Securing Wireless Networks
Despite all the wireless threats, there are many standard ways to secure Wi-Fi networks. To combat the vulnerabilities listed previously, administrators can implement one of the following common security options, listed from weakest to most secure:
-
802.11 Legacy Wireless Security Recommendations
-
WEP
-
VPN Protocols
-
WPA
-
WPA2/802.11i
802.11 Legacy Wireless Security Recommendations
In the past, the following security recommendations were often told to wireless network administrators:
-
Change access point's default SSID
-
Enable MAC filtering
-
Disable DHCP on the access point
-
Require user authentication passwords
-
Turn off SSID broadcasting
-
Change an access point's default administrator password
While each of these options could provide some security, each of them is easily bypassed by a minimally knowledgeable wireless hacker. They are listed in order of growing security importance.
Changing Access Point's Default SSID
Most access points come with a default SSID as pre-configured by the vendor (for example, dlink, linksys). It can be changed from the default to prevent roaming intruders from immediately connecting to the wireless network simply because it matches an existing SSID that the computer previously connected. This has to be the worst advice of all. First, if all the administrator does is change the SSID, the wireless access point will immediately advertise the new SSID. Any passing intruders can immediately detect the new SSID and begin attempting to connect to it. Individuals who recommend this wireless security measure, and it is often recommended, don't understand Wi-Fi networks well. Even so, it is a common usability recommendation, as it allows the user to recognize when they are in the range of a particular known network. If all users kept the vendor's default SSIDs, it is likely that several vendor products would overlap each other, leading to confusion. By changing the default SSID to a unique identifier, the user may be able to easily identify which wireless network is the intended one. However, no user should rely on SSID name alone, as an attacker can easily mimic an SSID to fool the user into connecting to the rogue access point.
Enabling MAC Filtering
Media Access Control (MAC) addresses are used by many network protocols as a basic data-link routing mechanism. In TCP/IP networks, which Wi-Fi networks usually are, MAC addresses are used to route packets from source to destination machines on the same local area network. Most access points, if not all, allow the administrator to define a list of allowed (that is, a whitelist) MAC addresses. Computers with unregistered MAC addresses will not be allowed to access the Wi-Fi network. While there is some value in this defense, MAC addresses can easily be sniffed off wireless networks, and once legitimate values are found, they can be used by intruders to force their way onto the meagerly protected network.
Disabling DHCP on the Access Point
Most wireless nodes are assigned dynamic IP addresses by the access point's DHCP services. It is so common that most users of wireless networks expect it to always be that way. One very weak security trick would be for an administrator to assign valid, static IP addresses to all legitimate nodes. Roaming intruders not in the know would not be assigned a valid IP address as they normally expect, and their connection to the access point would appear broke. Unfortunately, simple wireless sniffing will reveal the valid IP address ranges. A sniffing computer, in promiscuous mode, doesn't need a valid IP address to sniff wireless network traffic.
Requiring User Authentication Passwords
Requiring the user to type in their Windows logon name and password to connect to the wireless network has some value, however, alone, logon credentials could be transmitted in clear text or near clear text. Any intruder sniffing on the wireless network could see all shared data streams and network information.
Turning Off SSID Broadcasting
By default, all wireless access points will frequently broadcast their SSID. Turning off SSID broadcasting has some security value. As Figure 13-10 shows, disabling SSID broadcasting is called Enable Hidden Wireless on the example access point. Many clients, including Windows will have a hard time finding and connecting to non-broadcast Wi-Fi networks. However, hackers have developed techniques and tools to detect these types of networks.
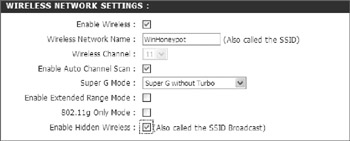
Figure 13-10: Disabling SSID broadcasting on access point
Vista has been improved to allow non-broadcast networks to be added to the Preferred Network list. Non-broadcast networks will appear as Unnamed Network in Vista.
