2.4 Types of DOS Viruses
2.4 Types of DOS Viruses DOS computer viruses (we are purposely ignoring macro viruses for now) can be classified in the following major categories:
2.4.1 Boot VirusesIn order for a pure boot virus to infect a hard drive, the PC must have attempted to boot with an infected floppy diskette. I run into people all the time with PCs that are infected with boot viruses and are convinced they did not boot, even accidentally , with a floppy diskette. But it had to have happened ! What these people mean is they did not intentionally mean to boot with a floppy diskette. Often they don't understand that a boot virus can be present on any diskette. It doesn't have to be bootable. Every DOS-formatted diskette contains a limited boot sector containing error messages and other miscellaneous code. And a virus can hide in there without the disk having the necessary operating system files needed to boot a PC. Most of the time, a friend or coworker gives someone an infected floppy diskette to transfer some datafiles to his computer. After he retrieves datafiles from the diskette, he forgets to remove it from the floppy drive and shuts down his PC. The next morning he turns on his PC, gets the familiar, "Nonsystem disk or disk error. Replace and strike any key when ready..." error message. He spends a few seconds trying to figure out why his system isn't starting as expected, then realizes the mistake, pops out the floppy diskette, and restarts the computer. Too late! If the diskette was infected by a boot virus, it has been transferred. The PC hard disk is infected. Every time the PC starts, the virus gets loaded into memory. Every floppy disk put in the PC can now be infected, and the whole cycle starts over again. This process is shown in Figure 2-8. Figure 2-8. Boot virus life cycle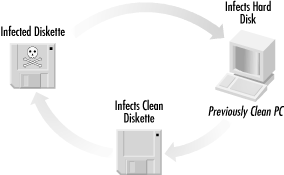 Pure boot sector viruses can only spread if you boot from an infected floppy diskette. You can retrieve and save files all day long to an infected diskette, but as long as you didn't boot with it, you're safe. In the past, to eliminate the biggest threat of computer viruses all you had to do was not boot from a diskette. Boot sector viruses replace a PC's normal boot code and take control during the initial stages of the PC's start sequence, although there are several different places where it can insert itself in the process. The very first IBM PC virus, Brain , was a boot virus. Stoned , Michelangelo , AntiEXE , Ping-Pong , and Monkey are all familiar names of boot viruses. Stoned displays a "Legalise Marijuana" message. Michelangelo formats hard drives . AntiEXE corrupts executable program files. Ping-Pong would send a black ball pinging across the screen. Monkey added a few new tricks and made its removal not quite so simple.
2.4.1.1 How boot viruses infect hard disksA user accidentally leaves an infected floppy diskette in drive A when she turns on her PC. The boot virus is located in the first sector on the floppy diskette that the BIOS and CPU automatically load into memory and execute. The virus gets into memory, checks to see whether it is activating from a floppy diskette or hard disk, finds the hard drive's MBR or DOS boot sector, and moves it (along with other related sectors) to somewhere else on the disk. Since a boot sector isn't a file, a "nice" boot virus will mark the new location for the original boot sector in such a way that it doesn't get overwritten accidentally. More times than not, the boot virus doesn't read the partition table to locate the DOS boot sector and haphazardly writes over the assumed boot sector location at Track 0, Head 1, Sector 1. This works fine in the majority of cases, but will crash the computer if you don't have an active DOS partition as your first logical partition. Most boot viruses are looking for DOS boot sectors and haven't the coding room to check the partition type first. So even if the boot sector contains non-DOS boot code, the virus will assume it is a DOS boot sector. As covered in Chapter 3 and Chapter 4, this lack of error checking is why NT takes such a beating from DOS boot viruses. The virus then writes its own viral boot sector into the original operating system boot sector area and automatically runs on each subsequent PC boot. The virus loads into memory and then runs the original boot sector. The whole process, documented in Figure 2-9, takes place in under a second. Now in memory, the virus can infect any floppy diskette put into the computer system and exert its influence where it likes. Figure 2-9. How a boot virus takes control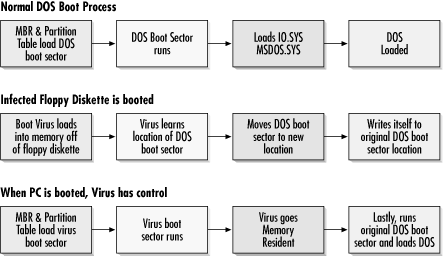 Another common boot virus technique is to move the original MBR to a safe location and replace it with the virus's code. When the PC reboots, the virus runs first from the original MBR location, gets in memory, and loads the original MBR, which then loads the DOS boot sector. Alternately, a boot virus can infect the MBR and partition table, manipulate where they point to, and again place itself in front of the correct boot code. Depending on where in the boot area they infect, a virus can be called a boot sector infector, a master