Overall Defense Strategy
One of the most welcome changes in the computer security field over the last decade is its maturing rise toward becoming a legitimate profession. Professions have guiding practices, certifications, and membership-based governing bodies. Certifications and governing bodies exist to help committed professionals follow ethical, best practices and to advance the profession as a whole. Every profession has a credo of accepted beliefs and practices that members should follow. These guidelines lead to a better overall work product, more educated practitioners, and the respect of other legal and financial bodies. Guiding principles help professionals make better, more consistent decisions when faced with unusual situations.
For example, accountants (my former profession) follow something called Generally Accepted Accounting Principles (GAAP). GAAP is a collection of official opinions and statements (http://cpaclass.com/gaap/gaap-us-01a.htm) that accountants can consult when faced with an accounting situation. They are particularly helpful with unique financial circumstances that the normal accounting rules haven't covered. GAAP puts out guiding principles (such as "revenues must be matched to the expenses that created them") to help accountants make the right decision when tempted by others to present a more optimistic (i.e., fraudulent) outcome. In recent years, several CEOs and corporate accounting officers have been arrested for not following GAAP. With this in mind, I want to introduce this book's guiding security principles. They lie behind all the statements and recommendations stated elsewhere.
We Will Never Defeat Hackers and Malware
We will never defeat hackers and malware! This is perhaps a bitter pill to swallow, but it's true. Viruses, worms, and hackers have been around since before Microsoft was in existence and will be around long after it is nothing but a historical footnote. Many computer administrators mistakenly believe that once Microsoft goes away, hackers and malware will too. They are fools without an appropriate understanding of history. The first viruses weren't on Windows PCs. They weren't even on personal computers. They, and their ilk, appeared on mainframe computers that were popular at the beginning of the computer age. They moved to Apple computers when they became popular and moved to Microsoft Windows when it became the dominant platform. Malware and hackers exist on every platform.
As long as computers allow flexibility and users have human ingenuity, there will be hacking and exploits. The best we can do is to strengthen our computers and networks to a point where other targets are more attractive and more likely to be broken into. Don't adopt the attitude that somehow there will be less hackers in the future and users will be eventually be allowed to compute without the fear of maliciousness. If fact, we do a relatively poor job at preventing old attacks, much less addressing the new attacks. Attacks from years ago are still very popular and successful. In the future, there will probably be more ways to exploit a computer, not less. I know many security experts who have burnout because their job just keeps getting harder and harder — and not easier.
Whatever Is Popular Gets Hacked
Whatever software is popular at the moment invites hackers. Many people believe that Microsoft Windows gets hacked so much because it has poor security. This may have been true in the days of Windows 95, but it certainly isn't true today. Windows XP and Windows Server 2003 have some of the best security of any popular desktop operating system. It's just that it runs on over 95% of client desktops, and popularity breeds attacks. This explains why the open-source Apache web server program, with 70 percent of the web server market, has had dozens of successful exploits against IIS's handful in the same time period. Is IIS more secure than Apache? I'm not sure. It would take a long-term analysis by experienced security evaluators to reach that conclusion. What I do know is that Apache is the most popular server and it gets hacked more.
Some Microsoft haters suggest that end users move to other platforms, such as open-source alternatives Linux, Firefox, and OpenOffice. These are the same people who often recommend that users move from Microsoft Office document formats to some other file format such as PDF or RTF. What they don't realize is that both of those file formats have already been exploited, the Adobe PDF format several times (http://secunia.com/search/?search=Adobe+Acrobat).
And if the computing world up and moved in mass to a new platform or new program, hackers would just follow. Just ask Firefox Internet browser users for their experiences. The open-source Firefox browser was released as a "secure" alternative to Microsoft's Internet Explorer. It has picked up 27 vulnerabilities since its release in August 2004. As I write this chapter, 2 of the 27 are unpatched (http://secunia.com/product/4227), and this is with only a 10% market share (www.clickz.com/stats/sectors/traffic_patterns/article.php/3500691). Let Firefox surpass Internet Explorer in popularity and it is sure to gain the notice of even more hackers.
