| Question 1 | You are designing a simple network for a small publishing company. The company has a single two-story building that houses all 44 employees. The company wishes to be connected to the Internet and an ISDN BRI link will be installed in the coming weeks. The company is using an off-site hosting company to host the corporate Web site. There are five servers located on site, two of which are used for sharing files and printers to the employees, one is used for email, one runs a database server, and the other authenticates logins. All employees have workstations or laptops. The company expects to have 10% more employees within the next two years . Which of the following design decisions would you recommend given this information? (Select two answers, each forms a part of the solution.) -
A. Purchase four 12-port hubs. Uplink three of the hubs to the fourth. Connect the workstations, laptops, and servers to the hubs. -
B. Purchase two 24-port Cisco switches with two uplink ports. Uplink the first switch to the second. Connect the workstations, laptops, and servers to the switches. -
C. Purchase a single 48-port Cisco switch. Connect the ISDN line to the switch's uplink port. Connect the workstations, laptops, and servers to the switch. -
D. Purchase a single 48-port Cisco switch and a 12-port switch. Use the uplink ports on the switches to connect them together. Connect the workstations, laptops, and servers to the switch. -
E. Purchase a Cisco router. Connect the ISDN line to the router. Connect the router to the 48-port switch. -
F. Purchase a Cisco router. Connect the ISDN line to the router. Connect the router to one of the 24 port switches. -
G. Purchase a Cisco router. Connect the ISDN line to the router. Connect the router to the 12-port hub that has the other three uplinked to it. |
| Question 2 | You have been asked to design a simple LAN for an accounting company. The accounting company is located in an office park. There are 120 employees located in three buildings. Each employee has a computer. The buildings are each approximately 180 meters from each other. The buildings are named Building A, Building B, and Building C. The largest number of employees, 50, is in Building B. The smallest number, 30, is located in Building A. You wish to network all of these buildings together, provide access for all employees to the network, and connect them to an ISDN PRI line running from Building A to the company's ISP. Which of the following schemes will best do this? -
A. Purchase 10 12-port Cisco switches. Place 2 in Building C, 5 in Building B, and 3 in Building C. Use CAT 5 UTP cable to connect all of the hosts to the switches. Use CAT 5 UTP to connect the uplink ports of one of the switches in each building to the switches in the other two. Purchase a Cisco router and install it in Building A. Connect the router to the ISDN line as well as one of the switches. -
B. Purchase 3 48-port Cisco switches and a single 12-port Cisco switch. Place one 48-port switch in each building. Place the 12-port switch in Building B. Use CAT 5 UTP to connect all of the hosts to the switches. Use CAT 5 UTP to connect the uplink ports on one of the switches in each building to the switches in the other two. Use the uplink port on the 12-port switch to connect it to that building's 48-port switch. Purchase a Cisco router and install it in Building A. Connect the router to the ISDN line as well as the 48-port switch. -
C. Purchase 3 48-port Cisco switches. Place one in each building. Use CAT 5 UTP to connect all of the hosts to the switches. Use CAT 5 UTP to connect the uplink ports on one of the switches in each building to the switches in the other two. Purchase a Cisco router and install it in Building A. Connect the router to the ISDN line as well as the 48-port switch. -
D. Purchase 3 48-port Cisco switches and a single 12-port Cisco switch. Place one 48-port switch in each building. Place the 12-port switch in Building B. Use CAT 5 UTP to connect all of the hosts to the switches. Use CAT 5 UTP with repeaters (no segment more than 95 meters) to connect the uplink ports on one of the switches in each building to the switches in the other two. Use the uplink port on the 12-port switch to connect it to that building's 48-port switch. Purchase a Cisco router and install it in Building A. Connect the router to the ISDN line as well as the 48-port switch. |