boot record infector, or a partition table virus. Once in memory, most boot viruses intercept interrupt 13h, the BIOS routines for reading and writing to floppy diskettes and hard drives. This allows the virus to write to floppy diskettes when all the user thought was going on was file retrieving. Every floppy disk they put in the infected PC is now infected and the cycle continues. This is as simple as the boot virus infection process gets. Most boot viruses add other subroutines to do damage (called a payload), display messages, or further manipulate the computer. Many viruses, including the original Brain boot virus, add extra code to pass along the original boot sector to any disk inspection tools looking for the boot sector. This way, they have a better chance of hiding (stealth). However, anyone looking with the right tools without the virus in memory (i.e., booting from a known, clean, write-protected DOS diskette) will see the new bogus boot sector. 2.4.1.2 Special boot virus delivery methodsDroppers are programs that, when executed, exist only to write a virus to a disk. Virus writers and antivirus researchers alike will use dropper programs to share boot viruses via email. When used maliciously by a virus spreader, these files arrive as a Trojan program, drop off a virus, and then erase themselves . Today, almost any other type of program can be a dropper file, including macro viruses and malicious HTML. There are droppers that infect boot sectors, create executable files, and infect Microsoft Office applications.
Multipartite viruses use more than one avenue of infection. The typical multipartite virus infects .COMs , .EXEs , floppy disk boot sectors, and hard drive MBRs. When you boot with a floppy diskette containing a multipartite virus, often it will infect your hard drive's boot sector and start to infect executable files. Because they contain subroutines to infect in more than one way, their code is often large. Unlike a regular boot virus that may take up two sectors, a multipartite virus may take up to six sectors or more. Many multipartite viruses act like a dropper program. They begin as a file-infecting virus that infects the boot sector of the hard disk. The hard disk can infect floppy diskette boot sectors, but the resulting boot sector virus usually cannot then infect other executable files. These types of viruses are often using the file infecting portion as a conduit to drop off the boot sector infecting portion. In practice, most boot viruses are passed on a floppy diskette and not via a dropper or multipartite virus. Whether or not the virus remains in memory after activation also determines its mechanism of action. 2.4.2 Memory ResidencyA nonmemory resident (also known as nonresident ) virus executes, does its business, and then exits. It doesn't activate again until the next infected host file is started. Nonresident viruses usually infect slower than their memory-resident counterparts. They have to do the file infecting quickly enough after the host is executed so the user doesn't become too suspicious. Infecting multiple files takes time. On the other hand, memory-resident viruses use host files as a launching point and reside in memory long after the original host file has exited. They are also significantly harder to write. A memory-resident virus will hook itself into the interrupt subroutines. Then whenever a user or program requests a particular service, the virus has first choice on what it wants to do. For instance, most boot viruses will stay in memory and infect any floppy disk that is accessed for any reason. The large majority of memory-resident viruses infect other program files when they are executed. They lie in wait, looking for newly executed files to infect. Other viruses infect program files only when they are copied . 2.4.3 File-Infecting VirusesComputer viruses, by their very definition, use other host code to propagate. File-infecting viruses write themselves to the other host files. These program files are usually executable .COM or .EXE files; but can be overlay files , datafiles , .SYS , .DLL and .OBJ files. File infectors can be classified as overwriting , appending , companion , or other . 2.4.3.1 Overwriting virusesOverwriting viruses are the easiest kind to write, as they run and save themselves right over the code of the host file. As demonstrated in Figure 2-10, this permanently damages the host file. Depending on the virus and the host file, this can affect functionality or completely bypass the original program. In most cases, the only recovery is to replace infected files with clean copies. Figure 2-10. Simple overwriting virus The simplest overwriting virus needs only four DOS interrupts to work. The Tiny-32 virus is considered one of the smallest, working viruses created to date. Example 2-1 shows the interrupts it contains as excerpted from its source code. Example 2-1. Excerpts of Tiny-32 virus source codeMOV AH, 4E ;setup to find a file INT 21 ;find the host file MOV AX,3D02 ;setup to open the host file INT 21 ;open host file MOV AH, 40 ;setup to write file to disk INT 21 ;write to file DB *.COM ;what files to look for