Objective 2.2.3: Designing Trust Relationships Between Domains and Forests
A trust creates the framework that governs domain-to-domain or forest-to-forest relationships. A trust allows users in different domains or forests to access resources in other domains or forests based on the trust that is established. Just as in previous versions of the Windows Server operating system, Windows Server 2003 trusts allow network administrators to establish relationships between domains and forests so that, for example, users from Domain A can access resources in Domain B. Unlike previous releases of Windows, however, Windows 2000 and Server 2003 allow for the creation of two-way, transitive trusts. This means that if Domain A trusts Domain B, and if Domain B trusts Domain C, then Domain A automatically trusts Domain C. (You may remember the days of Windows NT 4.0, when the number of trust relationships you needed to create in a large environment became staggeringly large: A network with 10 domains would require the administrator to manually create 90 trust relationships to allow for the kind of trust relationships that Windows 2000 and Windows Server 2003 create automatically.) In this section, we ll cover the various types of trust relationships that you can create to allow your users to quickly and easily access the resources they require.
Let s review some of the terminology that you ll encounter when you re dealing with designing trust relationships:
-
One-way trust
-
Two-way trust
-
Transitive trust
-
Nontransitive trust
In a one-way trust, Domain A trusts Domain B. What this means is that Domain A is trusting Domain B s users and granting them access to its resources. As you can see in Figure 4.9, Domain A is the trusting domain, and Domain B is the trusted domain . With a one-way trust, the trusted domain contains the user resources that require access, and the trusting domain contains the resources that are being accessed. Diagrammatically, this concept is represented using an arrow pointing toward the trusted domain, as you can see in the figure. If you have a hard time remembering which domain is the trusted domain and which is the trusting domain as well as which way the arrow is supposed to point, it might help to try to remember it this way: Think of the last two letters in trust-ED as talking about a guy named Ed. The trust-ED domain is the one that contains users, since that s where ED is. The trusting domain, on the other hand, contains the thing that your users are trying to access. It s the trust-ING domain because that s where the THINGS are. Using this mnemonic device when you re looking at a diagram of a one-way trust relationship on the 70-298 exam, you can remember that the direction-of-trust arrow is pointing to ED .
When setting up one-way trusts from a Windows Server 2003 domain or forest, you have two possible options:
-
One-way: incoming Users in your Windows Server 2003 domain or forest will be able to access resources in the external realm, but external users will not be able to access any resources in your Windows Server 2003 domain. In this case, the Windows 2003 domain will be the trusted domain (since that s where Ed and all the other users are), and the external domain or forest will be the trusting domain, since that will be where the resources (or things ) are.
-
One-way: outgoing This is the reverse of one-way: incoming. Here, users in the external domain or forest will be able to access resources within your domain, but your Windows Server 2003 users will not be able to access any resources in the external realm. Likewise, the Windows Server 2003 domain will be the trusting domain, since it contains the resources being accessed, and the external domain or forest will be the trusted domain, since it contains the users who will be accessing the resources.
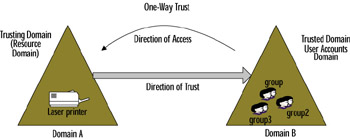
Figure 4.9: The One-Way Trust Relationship
Unlike a one-way trust, a two-way trust means that both Domain A and Domain B are simultaneously trusting and trusted domains, respectively, which means that users in both domains can access resources in either domain. Figure 4.10 will help you visualize this trust relationship.
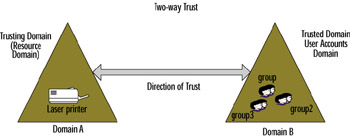
Figure 4.10: The Two-Way Trust Relationship
All Windows 2000 and Windows Server 2003 domains are designed with transitive trusts by default. Remember the transitive property from your high school mathematics class: If A equals B and B equals C, then A must therefore equal C. It works the same way in a transitive trust relationship: If Domain A trusts Domain B and Domain B trusts Domain C, then Domain A automatically trusts Domain C. (This is different from the NT 4.0 trust environment in which you needed to manually create another trust between Domain A and Domain C.) For example, when you create a child domain, a two-way transitive trust is automatically created between the parent and child domains. You can see this illustrated in Figure 4.11. In plain English, this means that using transitivity of trust , a user in any domain can access any resource in any other domain in the same forest.