| Question 3 | Rooslan has been allocated the network range 192.168.20.0 /24. From this range he needs to create four subnets. The first subnet must support 90 hosts. The second must support 40 hosts. The third must support 30 hosts, and the final network must support 24 hosts. Which of the following schemes will meet Rooslan's needs? -
A. First: 192.168.20.0 /25, Second: 192.168.20.128 /26, Third: 192.168.20.192 /27, Fourth: 192.168.20.240 /28 -
B. First: 192.168.20.0 /25, Second: 192.168.20.128 /26, Third: 192.168.20.192 /27, Fourth: 192.168.20.224 /27 -
C. First: 192.168.20.0 /26, Second: 192.168.20.64 /26, Third: 192.168.20.192 /27, Fourth: 192.168.20.224 /27 -
D. First: 192.168.20.0 /25, Second: 192.168.20.128 /26, Third: 192.168.20.192 /28, Fourth: 192.168.20.240 /28 |
| Question 4 | Which of the following /24 subnets can be supernetted into a larger network? -
A. 10.10.20.0 /24 and 10.10.21.0 /24 into 10.10.20.0 /23 -
B. 10.10.21.0 /24 and 10.10.22.0 /24 into 10.10.21.0 /23 -
C. 10.10.130.0 /24, 10.10.131.0 /24, 10.10.132.0 /24, and 10.10.133.0 /24 into 10.10.130.0 /22 -
D. 10.10.164.0 /24, 10.10.165.0 /24, 10.10.166.0 /24, and 10.10.167.0 /24 into 10.10.165.0 /22 |
| Question 5 | You are trying to select a routing protocol to use on a large internetwork. 60% of the routers on the network are Cisco systems running IOS, and 40% are manufactured by other vendors. Which of the following routing protocols are unlikely to be supported by the 40% of routers manufactured by other vendors ? (Select all that apply.) -
A. IGRP -
B. RIP -
C. RIPv2 -
D. OSPF -
E. BGP -
F. EIGRP |
| Question 6 | There are 326 routers used in a network for a government department. Some routes are 25 hops in diameter. Which of the following routing protocols could not fully map this network? -
A. OSPF -
B. IGRP -
C. RIPv2 -
D. EIGRP |
| Question 7 | You are designing a network for a small bank that has branch offices spread all across the state. There are seven branch offices and a central office. Four of the branch offices have a single TCP/IP subnet, and three of the branch offices have two TCP/IP subnets. Each branch office is connected via ISDN line to the central office. What is the minimum number of routers that will be required for the branch offices if VLANs are not used for branch office hosts to communicate with the central office? |
| Question 8 | You are designing a network for an insurance company that has offices in several capital cities around the country. There is a single head office and six branch offices. You are going to use ISDN BRI leased lines to connect each office to the head office. You also want to configure the network so that it will still operate if a single ISDN BRI line fails. If this occurs, data transmission should be sent via an ISDN BRI line to another branch office, which will then forward the data to the head office. How many ISDN lines will be required to implement such a network? |
| Question 9 | You wish to write an access list that allows access from hosts with IP addresses in the range 10.10.0.0 through to 10.10.255.255. Which of the following access lists will achieve this goal? -
A. ACCESS LIST 1 PERMIT 10.10.0.0 255.255.255.0 -
B. ACCESS LIST 201 PERMIT 10.10.0.0 255.255.255.0 -
C. ACCESS LIST 1 PERMIT 10.10.0.0 255.255.0.0 -
D. ACCESS LIST 201 PERMIT 10.10.0.0 255.255.0.0 -
E. ACCESS LIST 1 PERMIT 10.10.0.0 0.0.255.255 -
F. ACCESS LIST 201 PERMIT 10.10.0.0 255.255.0.0 |
| Question 10 | You have the following access list: ACCESS LIST 1 DENY 10.100.45.0 0.0.0.127 ACCESS LIST 1 PERMIT 10.100.20.0 0.0.255.255 Interface e0 is connected to the internal network, which includes the IP range 10.100.0.0 /16. Access list 1 is applied inbound on interface e0. Interface s1 is connected to internal network 10.200.0.0 /16. Which of the following host addresses will not be able to send traffic through the router to the network that is connected to interface s1? (Select all that apply.) -
A. 10.100.240.223 -
B. 10.100.20.132 -
C. 10.100.45.223 -
D. 10.100.45.25 -
E. 10.100.45.118 |
| Question 11 | One of your clients has asked you to implement a WAN service that will be relatively inexpensive, provide extra data transfer speed if required, and allow new sites to be added to the network quickly. Which of the following WAN technologies will allow this? |
| Question 12 | Your company has decided to go with a leased-line solution in provisioning WAN connections. They want to use the default leased-line protocol for Cisco systems because Cisco manufactures all of the routers and switches on the corporate network. When on a leased-line WAN service, which of the following data-link protocols is the default used by Cisco routers? -