The Tiny-32 virus doesn't do anything but infect the first listed .COM file in the current directory, so it really isn't a viable virus. However, it demonstrates that it doesn't take much to write a virus. There have been a few demonstration viruses written in less than 15 bytes. All file-infecting viruses are just more sophisticated versions of the same thing: find a host file, open it, write itself to the file, and close the file. The larger viruses just do with more finesse and contain more instructions to implement damage "payloads," display graphics, make sounds, corrupt files, or hide from antivirus programs. Often when I am looking at a suspected DOS virus, I will open the file using DEBUG.EXE and use the (U) Unassemble command to view its assembly language source code. If I see the interrupts listed in Table 2-1, I at least know the suspected file has the capability to manipulate files. When looking for interrupts in assembly language the action of interrupt function is determined by the register values above it. Using Example 2-1, interrupt 21h is preceded by the value 4E. This can be interpreted as interrupt 21h, 4Eh, or the File Find instruction. Of course, there are dozens of other interrupts, 13h for example, which virus writers can use to do their dirty work. Usually I look for other text signs, such as *.COM , *.EXE , or some text that looks like a virus in the source code using the (D) Dump command. Other times I will just use the TYPE or EDIT commands to take a quick look inside (covered later on in this chapter). It takes a reasonable understanding of assembly language to be able to understand what you are viewing when peering inside a DOS binary file. Most people are better off letting antivirus scanners do the diagnosing for them.
Budding virus writers will usually start off writing an overwriting virus as their first attempt, because it is the easiest to write. It has to do only the following: find a file, open the file, write itself to the file, close the file . The routine is the same regardless of what type of file it's infecting. It doesn't care about saving the original bytes. It just overwrites the host file with itself. Since the virus writes itself over the original host file, users detect the damage pretty quickly. Whatever is infected usually no longer works, although there are overwriting viruses that go out of their way to hide in expendable portions of the host. As the confused end-user continues to try to rerun the infected program in a desperate attempt to make it work, the overwriting virus finds one or more additional hosts and the process continues. An overwriting virus may trick the user into trying over and over to start the same infected host file by displaying a false error message. The Leprosy virus printed an "Out of memory" error when it was running. A user would type the host file's name over and over again trying to get it to run. Each time the virus would infect six new files. The user would finally stop typing the same filename and assume it was simply corrupted. Imagine her continuing displeasure as more programs began having the same memory problems. 2.4.3.2 Cavity virusesMany executables contain lots of free space, especially large .EXE s. The free space is usually reserved for a data buffer area to store temporary data. Cavity viruses look for program files with large amounts of free space, and if large enough, store themselves there. This overwrites part of the host file, but without increasing the size or harming functionality. When the host file executes, the virus runs and does what it was coded to do. The borrowed buffer area is often overwritten with temporary data, as was intended by the host file, erasing the virus code. By then the virus is in memory or already in a new host. 2.4.3.3 Appending virusesAppending viruses have a lot more work to do as they add themselves to the original host file without destroying it. Appending viruses add themselves at the end of a file, while prepending viruses add themselves to the beginning. First, they must consider what type of host file they will target. Every type of file, .COM , .EXE , .SYS , and so on, has its own file structure that must be maintained after the insertion of the virus. To insert a virus in a .COM file takes one set of commands, to successfully append to an .EXE file, another. Appending viruses, also known as parasitic viruses , are more successful at spreading without quick detection because they maintain the original functionality of their host victim files. I've never heard of anyone noticing the few extra microseconds it takes to run the appended virus code. The basic prepending virus sequence looks like Figure 2-11. Figure 2-11. Simple prepending virus The virus writes itself to the beginning or end of the host file, runs itself first, and then turns control over to the original program. In practice, parasitic viruses can insert themselves anywhere in the program file, although most insert themselves at the beginning or end. The Cmdr Bomber was the first virus to successfully insert itself into the middle of the host file. Most file viruses insert a jump instruction at the beginning of the file that points to the virus code located elsewhere. The virus gains control and then jumps to the new start location of the original program. Lots of file calculations have to be made in order to determine where the different start points are now located. Program files have file headers that set up different initialization variables , and changing a file in any way means the header must be rewritten. Viruses have to recalculate and rewrite program code to correctly modified the file's structure so that its appearance doesn't disrupt its underlying organization. 