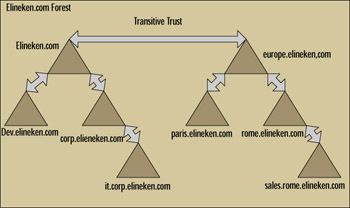
Figure 4.11: Trust Transitivity in Domains
Let s explore this idea a little further with forests, since transitive trusts flow between domains in two forests as well. Let s say that Forest A has a transitive trust relationship with Forest B. This would mean that all the domains in Forest A have a transitive trust with all the domains in Forest B, and vice versa. However, let s say that there is a trust between Forest B and Forest C as well. This transitive trust between Forest B and Forest C will not flow to Forest A. So domains within Forest A and Forest C will not have any trust relationships between them unless you manually configure a trust between Forest A and Forest C. See Figure 4.12 for an illustration of this concept.
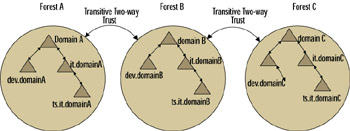
Figure 4.12: Transitivity of Forest Trusts
| Exam Warning | Two-way transitive trust relationships are possible only if your forest is operating in the Windows Server 2003 forest functional level. We ll be talking about domain and forest functional levels later in this section. |
A nontransitive trust is similar to the way that trust relationships functioned in Windows NT4.0: The trust is limited to the domains where it was explicitly configured. As we ve already discussed, a number of transitive trust relationships are created by default in Windows Server 2003. This level of transitivity can be a deciding factor in your security design, since if you need a domain to have absolutely no default trust relationships with any other domains in your organization, you should consider creating a separate forest. (You ll often hear this referred to as a security boundary . To completely isolate resources, you should use the forest as the security boundary, rather than the domain.) A number of trust relationships in Windows Server 2003 are nontransitive by default; we ll be talking more about each one in the next section.
Designing Forest and Domain Trust Models
Trust relationships will be an integral part of your security design when you need to create user access for separate businesses or departments with differing security requirements. There may also come a time when you will be adding or removing domains from your Active Directory structure because of an event such as a company merger or branch closure. These and other business-oriented events can trigger a need to reconfigure your domain and security structure to accommodate these types of changes. The use of domain and forest trusts will be a great asset in designing your environment for both security and ease of management. You should also be familiar with the different types of trusts that are available to you and when to use each type or model to best accomplish the task at hand. In the following sections we will discuss the various types of trust.
Default Trust Relationships
The default trust relationship that is available with Active Directory is a two-way transitive trust. This means that every time a new domain is added to the forest, an automatic two-way transitive trust is created between the new child domain and its parent domain. In the same context, every time a new domain tree is introduced into the forest, an automatic two-way trust is created between the new tree and the forest root.
External Trusts
You ll create an external trust to form a nontransitive trust with a domain that exists outside your Windows Server 2003 forest. External trusts can be one-way or two-way and should be employed when users need access to resources located in a Windows NT 4.0 domain or in an individual domain located within a separate Windows 2000 or Server 2003 forest with which you haven t established a forest trust. You ll use an external trust instead of a forest trust if the trusting domain is running Windows NT 4.0 or if you want to restrict access to another forest simply to resources within a single domain. You can create external trusts using either the GUI interface or the command line. As with most of the functions discussed in this chapter, to perform these procedures you must be a member of the Domain Admins or Enterprise Admins group or you must have been delegated the appropriate authority by a member of one of these groups.
Creating an External Trust With the Windows Interface
-
Click Start Programs Administrative Tools Active Directory Domains and Trusts . Enter the appropriate username and password to run the utility if you ve configured the shortcut to use RunAs .