A. SLIP -
B. PPP -
C. HDLC -
D. LAPB |
| Question 13 | You are working on a network that only supports RIPv1. Which of the following IOS command sequences will force a Cisco router named router to only send and receive RIPv1, rather than RIPv1 and RIPv2 routing updates? -
A. router#configure terminal router(config)#router rip router(config-router)#version 1 router(config-router)#end -
B. router#configure terminal router(config)#interface e0 router(config-if)#router ripv1 -
C. router#configure terminal router(config)#router ripv1 -
D. router#configure terminal router(config)#interface e0 router(config-if)#set rip version 1 |
| Question 14 | You are adding a router to a network that is entirely made up of Cisco equipment. The routing protocol in use is EIGRP, which is a proprietary protocol from Cisco. The EIGRP's AS (Autonomous System) number is 77. Which of the following IOS command sequences will configure EIGRP with an AS of 77 for the network 10.10.50.0? (Assume that the appropriate interface has already been configured.) -
A. NEWROUTER(config)#router rip 77 NEWROUTER(config-router)#network 10.50.10.0 NEWROUTER(config-router)#end -
B. NEWROUTER(config)#router eigrp 77 NEWROUTER(config-router)#network 10.50.10.0 NEWROUTER(config-router)#end -
C. NEWROUTER(config)#router eigrp 77 NEWROUTER(config-router)#network 10.10.50.0 NEWROUTER(config-router)#end -
D. NEWROUTER(config)#router eigrp 66 NEWROUTER(config-router)#network 10.50.10.0 NEWROUTER(config-router)#end |
| Question 15 | Which of the following sets of IOS commands will set the IP address of router ODLT1's e0 interface to 10.10.40.1 /27, the address of the s1 interface to 10.10.41.1 /29, and the address of the s2 interface to 10.10.40.33 /28? (Select all that apply.) -
A. ODLT1(config)#interface e0 ODLT1(config-if)#ip address 10.10.40.1 255.255.240.0 ODLT1(config-if)#no shut -
B. ODLT1(config)#interface e0 ODLT1(config-if)#ip address 10.10.40.1255.255.224.0 ODLT1(config-if)#no shut -
C. ODLT1(config)#interface s1 ODLT1(config-if)#ip address 10.10.41.1 255.255.240.0 ODLT1(config-if)#no shut -
D. ODLT1(config)#interface s2 ODLT1(config-if)#ip address 10.10.40.33 255.255.248.0 ODLT1(config-if)#no shut -
E. ODLT1(config)#interface s2 ODLT1(config-if)#ip address 10.10.40.33 255.255.240.0 ODLT1(config-if)#no shut -
F. ODLT1(config)#interface s1 ODLT1(config-if)#ip address 10.10.41.1 255.255.248.0 ODLT1(config-if)#no shut |
| Question 16 | You want to configure the e0 interface of a router with the IP address 10.10.10.31. Which of the following steps taken in IOS will apply this address with a subnet mask, thereby making it addressable on the network to interface e0? -
A. ROUTER(config)#interface e0 ROUTER(config-if)#ip address 10.10.10.31 255.255.255.0 ROUTER(config-if)#no shut -
B. ROUTER(config)#interface e0 ROUTER(config-if)#ip address 10.10.10.31 255.255.255.192 ROUTER(config-if)#no shut -
C. ROUTER(config)#interface e0 ROUTER(config-if)#ip address 10.10.10.31 255.255.255.224 ROUTER(config-if)#no shut -
D. ROUTER(config)#interface e0 ROUTER(config-if)#ip address 10.10.10.31 255.255.255.240 ROUTER(config-if)#no shut -
E. ROUTER(config)#interface e0 ROUTER(config-if)#ip address 10.10.10.31 255.255.255.248 ROUTER(config-if)#no shut |
| Question 17 | Which of the following protocols does Cisco recommend that you use to support a router to act as a terminal server to manage other routers? -
A. RADIUS -
B. TACACS+ -
C. IGRP -
D. OSPF |
| Question 18 | What is the maximum number of VLANs that have a separate spanning tree supported by Catalyst 1900 switches? -
A. 8 -
B. 16 -
C. 32 -
D. 64 -
E. 128 |
| Question 19 | Which of the following IOS commands issued on a Cisco Catalyst 1900 switch will display the VLAN membership of each of the ports? -
A. list ports -
B. list VLAN -
C. show VLAN -membership -
D. VLAN -membership |
| Question 20 | You are designing a LAN for a large manufacturing company's production site. There is a single factory building that is 200 meters long. The first 50 meters are taken up with office space for the administrative staff. The rest of the factory is filled with large equipment that occasionally generates electrical interference. There are 50 workstations and three servers located in the administrative area. Throughout the rest of the factory there are 20 workstations. All of these workstations are located between 120 and 180 meters from the administrative area. All need to be networked to each other. You have the following equipment available: 80 lengths of UTP cable (of whatever is required length) 25 lengths of STP cable (of whatever is required length) 1 48-port Cisco Catalyst switch 2 24-port Cisco Catalyst switches 2 repeaters What should you do to provide connectivity to all of these hosts given the available equipment? -