2.4.3.4 Other executable typesOther types of files can contain executable code. There are lots of viruses that infect device drivers ( .SYS or .DRV ), overlay ( .OVR or .OVL ), and so on. Each type of file structure earns a slightly different method of infection. But like infecting the .EXE and .COM files, the virus writer simply learns how the file is organized and how to appropriately modify the file header so that the first instruction that gets executed is itself. Of course, for each type of file a virus wants to infect, it increases the size of virus code and the chance that it will contain a programming bug. 2.4.3.5 Companion virusesCompanion viruses , also called spawners or twins , were created to get around antivirus programs that checked to see if the original host files were modified. Many antivirus programs are capable of running a checksum algorithm against program files to calculate a mathematical result. Checksumming uses a certain sequence of bytes in the original file and applies it in a calculation. The result is stored for later comparison. If the previously checked program file gets modified, a subsequent run of the checksum algorithm will return a different mathematical value and alert the user that the file was modified. Of course, it was essential that users ran the checksum program prior to infection. Some antivirus programs modified the original file and stored the mathematical result internally. Critics of such techniques rightly claimed that no program, good or bad, should modify program executables. Companion viruses get around checksumming programs by never modifying the host file. They use a weakness in the way DOS handles program files. If you've ever typed in a program file without using its extension, then you've used this DOS "feature." By default, when trying to run a program filename without an extension (e.g., WP and Enter), DOS will always choose .COM files first, .EXE files second, and .BAT files last. Hence, if you were trying to start a program named WP.EXE , you can type in WP and hit Enter. DOS will look for WP.COM first to execute, WP.EXE second, and WP.BAT last. To make matters worse , prior to DOS 5.0, even if you type in the exact filename and extension (e.g., WP.EXE ), DOS didn't particularly care what extension you typed as long as it was a valid program extension. Disregarding what you actually typed, DOS would begin searching for WP.COM first, WP.EXE second, and WP.BAT last. Most of us learned that we could simply enter in the filename and not worry about the extension. This DOS shortcut feature is helpful most of the time. Companion viruses use this DOS peculiarity to their advantage, searching for host files with the extension .EXE . The virus will then make a copy of itself with the same filename, but with the .COM extension. The new .COM file will also have the hidden file attribute set so it does not show up in directory listings, although this does not prevent it from being executed. Hence, if you typed WP and hit Enter, the virus would be executed first by masquerading as WP.COM , do its virus stuff, and then run the original WP.EXE executable. Checksumming programs will not produce an alert because the original host file is unmodified. For a while, this fooled some antivirus programs. Today's good antivirus programs will find the hidden rogue .COM files. Because most people never used checksumming programs as their sole antivirus defense, companion viruses never presented much of a threat.
2.4.3.6 Cluster virusesThe DIR-2 and CD10 viruses employ another technique whereby the original host files are not modified. Cluster viruses place themselves in one area on the disk and then modify the operating system's file storage system in such a way that every file executed runs the virus code first. The virus then runs the original file. Cluster viruses are able to do this by manipulating the DOS system file table . Like the interrupt vector table, this table is a simple database stored in memory. It stores about 20 different pieces of information on each file open in memory, including on what disk cluster the file begins. Cluster viruses manipulate the system file table to point to itself as the starting cluster. Then when the virus is in control, it finds and runs the original program. This type of virus made it harder for antivirus programs to detect and clean infected disks. Because cluster viruses modify the low-level file storage system, they can lead to frequent program crashes and malfunctions. |
| | |
| Team-Fly |
| Top |
EAN: 2147483647
Pages: 176