-
Right-click the domain that you want to create a trust for, and click Properties .
-
From the Trusts tab, click New Trust and then Next .
-
On the Trust Name screen, enter the DNS or NetBIOS name of the domain that you want to establish a trust with, then click Next .
-
The next screen allows you to establish the Trust Type. Click External Trust , then click Next to continue.
-
From the Direction of Trust screen, select one of the following:
-
Two-way will establish a two-way external trust. Users in your domain and the users in the specified domain will be able to access resources in either domain.
-
One-way incoming allows users in your Windows Server 2003 domain to access resources in the trusting domain that you specify, but the trusting domain will not be able to access any resources in the 2003 domain.
-
One-way outgoing is the reverse of one-way incoming, allows users in the external domain to access resources in your domain, but your users will not be able to connect to resources in the external domain.
-
-
Click Next when you ve determined the direction of the trust you re creating. On the Outgoing Trust Properties sheet, you can choose one of the following options:
-
To allow users from the external domain to access to all resources in your Windows Server 2003 domain, select Allow authentication for all resources in the local domain . (You ll most commonly select this option if both domains are part of the same company or organization.)
-
To restrict users in the external domain from obtaining access to any of the resources in your domain, click Allow authentication only for selected resources in the local domain. This option should be used when each domain belongs to a separate organization. Once you ve made your selection, click Next to continue.
-
-
If you have Domain Admin or Enterprise Admin access to each domain involved in the trust relationship, you can create both sides of an external trust at the same time. Click Both this domain and the specified domain on the Sides of Trust page.
Exam Warning As a best practice, Microsoft recommends using the RunAs function to perform most trust procedures. You can configure Active Directory Domains and Trusts to use the RunAs function by right-clicking the shortcut and selecting RunAs . You ll be prompted for the username and password that you want to use to access the administrative utility. If you leave the logon information blank, you ll be prompted to enter it every time you launch the utility.
Selecting the Scope of Authentication for Users
Once you ve created a trust relationship between two separate forests, you ll need to indicate the scope of authentication for users from the trusted domain. You can either allow users in the trusted forest to be treated as members of the Authenticated Users group in the local forest, or you can specify that users from the other forest must be granted explicit permission to authenticate to local resources. (You ll hear the latter option referred to as an authentication firewall .) If users from the trusted domain are not treated as members of the Authenticated Users group in the trusting domain, they will only be able to access any resources for which they have been granted specific permissions. This is a more restrictive means of granting access and should be used when the trusting domain contains extremely sensitive or compartmentalized data. Specify the scope of authentication for any trusts you ve created using the following steps:
-
Click Start Programs Administrative Tools Active Directory Domains and Trusts .
-
Right-click the domain that you want to administer, and select Properties .
-
On the Trusts tab, select the trust that you want to administer under Domains trusted by this domain (outgoing trusts) or Domains that trust this domain (incoming trusts) and do one of the following:
-
To select the scope of authentication for users who authenticate through an external trust, select the external trust that you want to administer, and then click Properties . On the Authentication tab, click either Domain-wide or Selective authentication . If you select Selective authentication , you need to manually enable permissions on the local domain and on the resource to which you want users in the external domain to have access. Otherwise, the users from the trusted domain will automatically be added to the Authenticated Users group in the trusting domain.
-
To select the scope of authentication for users authenticating through a forest trust, click the forest trust that you want to administer, and then click Properties . On the Authentication tab, click either Forest-wide or Selective authentication . If you select Selective authentication , you need to manually enable permissions on each domain and resource in the local forest that users in the second forest should be able to access.
Exam Warning Selective authentication is available only with external and forest trusts. It cannot be used with a realm trust.