Some other examples: Apple Corporation's new Macintosh operating system, OS X, is gaining Apple slightly more market share. OS X has had 63 (http://secunia.com/product/96) vulnerabilities patched since its release. Cisco, the world's most popular Internet router company, releases patches nearly every month. Its new router operating system, IOS 12.x, has had 36 public vulnerabilities (http://secunia.com/product/182). RedHat Linux has over 99 (http://secunia.com/product/1343).
The truth is that any software can be hacked. There is no perfect code without bugs and potential exploits. What matters is how seriously the vendor takes security and how quickly they respond to security vulnerabilities. You may end up initially decreasing your overall security exposure by switching to a less hacked platform or piece of software, but then you pick up interoperability and training issues. And if your new platform becomes popular, you're back in the same place after all the pain and bloodletting. Instead, if the vendor is being responsive to security problems, then spend your effort on securing your current environment instead of looking for temporary false solutions. On a related note, if you want to know where hackers and malware will attack in the future, just look for the popular software.
There Is No Perfect Security Solution
There is no single solution that will be best for all users and environments. For instance, users often ask me to recommend the "best" antivirus program. That's like asking a car mechanic for his recommendation for best car. It depends on what you value most. The car mechanic might value a car noted for its low-cost reliability, while maybe the buyer wants a sports car or something low on gas mileage. It's the same way with computer security. There are many good solutions, none perfect, and what works best for one organization doesn't work great for another. That's why if any security expert claims to know what is best for your environment without learning about the environment first, you're talking to a marketing guy, not a security techie.
Most people don't even really want the best security. The best security is almost always unusable in most organizations. The popular saying is that if you want a secure computer, lock it up in a closet without a network card or keyboard. If you don't want to be attacked from the Internet, don't allow the computer to connect to it. Outside of those types of efforts, everything else is just a cost/benefit trade-off. Usually, the more secure you make a system, the less user-friendly it is. A good security solution weighs end-user and management acceptance against the potential problems the security defense is surely to cause. The best security defenses are highly accurate at both preventing maliciousness and not preventing legitimate computing. In this book, each defense technique is taught along with best practice recommendations, but ultimately each decision must be decided by the administrator.
Focus on the Right Problem of Automated Malware, Not Hackers
As Chapter 1 covered, more than 99% of the attacks and attempted exploits any computer system will endure are automated malware. There are different defenses with higher levels of success that can be implemented if you accept this understanding. You still need to fear the dedicated malicious hacker, just don't focus the majority of your efforts on the wrong problem. The solutions presented in this book address both but concentrate on automated malware.
If a User Can Be Tricked into Running a Malicious Program, It Is Game Over
If users only ran the legitimate, authorized programs they needed to do their job, the life of the computer administrator would be an easy one. Instead, users frequently run programs they shouldn't, visit web sites they shouldn't, and execute every file attachment. Ultimately, if you cannot prevent end users from executing unauthorized software, everything else is for naught. That's because a malicious program, if so programmed, can get around any computer security defense. Malware can bypass any firewall, bypass any antivirus scanner, and undo any computer security protection. There is no perfect defense against executed malware. The key then is to prevent end users from running unauthorized programs and code they should not be executing. Much of this book is dedicated to those types of protections, especially Chapter 9, "Stopping Unauthorized Execution."
Security-bY-Obscurity Works!
Too many security experts claim that security-by obscurity doesn't work when it is obvious that it does. And although security-by-obscurity doesn't work as a complete defense by itself, I'll venture to say that it is one of the best ways to secure a computer! Anyone that disagrees with this statement, just move your web server from port 80 to some other random port and compare before and after attack statistics. This chapter covers the best security-by-obscurity tips.
Don't Let End Users Make Security Decisions
I'm not a big believer in end user education. It's highly overrated. With few exceptions, coordinated end-user education programs have never worked! Think about it. The most prolific automated threat is malicious e-mail attachments. As reported in Chapter 1, they are involved in nearly 92% of all successful attacks. The entire class of attacks could be defeated if people did not execute unexpected file attachments. Is there a computer user alive who has not heard the warning, several times, not to execute strange file attachments? And even if nearly everyone on your network follows this advice, it takes only one clueless end user to infect the whole network.