A. Place the 48-port and one 24-port switch in the administration area. Connect them to each other using a single UTP cable. Connect all of the hosts in the administration area to these two switches with lengths of UTP cable. Place the second 24-port catalyst switch in a safe position 150 meters from the administration area. Connect two 90-meter lengths of UTP cable together with one of the repeaters and use this longer cable to connect the 48-port switch with the 24-port switch out in the factory. Use 20 lengths of STP cable to connect the hosts on the factory floor to the switch. -
B. Place the 48-port and one 24-port switch in the administration area. Connect them to each other using a single STP cable. Connect all of the hosts in the administration area to these two switches with lengths of UTP cable. Place the second 24-port catalyst switch in a safe position 150 meters from the administration area. Connect two 90-meter lengths of STP cable together with one of the repeaters and use this longer cable to connect the 48-port switch with the 24-port switch out in the factory. Use 20 lengths of UTP cable to connect the hosts on the factory floor to the switch. -
C. Place both 24-port switches in the administration area. Connect them to each other using a single UTP cable. Use lengths of UTP cable to connect all of the hosts in the administration area to these two switches. Place the 48-port catalyst switch in a safe position 150 meters from the administration area. Connect two 90-meter lengths of STP cable together with one of the repeaters and use this longer cable to connect one of the 24-port switches with the 48-port switch out in the factory. Use 20 lengths of UTP cable to connect the hosts on the factory floor to the switch. -
D. Place the 48-port and one 24 port-switch in the administration area. Connect them to each other using a single UTP cable. Use lengths of UTP cable to connect all of the hosts in the administration area to these two switches. Place the second 24-port catalyst switch in a safe position 150 meters from the administration area. Connect two 90-meter lengths of STP cable together with one of the repeaters and use this longer cable to connect the 48-port switch with the 24-port switch that is located out in the factory. Use 20 lengths of STP cable to connect the hosts on the factory floor to the switch. |
| Question 21 | You have been asked to help with a local school's LAN that has become bogged down due to heavy data traffic. The LAN currently has 220 hosts on a single TCP/IP subnet. The school administration does not want this network resubnetted. Which of the following devices can be implemented on the network to reduce the amount of unicast traffic on each segment of the network? (Select all that apply.) -
A. Bridge -
B. Switch -
C. Router -
D. Repeater |
| Question 22 | You wish to configure a switch so that it examines each frame for errors in its entirety before forwarding it on to its destination. For which of the following switching methods should a Catalyst 1900 switch be configured to perform this function? |
| Question 23 | You wish to configure a Cisco Catalyst switch to use a method of switching that will perform some error correction on frames transmitted across the network, but that the latency caused by that error correction will not increase with the size of the frame. Which of the following switching methods should you implement? |
| Question 24 | Which of the following IOS commands will back up the starting configuration to a TFTP server located on IP address 10.10.10.99? -
A. backup start-config tftp 10.10.10.99 -
B. backup running-config tftp 10.10.10.99 -
C. copy tftp start-config -
D. copy start-config tftp |
| Question 25 | Which of the following commands can be used to copy the startup configuration to the running configuration on a switch? -
A. copy run start -
B. copy start run -
C. overwrite run start -
D. overwrite start run |
| Question 26 | Which of the following commands will set a router's host name to PHOENIX? |