-
Realm Trusts
Windows Server 2003 allows you to create a trust relationship with an external Kerberos realm, allowing cross-platform interoperability with other Kerberos services such as UNIX and MIT-based implementations . You can establish a realm trust between your Windows Server 2003 domain and any non-Windows Kerberos V5 realm as shown in Figure 4.13. This trust relationship will allow pass-through authentication, in which a trusting domain (the domain containing the resources to be accessed) honors the logon authentications of a trusted domain (the domain containing the user accounts). You can grant rights and permissions in the trusting domain to user accounts and global groups in the trusted domain, even though the accounts or groups don t exist in the trusting domain s directory. Realm trusts can also be either one-way or two-way.
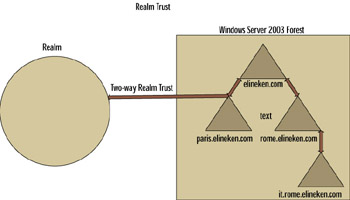
Figure 4.13: Realm Trusts
You can create a realm trust using the Active Directory Domains and Trusts GUI or the netdom command-line utility. To perform this procedure, you must be a member of the Domain Admins or Enterprise Admins group or you must have been delegated the appropriate authority by a member of one of these groups.
Shortcut Trusts
Authentication requests between two domains in different domain trees must travel a trust path ”that is, a series of individual relationships between the two domains. This can be a somewhat lengthy process within a complex forest structure, but you can reduce this process through the use of shortcut trusts . Shortcut trusts are one-way or two-way transitive trusts that you can use to optimize the authentication process if many of your users from one domain need to log on to another domain in the forest structure.
As illustrated in Figure 4.14, the shortcut trust between Domain A and Domain F will shorten the path traveled for User1 s login request between the two domains. In the figure, UserA must access the printer in Domain F by referring to the trust relationships between Domain A and Domain B, then between Domain B and Domain C, and so forth until reaching Domain F. The shortcut trust creates a trust relationship directly between Domain A and Domain F, greatly shortening the authentication process in an enterprise domain with a large series of forest trust relationships.
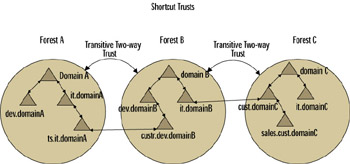
Figure 4.14: Using a Shortcut Trust
Objective 2.2.3: Designing Security for Interoperability
When you re dealing with domains that are still running Windows NT or earlier, it is important to note that the only trust relationships that are possible are trust relationships that you set up manually. If you wanted a two-way trust between an NT4 domain and a Windows Server 2003 domain, you would need to create two one-way trust relationships, one in each direction.
Whenever you are supporting down-level domains and controllers with Windows Server 2003, you need to be aware of the concept of domain and forest functional levels on your network. You probably recall that in Windows 2000, you were able to configure your Active Directory domains in either mixed mode or native mode. Mixed-mode operation provided backward compatibility for any remaining NT4 backup domain controllers (BDCs) still existing on your network. Mixed-mode domains could contain Windows NT 4.0 backup domain controllers and were unable to take advantage of such advanced Windows 2000 features as universal security groups, group nesting, and security ID (SID) history capabilities, as well as other Microsoft packages such as Exchange 2000. When you set your domain to native mode, these advanced functions became available for your use.
Windows Server 2003 takes this concept of domain functionality to a new level, allowing you to establish four different levels of domain functionality, with differing feature sets available, depending on your network environment. The four domain functional levels available in the new release of Windows Server are as follows :
-
Windows 2000 mixed
-
Windows 2000 native
-
Windows Server 2003 interim
-
Windows Server 2003
The default domain functional level is still Windows 2000 mixed mode, to allow you time to upgrade your domain controllers from Windows NT 4.0 and Windows 2000 to Windows Server 2003. Just as in the previous release of Windows, however, when you raise the functional level, advanced domainwide Active Directory features become available. Just as NT4 controllers were not able to take advantage of the features available in Windows 2000 native mode, Windows 2000 controllers will not be aware of the features provided by the Windows Server 2003 level of domain and forest functionality.