Most end users aren't very computer security aware, and even if they are, they are more likely to choose the wrong answer when faced with a particular security decision than the reader of this book. When end users get e-mail file attachments, Windows warns them that the file attachment could be malicious and cautions them against execution. The default decision is not to execute the attachment. End users need only press their Enter key or click the OK button and the system will do the right thing. Still, end users continue to go out of their way to make the wrong choice.
How many computer systems have you been on where the Microsoft Automatic Updates program has downloaded all the current patches and is just waiting for the end user to acknowledge and apply them but the user has clicked the "do it later" button? I frequently see patches behind for eight months or more. When I query the end user, he or she acknowledges being bugged by the update warning, but still they go unpatched.
End users really shouldn't be faced with security decisions. They aren't as knowledgeable as the typical IT professional and they often aren't going to make the right choice. We need to make the right choice for them and prevent malicious exploits from reaching their desktops in the first place. We need to push out patches and block malicious file attachments. We need to prevent the accidental execution of rogue code and block access to malicious HTML coding. Don't allow malicious code to get to the user's desktop in the first place.
Assume Firewalls and Antivirus Software Will Fail
Assume that traditional firewall and antivirus solutions will fail, because they will. As showed in Chapter 1, nearly every corporation reports universal antivirus software deployment, and yet they still report the problem as being as bad as ever. Firewalls can help, but malware is increasingly coming in and going out on allowed ports. Heck, I think any malware program that doesn't use port 80 for its malicious communications must be written by an idiot hacker. Port 80 is open on every firewall; why not use it?
Firewalls and antivirus solutions are needed, but they are not perfect defenses. Practically, I assume they will fail a few times a year. Computer security defenses should be designed following the "defense-in-depth" principle and assume that secondary and tertiary defenses will be needed to prevent what was missed by the first layers.
Protection should Be Host-Based
In order for malware to exploit a PC, it must be executed on a PC, in its memory. Malware and hackers can arrive via any input mechanism (see Figure 2-1). If bits can be sent to a PC over a connection, the input conduit can be used maliciously. This includes wirelessly, via the keyboard, modem, network card, USB devices, CD-ROMs, and floppy discs. A frequent location to put computer defenses is on the network edge or e-mail gateway. These are great locations but only as an adjunct. The best place to put a computer defense is on the computer desktop.
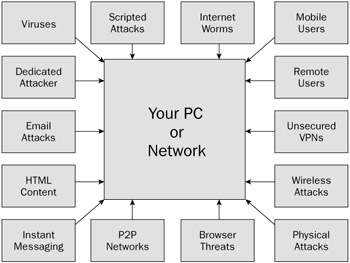
Figure 2-1
For instance, if you placed your antivirus software only on the e-mail gateway, you would miss nearly every other attack vector not occurring on port 25, including local execution and peer-to-peer programs. Sure, most of the attacks are currently coming via e-mail, but this trend isn't going to continue. Like the macro and boot viruses of yesteryear, malware will move on to other avenues once the current defenses prove consistently successful.
The August 2003 MS-Blaster RPC worm (http://securityresponse.symantec.com/avcenter/venc/data/w32.blaster.worm.html) proved that network edge protection isn't enough. When Blaster first came out, the conventional warning was that because most network Internet firewalls didn't allow port 135 traffic through it, the network and all its PCs were safe. Then remote laptop users and other infected mobile users (e.g., consultants, part-time workers, etc.) logged in a few days later with infected host computers. Once the Blaster worm was around the edge firewall, every unpatched PC host fell victim. The MS-Blaster worm proved that firewall protection must be moved down to the desktop.
If you deploy defenses on the desktop level, you will be able to catch the threat no matter where it originates. Having protection on both the desktop and the network is a great strategy, but if you have money only for one location, choose the desktop.