| Question 27 | Which of the following IOS command sequences will set the enable password to CAPRICORNUS and the console password to AQUILA on router PHOENIX? -
A. PHOENIX(config)#enable password CAPRICORNUS PHOENIX(config)#line con 0 PHOENIX(config-line)#password AQUILA -
B. PHOENIX(config)#enable password PHOENIX(config)#set password CAPRICORNUS PHOENIX(config)#line con 0 PHOENIX(config-line)#password AQUILA -
C. PHOENIX(config)#enable password CAPRICORNUS PHOENIX(config)#line vty 0 4 PHOENIX(config-line)#password AQUILA -
D. PHOENIX(config)#configure password CAPRICORNUS PHOENIX(config)#line con 0 PHOENIX(config-line)#enable password AQUILA |
| Question 28 | Which of the following settings are the defaults on a Catalyst 1900 switch when it is first powered on? -
A. CDP: Enabled -
B. Console Password: CISCO -
C. Spanning Tree: Disabled -
D. Switching Mode: Store and Forward -
E. 10BaseT port: Full Duplex |
| Question 29 | You are configuring a Cisco Catalyst 1900 switch from the command line. Which of the following groups of commands will set the IP of the switch to 10.10.10.54 /29 and the default gateway to 10.10.10.49? -
A. switch# configure terminal switch(config)#ip address 10.10.10.54 255.255.255.240 switch(config)#ip default-gateway 10.10.10.54 -
B. switch# configure terminal switch(config)#ip address 10.10.10.54 255.255.255.248 switch(config)#ip default-gateway 10.10.10.54 -
C. switch# configure terminal switch(config)#ip address 10.10.10.49 255.255.255.240 switch(config)#ip default-gateway 10.10.10.54 -
D. switch# configure terminal switch(config)#ip address 10.10.10.54 255.255.255.240 switch(config)#ip default-gateway 10.10.10.49 -
E. switch# configure terminal switch(config)#ip address 10.10.10.54 255.255.255.248 switch(config)#ip default-gateway 10.10.10.49 |
| Question 30 | Router Alpha's E0 interface is connected to the Internet. Router Alpha's S1 interface is connected to the internal network that encompasses 30 /24 bit networks from 10.10.10.0 /24 through to 10.10.40.0 /24. You have two goals. First, you want to stop traffic from network 10.10.36.0 /24 from reaching the Internet. Second, you only want traffic from the network 192.168.24.0 /24 to reach the internal network from the Internet. You have the following access lists: ACCESS LIST 1 PERMIT 192.168.24.0 255.255.255.0 ACCESS LIST 2 PERMIT 192.168.24.0 0.0.0.255 ACCESS LIST 3 DENY 10.10.36.0 255.255.255.0 ACCESS LIST 4 DENY 10.10.36.0 0.0.0.255 Which of the following describes how these access lists can be applied to meet your two goals? -
A. Apply access list 1 to interface e0 out; apply access list 3 to interface s1 in. -
B. Apply access list 1 to interface e0 in; apply access list 3 to interface s1 in. -
C. Apply access list 2 to interface e0 out; apply access list 4 to interface s1 in. -
D. Apply access list 2 to interface e0 in; apply access list 4 to interface s1 in. |
| Question 31 | You wish to block users from the network 192.168.20.0 /24, which is a network connected to interface e0, from using the FTP protocol to connect to host 192.168.40.24 on the network that is connected to interface s1. These are the only two configured interfaces on the router, and no other path exists between the networks. Which of the following will achieve this goal? -
A. Create an access list: access-list 101 deny tcp 192.168.20.0 255.255.255.0 192.168.40.24 eq ftp and apply this access list to incoming traffic on interface e0. -
B. Create an access list: access-list 101 deny tcp 192.168.20.0 0.0.0.255 192.168.40.24 eq ftp and apply this access list to outgoing traffic on interface s1. -
C. Create an access list: access-list 101 deny tcp 192.168.20.0 0.0.0.255 192.168.40.24 eq ftp and apply this access list to outgoing traffic on interface e0. -
D. Create an access list: access-list 101 deny tcp 192.168.20.0 255.255.255.0 192.168.40.24 eq ftp and apply this access list to incoming traffic on interface s1. -
E. None of the above. |
| Question 32 | You wish to configure interface s0, which will host a frame relay connection to a remote office, to send keepalive packets through the PVC every 20 seconds. Keepalive packets verify that the path is still available. Which of the following IOS sequences will achieve this goal? -
A. WANROUTE(config)#interface s0 WANROUTE(config-if)#encapsulation ppp WANROUTE(config-if)#keepalive 20 WANROUTE(config-if)#end -
B. WANROUTE(config)#interface s1 WANROUTE(config-if)#encapsulation frame-relay WANROUTE(config-if)#keepalive 20 WANROUTE(config-if)#end -
C. WANROUTE(config)#interface s0 WANROUTE(config-if)#encapsulation ppp WANROUTE(config-if)#keepalive 5 WANROUTE(config-if)#end -
