High-Risk File and Program Examples
What is and isn't high-risk is different for different organizations. It is up to each system administrator to review the files and programs running on the computers under their control and determine what should and shouldn't be executing. While no administrator will come up with the same list, here are some starting points.
List of Potentially Malicious File Types
Table 5-1 shows many high-risk file types by extension and gives related details. You can use this list as a starting point to check off what is and isn't needed in your environment. This list can also be used in Chapter 11, "Protecting E-mail."
Go to www.wrox.com to get an updated list of potential malicious files.
As exhaustive as this list may seem, many readers can probably add additional high-risk files. This list does not contain every file extension that could be used maliciously, just the most likely candidates. To find out all the file extensions registered with a particular Windows computer, open up Windows Explorer and choose Tools ð Folder Options ð File Types (see Figure 5-2). The average Windows installation contains hundreds of file associations. Each file association should be considered potentially exploitable and measured against the potential risk and benefit. With many file extensions (e.g., Remote Desktop Protocol), what can potentially be exploited is high, but the relative risk of exploitation is low because attackers aren't commonly using that method. The highest-risk files for your organization should be monitored, and the risk of attack minimized (see "Defenses," below).
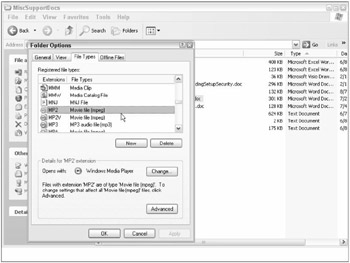
Figure 5-2
| Note | A great web site to use for file extension research is The File Extension Source (http://filext.com). |
EAN: 2147483647
Pages: 122