Practice Defense-In-Depth
With the latter point made, you should always practice defense-in-depth computer security when possible. No one computer security initiative works perfectly. Computer security will rarely be applied consistently across the environment. Somebody always misses something. Computers break, automation tools are never perfect, and it is a rare environment with nothing but the latest operating system tools and applications.
Defense-in-depth is the practice of placing security defenses at varying, often overlapping, logical locations within the enterprise. As Figure 2-2 shows, defense-in-depth includes the following locations:
-
Physical
-
Network
-
Host
-
Data
-
Application
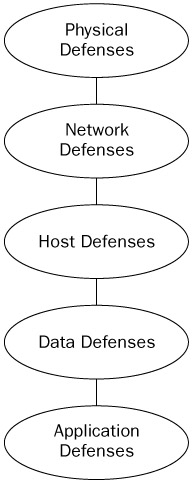
Figure 2-2
These locations somewhat, and rightly, mimic the layers of the OSI model. First, if a hacker has physical access to a computer, then they can do anything to it. They can steal it, modify it, hack it, or destroy it. You must provide physical security mechanisms to prevent malicious attack.
Second, network defenses are a great place to stop malicious attacks before they can reach the computers. For example, even when both the network and the desktop antivirus systems can catch a particular virus, it doesn't hurt to stop it before it gets to the PC. By stopping it at the network level, the PC's CPU resources don't have to be utilized to stop the viruses. Plus, network security devices allow centralized control. Just don't rely on network defenses to work perfectly.
As discussed in the previous section, host defenses are crucial to prevent malware because all malware must be executed on the host in order to be successful. Data defenses references how data can be used to compromise a computer. For example, a macro virus is made up of scripting languages and is stored in a document as data. SQL injection attacks use malformed data to extract confidential information from a database. Data has long been used to compromise computer systems, and application vendors and programmers need to write their programs to expect, and deal with, malformed data. Lastly, the applications themselves are frequently used to exploit a PC. Buffer overflows are the most frequent type of application attack, but you must include nearly every other type of malware program that accomplishes its work through end-user execution.
Defense-in-depth means including defenses at multiple layers to catch what others might have missed. Defense-in-depth also means overlapping different vendor products when possible and practical. There is no doubt that two products in the same defense class will always catch more malware than a single product from a single vendor. For example, consider using one vendor's product on your Internet gateway, another on your e-mail server, and still another on your computer desktop. The most successful e-mail security providers, such as MessageLabs (www.messagelabs.com) and Postini (www.postini.com), use multiple antivirus e-mail engines to catch more viruses. Many studies, (including this one on anti-spyware products at http://windowssecrets.com/comp/050127), proved that even when one product is vastly superior to others, using two products always increased detection rates. Of course, although multiple vendor products catch more malware and decrease overall risk, the strategy must be weighed against the added overhead and cost of managing multiple platforms.
Prevent Malware from Hiding Where It Likes to Hide
Most automated malware must hide itself in Windows in order to be executed when the computer is rebooted. Thus, a good security defense is to prevent malware from hiding where it normally likes to hide (see Table 1-1 in Chapter 1). In particular, Chapter 3, "NTFS Permissions 101," will describe how to prevent malware from hiding in the operating system; and Chapter 6, "Protecting High-Risk Registry Entries," will explain how to prevent malware from hiding in the registry.
Minimize Potential Attack Vectors, Decrease Attack Space
Every installed service, application, and running process on a PC is a potential attack vector. By decreasing the number of them, you will decrease the risk of successful exploitation. Chapter 5, "Protecting High-Risk Files," Chapter 7, "Tightening Services," and Chapter 8, "Using IPSec," discuss decreasing attack vectors.
Security must Be Automated
Security is relatively easy. It's consistency that is hard. We know how to prevent viruses, worms, and trojans, but consistently applying the recommended security defenses all the time requires automation. If you don't automate security, it won't get done consistently. Chapters 14, "Group Policy Explained," and Chapter 15, "Designing a Secure Active Directory Infrastructure," discuss automation.
With these overall guiding principles in place, the practical defense steps can be discussed.
EAN: 2147483647
Pages: 122