D. WANROUTE(config)#interface s0 WANROUTE(config-if)#encapsulation frame-relay WANROUTE(config-if)#keepalive 20 WANROUTE(config-if)#end |
| Question 33 | Which layer of the OSI model represents where you would begin troubleshooting problems with frames? -
A. Layer 1 -
B. Layer 2 -
C. Layer 3 -
D. Layer 4 |
| Question 34 | Which layer of the conceptual OSI model represents where you would begin troubleshooting problems with IP addressing? -
A. Layer 1 -
B. Layer 2 -
C. Layer 3 -
D. Layer 4 |
| Question 35 | Your local area network is suffering from frequent overloads of broadcast traffic. Which of the following hardware devices could not be used to reduce the amount of broadcast traffic on the LAN? (Select two.) |
| Question 36 | You wish to decrease the amount of time that an RIP network takes to converge after a topology change. You want the update period to be 10 seconds. You also want to set the invalid route timer to 100 seconds, the hold-down timer to 100 seconds, and the flush timer to 110 seconds. Which of the following IOS commands, entered after router rip , will enable you to achieve this goal? -
A. timers basic 10 100 100 110 -
B. set rip timers 20 100 100 110 -
C. configure rip timers 20 100 100 110 -
D. routing update 10 100 100 95 |
| Question 37 | You have inherited a /24 network that has been separated into several /29 networks. The original network was 192.168.10.0 /24. You are currently looking at a list of IP addresses that can be assigned to router interfaces. Which of the following IP addresses can be assigned to router interfaces given this networking scheme? -
A. 192.168.10.15 -
B . 192.168.10.223 -
C . 192. 168.10.184 -
D. 192.168.10.153 |
| Question 38 | Your national company uses the 192.168.0.0 private address space. Your state network has been assigned the 192.168.100.0 /24 and 192.168.101.0 /24 address space. You have subnetted the two address spaces into a total of 16 equal- sized networks. Which of the following IP addresses cannot be assigned to hosts on the networks within your state? -
A. 192.168.100.31 -
B. 192.168.101.63 -
C. 192.168.101.203 -
D. 192.168.100.227 -
E. 192.168.100.129 |
| Question 39 | Your network consists of four switches, two repeaters, a single router, two subnets, and 160 hosts. Switches one and two are on subnet 192.168.10.0 /25, and switches three and four are on subnet 192.168.10.128 /25. Hosts 192.168.10.5 through 192.168.10.45 are connected to switch one. Hosts 192.168.10.46 through 192.168.10.86 are connected to switch two. Two segments of UTP, connected via a repeater, connect switch one to switch two. Hosts 192.168.10.130 through hosts 192.168.10.170 are connected to switch three. Hosts 192.168.10.171 through hosts 192.168.10.211 are connected to switch four. Switch three is connected to switch four via two segments of UTP cable connected together via a repeater. Switch four is connected via UTP to the router. Switch one is connected to the router. Host 192.168.10.50 cannot ping host 192.168.10.165. Host 192.168.10.70 can ping host 192.168.10.200. Assuming all of the hosts work, which of the following devices could be faulty? (Select all that apply.) |
| Question 40 | You have six switches, 120 hosts, three networks, and one router. Your network configuration can be summarized as follows : Switches Alpha and Beta service hosts on Network 10.10.10.0 /24. This network is connected to interface e0 on the router. The hosts on switch Alpha have IP addresses between 10.10.10.10 and 10.10.10.30. The hosts on switch Beta have IP addresses between 10.10.10.50 and 10.10.10.70. Switch Alpha is connected to switch Beta. Switch Beta is connected to the router. Switches Gamma and Delta service hosts on Network 10.10.20.0 /24. This network is connected to interface s1 on the router. The hosts on switch Gamma have IP addresses between 10.10.20.10 and 10.10.20.30. The hosts on switch Delta have IP addresses between 10.10.20.50 and 10.10.20.70. Switch Gamma is connected to switch Delta. Switch Delta is connected to the router. Switches Epsilon and Omega service hosts on network 10.10.30.0 /24. This network is connected to interface s2 on the router. The hosts on switch Epsilon have IP addresses between 10.10.30.10 and 10.10.30.30. The hosts on switch Omega have IP addresses between 10.10.30.50 and 10.10.30.70. Switch Epsilon is connected to switch Omega. Switch Omega is connected to the router. See Figure 15.1 for a diagram.
