaluated, you have to select whether you want to see the permissions granted by the security policy to this assembly or the code groups in security policy that apply to this assembly. You will usually first want to see the permissions before finding out what code groups are responsible for handing them to the assembly.
Finally, you need to select whether you want to see the applicable permissions or code groups for all policy levels or just one policy level. If you choose a particular policy level, please keep in mind that all other policy levels usually contribute to the final set of permissions the assembly receives.
If you elected to see the permissions the chosen assembly receives, you will see the list of granted permissions. To view the properties of any of the granted permissions, simply select the permission whose properties you want to see and click the View Permission button. This will then show you the properties of the selected permission. Just seeing the list of permissions that have been granted tells you little as to the scope of access to resources. For example, if you see that an assembly has the registry permission, it is still unclear whether the permission state is set to give that assembly full access to all of the registry or read access to one registry location.
If you elected to see the code groups the assembly maps to, you will be presented with a condensed policy tree view containing just the code groups that match the assembly (see Figure 18.25).
Figure 18.25. Browsing the code groups that apply to the selected assembly.
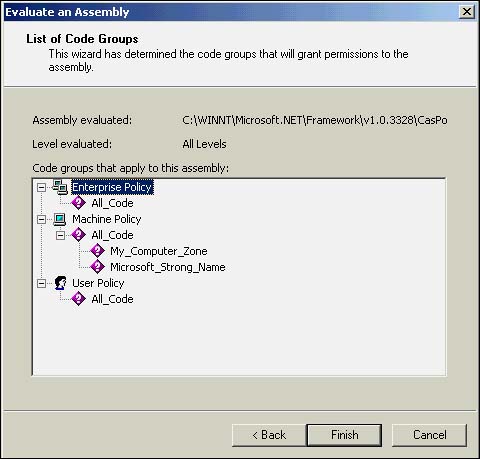
Unfortunately, you cannot access a code group's properties from this view. To find out exactly what the matching code groups grant to an assembly, either jot down the code group names or run a second instance of the tool in parallel and check the code group hierarchies for the respective code group properties.
| for RuBoard |
EAN: 2147483647
Pages: 235