In Table 4.1, you can see the four levels of domain functionality available in Windows Server 2003 and the types of domain controllers that are supported by each.
| Domain Functional Level | Domain Controllers Supported |
|---|---|
| Windows 2000 mixed (default) | Windows Server 2003 family |
| Windows 2000 | |
| Windows NT4 | |
| Windows 2000 native | Windows Server 2003 family |
| Windows 2000 | |
| Windows Server 2003 interim | Windows Server 2003 family |
| Windows NT4 | |
| Windows Server 2003 | Windows Server 2003 |
| Test Day Tip | The Windows Server 2003 interim domain functional level is a special level that s available if you re upgrading a Windows NT 4.0 PDC to become the first domain controller in a new Windows Server 2003 domain. |
When you upgrade the domain functional level of your Windows Server 2003 domain, new administrative and security features will be available for your use. Just as when you set Windows 2000 to either mixed or native mode, specifying the domain functional level is a one-way operation; it cannot be undone. Therefore, if you still have domain controllers that are running Windows NT 4.0 or earlier, you shouldn t raise the domain functional level to Windows 2000 native. Likewise, if you haven t finished migrating your Windows 2000 controllers to Windows Server 2003, you should leave the domain functional level lower than Windows Server 2003.
Similar to the domain functional level, Windows Server 2003 has created different forest functional levels that can enable new Active Directory features that will apply to every domain within an Active Directory forest. When you first create a Windows Server 2003 Active Directory forest, its forest functional level is set to Windows 2000. Depending on your environment, you can consider raising the forest functional level to Windows Server 2003; however, just as with the domain functional level, changing the forest functional level is a one-way operation that cannot be undone. Therefore, if any of your domain controllers are still running Windows NT 4.0 or Windows 2000, you shouldn t raise your forest functional level to Windows Server 2003 until your existing controllers have been upgraded.
4.2 details the types of domain controllers that are supported by each of the forest functional levels.
| Forest Functional Level | Domain Controllers Supported |
|---|---|
| Windows 2000 (default) | Windows NT 4.0 Windows 2000 Windows Server 2003 family |
| Windows Server 2003 interim | Windows NT 4.0 Windows Server 2003 family |
| Windows Server 2003 | Windows Server 2003 family |
| |
Windows Server 2003 Domain and Forest Functionality
When you raise the domain and/or forest functional level within your Active Directory environment, certain advanced features will be available for your use. At the domain level, the Windows Server 2003 functional level provides the following advantages that are not available in either Windows 2000 mixed or native mode. You can enable these features on a domain-by-domain basis:
-
Domain controller rename tool This Resource Kit utility allows you to rename a domain controller if your business or organizational structure changes.
-
SID history Allows you to migrate security principals from one domain to another.
-
Converting groups This enables you to convert a security group to a distribution group, and vice versa.
-
InetOrg Person These objects ease the migration from other LDAP-enabled directory applications to Active Directory.
-
lastLogonTimestamp attribute Keeps track of the last logon time for either a user or computer account, providing the administrator with the ability to track the history of the account.
Raising the forest functional level creates the following features that you can implement throughout your Windows Server 2003 forest:
-
-
Domain rename Allows you to rename an entire Active Directory domain.
-
Forest trusts Enable two-way transitive trusts between separate Windows Server 2003 forests. In Windows 2000, trusts between forests were one-way and intransitive .
-
InetOrg Person These objects can now be made available throughout your entire Windows Server 2003 forest.
-
Defunct schema object You can now reuse the object identifier, the ldapDisplayName, and the schemaIdGUID that are associated with a defunct schema object, whether a class or an attribute.
-
Linked value replication This feature allows individual values of a schema attribute to be replicated separately. In Windows 2000, if an administrator or application made a change to a member of a group, for example, the entire group needed to be replicated. With linked value replication, only the group member that has changed is replicated, greatly improving replication efficiency and speed in larger environments.
-
Dynamic auxiliary classes These allow you to link auxiliary schema classes to an individual object rather than entire classes of objects. They also serve to improve replication under Windows Server 2003.
-
Global catalog replication This has also been improved by propagating only partial changes when possible.
-
| |
EAN: 2147483647
Pages: 122