Figure 15.1. 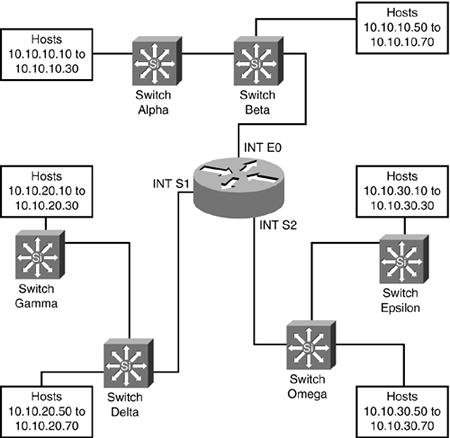
Until yesterday , all hosts were able to communicate with each another. This morning your users have reported some problems. You perform some testing and come up with the following results: Host 10.10.20.24 can ping host 10.10.20.58 Host 10.10.10.14 can ping host 10.10.30.68 Host 10.10.30.27 can ping host 10.10.10.57 Host 10.10.30.65 cannot ping host 10.10.20.51 Given this information, and assuming that all hosts are functioning properly, which of the following networks might have caused the problem? -
A. Interface e0 of the router is down -
B. Interface s1 of the router is down -
C. Interface s2 of the router is down -
D. Switch Delta is down -
E. Switch Omega is down -
F. Switch Beta is down |
| Question 41 | You have the following access list: ACCESS LIST 1 PERMIT 10.10.0.0 0.0.255.255 ACCESS LIST 1 DENY 10.10.100.0 0.0.0.255 ACCESS LIST 1 DENY 10.10.130.0 255.255.255.0 ACCESS LIST 1 DENY 10.10.150.0 0.0.0.255 You want to make sure that traffic from the networks 10.10.100.0 /24 and 10.10.150.0 /24 are blocked, but still allow all other traffic from the 10.10.0.0 /16 network. How should you modify the access list? (Select two.) -
A. Delete line three of the access list. -
B. Modify line four of the access list to ACCESS LIST 1 DENY 10.10.150.0 255.255.255.0 . -
C. Modify line three of the access list to ACCESS LIST 1 DENY 10.10.130.0 0.0.0.255 . -
D. Move line one of the access list to the end of the access list. -
E. Modify line two of the access list to ACCESS LIST 1 DENY 10.10.100.0 255.255.255.0 . |
| Question 42 | You have the following access list: ACCESS LIST 101 deny tcp any host 192.168.10.21 eq 80 ACCESS LIST 101 deny tcp 192.168.20.0 0.0.0.255 eq telnet ACCESS LIST 101 deny tcp 192.168.0.0 0.0.255.255 192.168.10.22 eq ftp ACCESS LIST 101 allow tcp 192.168.44.0 0.0.0.255 192.168.10.22 eq ftp You want to achieve the following: Block telnet access to any host on the 192.168.10.0 /24 network from the 192.168.20.0 /24 network. Allow all hosts access to the Web server on host 192.168.10.21. Allow hosts on network 192.168.44.0 /24 ftp access to host 192.168.10.22 but block ftp access to this host from other networks in the 192.168.0.0 /24 range. Which of the following modifications do not have to be made to the access list? (Select all that apply.) -
A. Change line one to ACCESS LIST 101 allow tcp any host 192.168.10.21 eq 80 . -
B. Change line two to ACCESS LIST 101 deny tcp 192.168.20.0 0.0.0.255 192.168.10.0 0.0.0.255 eq telnet . -
C. Rearrange the access list so that line 4 is above line 3. -
D. Change line one to ACCESS LIST 101 allow tcp any host 192.168.10.21 0.0.255.255 eq 80 . -
E. Change line two to ACCESS LIST 101 allow tcp 192.168.20.0 0.0.0.255 192.168.10.0 0.0.0.255 eq telnet . |
| Question 43 | Which of the following best describes how information progresses up the OSI model from Layer 1 to Layer 5? -
A. Bits -> Packets -> Frames -> Datagrams -> Segments -
B. Bits -> Datagrams -> Frames -> Packets -> Segments -
C. Bits -> Frames -> Packets -> Segments -> Datagrams -
D. Bits -> Frames -> Packets -> Datagrams -> Segments |
| Question 44 | Which of the following correctly map the appropriate layer with the description of information that is transmitted at that layer? (Select all that apply.) -
A. Layer 1 = Bits -
B. Layer 2 = Packets -
C. Layer 3 = Frames -
D. Layer 4 = Segments -
E. Layer 5 = Datagrams |
| Question 45 | Which of the following best describes the spanning tree process? -
A. Spanning tree creates a series of redundant links between switches. -
B. Spanning tree creates a loop network so that data may reach its destination via multiple paths. -
C. Spanning tree blocks of ports on redundant links so that there is only one path through the LAN from one switch to the next. -
D. Spanning tree creates multiple links so that bandwidth can be aggregated creating faster transfer speeds. |
| Question 46 | How many STP root bridges are on a network that contains two TCP/IP subnets separated by a Cisco router, with each subnet hosting six Cisco Catalyst 1900 switches? |