Disabling SSID broadcasting was initially thought to provide an additional layer of wireless security, but further analysis has proven this practice to be inadvisable in most cases. This is because while the access point does not advertise its presence, all the pre-configured clients looking for it do. The clients will send out probe packets looking for the "hidden" access point, and a listening attacker can intercept those broadcasts, make a rogue access point with the same name, and attempt to re-direct the clients to the invalid access point.
Allowing SSIDs to be broadcast by the access point puts the security requirement at the access point and its configuration, rather than at the client and its user. A client will not provide a rogue access point with the name of its preferred networks if it is configured to only connect to broadcast SSIDs.
More information as to why non-broadcast SSIDs are not recommended can be found at http://www.microsoft.com/technet/network/evaluate/hiddennet.mspx.
Changing an Access Point's Default Administrator Password
This is a solid security recommendation. Most access points come with vendor supplied default passwords (if any). For example, many D-Link access points come with an administrative logon name of admin with no default password. There are many lists all over the Internet containing every vendor's default logon credential. My favorite site is http://www.phenoelit.de/dpl/dpl.html.
When a new access point is first plugged in and accessed for the first time, its admin password should be changed to something ten characters or longer. Many access points also allow the administrator's logon name to be changed. Do that as well, and securely store both values so they can be retrieved later when needed. Some access points also have a read-only user (often called user). If this type of default account exists, change its password (and name, if possible), as well.
| Note | Since the WEP encryption itself may still be cracked, you may find that your wireless access point is used by attackers to mount other attacks, engage in criminal behavior traceable back to your network, or simply deny you the bandwidth for which you have paid. |
WEP
Wired Equivalent Privacy should be used as a last resort, as a fallback position when legacy components are involved. If WEP must be used, enable 128-bit (or 256-bit) keys. The WEP shared key should be random or complex, and not contain whole words that can be found in the dictionary. If the components allow it, choose Dynamic WEP, an improved WEP protocol where the keys are dynamically updated at frequent intervals. Unfortunately, even the latest, strongest versions of WEP are not as strong as WPA or WPA2 (used with appropriate settings, of course).
Because a primary means of attacking WEP is to capture enough packets to crack the encryption, a protection mechanism you can use, if WEP is required, is to issue a new WEP key frequently. The frequency of change will depend on how much traffic is sent across the network-a fully saturated network might be crackable if its WEP key is not changed every few hours. A home network might be able to get away with changing the WEP key every few days or weeks. The more frequent the change, the better. Some of the newer WEP protocols (called dynamic WEP), can change the WEP key every few minutes. However, whenever possible, WEP, no matter how updated, should be abandoned in favor of new wireless protection protocols.
VPN Protocols
Consider using an external point-to-point client VPN protocol, such as SSL, IPsec, or a third-party VPN product, if all you have is WEP. You can set the access point to WEP or weaker security, but require an authenticated point-to-point VPN connection in order for clients to access any resources beyond the access point. This will provide protection to each client's personal data stream, and stop external sniffing and man-in-the-middle attacks.
Using WPA
The WPA2 standard gained final approval in 2006. Many older network cards and access points do not support WPA, although some will with a firmware or software upgrade. If your Wi-Fi components support WPA, but not WPA2, enable WPA with a long and/or complex pre-shared key. Weak pre-shared keys can still allow any protocol using them to fall prey to successful attacks.
Using WPA2/802.11i
All Wi-Fi administrators, whether at home or at work, should be working toward implementing WPA2/802.11i. WPA2 Personal, with its pre-shared key, is stronger than WEP, and just as easy to setup. WPA2 Enterprise has more difficult setup requirements, but using an appropriately configured PKI service can make certificate distribution easier than most administrators can imagine. Microsoft Certificate Services can distribute computer and user digital certificates automatically as soon as the computer or user logs on successfully for the first time.
WPA2 can also be used without digital certificates, using PEAP-MSCHAPv2. But the best Wi-Fi security that can be had is using WPA2 with smart cards and separate PIN. Two factor authentication using digital certificates should prove to be the most resistant to attack wireless protection currently available. And if the user or computer loses its authority, the Certificate Services administrator can revoke the digital certificate and the wireless node can no longer connect to the network.
EAN: N/A
Pages: 163