| Question 47 | Which of the following correctly describes the difference between broadcast, unicast, and multicast transmissions on a LAN? -
A. Unicast transmissions are sent from one host to all hosts. Broadcast transmissions are sent from all hosts to one host. Multicast transmissions are sent from some hosts to some other hosts. -
B. Unicast transmissions are sent from a single host to another single host. Broadcast transmissions are sent from a single host to all hosts on the LAN. Multicast transmissions are sent from a single host to a group of hosts. -
C. Unicast transmissions are sent from a single host to another single host. Broadcast transmissions are sent from a single host to a small group of hosts. Multicast transmissions are sent from a single host to all hosts on the LAN. -
D. Unicast transmissions are sent from a single host to a group of hosts. Broadcast transmissions are sent from a single host to all hosts on the LAN. Multicast transmissions are sent from a single host to another single host. |
| Question 48 | Which of the following statements is true? -
A. Switches, without VLANs, reduce the size of broadcast domains. -
B. Switches, without VLANs, reduce the size of unicast collision domains. -
C. Routers reduce the size of broadcast domains. -
D. Switches, when configured with two or more VLANs, reduce the size of broadcast domains. |
| Question 49 | Which of the following routing protocols are, or make use of, the Distance Vector process? -
A. RIPv2 -
B. OSPF -
C. IGRP -
D. EIGRP |
| Question 50 | Which of the following routing protocols are exterior routing protocols? -
A. RIPv2 -
B. IGRP -
C. OSPF -
D. BGP |
| Question 51 | You want to transfer files back and forth across a network, but you are not as concerned about error correction as you are about the speed of the transfer. Which of the following protocols might you utilize? -
A. HTTP -
B. Telnet -
C. TFTP -
D. FTP |
| Question 52 | Which of the following ports on a router can be used to initially configure a router via a special cable to a laptop that is running appropriate software? -
A. console port -
B. auxiliary port -
C. UTP port -
D. serial port |
| Question 53 | Which of the following Router memory types stores the IOS image? -
A. RAM -
B. ROM -
C. FLASH -
D. NVRAM |
| Question 54 | You have the following access list: ACCESS LIST 101 deny tcp 10.10.0.0 0.0.255.255 192.168.10.24 eq ftp ACCESS LIST 101 deny tcp 10.10.10.0 0.0.0.255 192.168.10.24 eq 80 ACCESS LIST 101 allow tcp 10.10.10.0 0.0.0.128 192.168.10.24 eq telnet ACCESS LIST 101 allow tcp 10.10.10.0 0.0.0.255 192.168.10.25 eq 80 ACCESS LIST 101 allow tcp 10.10.0.0 0.0.255.255 192.168.10.25 eq ftp Which of the following packets will be discarded while passing through an interface that has this access list applied? (Select all that apply.) -
A. FTP packets from host 10.10.234.65 to host 192.168.10.24 will be discarded. -
B. HTTP packets from host 10.10.20.0 to host 192.168.10.24 will be discarded. -
C. Telnet packets from host 10.10.10.15 to host 192.168.10.24 will be discarded. -
D. FTP packets from host 10.10.99.65 to host 192.168.10.25 will be discarded. -
E. HTTP packets from host 10.10.10.47 to host 192.168.10.24 will be discarded. |
| Question 55 | You have the following access list: ACCESS LIST 102 deny tcp 10.50.0.0 0.0.255.255 192.168.10.24 eq ftp ACCESS LIST 102 deny tcp 10.60.0.128 0.0.255.127 192.168.10.24 eq ftp ACCESS LIST 102 deny tcp 10.70.0.0 0.0.0.255 192.168.10.24 eq ftp ACCESS LIST 102 deny tcp 10.80.0.0 0.0.255.255 192.168.10.24 eq ftp ACCESS LIST 102 allow tcp 10.100.0.0 0.255.255.255 192.168.10.24 eq ftp Which of the following FTP packets will be discarded while attempting to travel through an interface where this access list is applied? -
A. FTP packets from host 10.100.24.22 to host 192.168.10.24 -
B. FTP packets from host 10.51.101.223 to host 192.168.10.24 -
C. FTP packets from host 10.60.103.54 to host 192.168.10.24 -
D. FTP packets from host 10.60.94.200 to host 192.168.10.24 -
E. FTP packets from host 10.79.105.22 to host 192.168.10.24 |