Fast Track - How To Implement the Guidance
Goal and Scope
This guide helps you to design, build, and configure hack-resilient Web applications. These applications reduce the likelihood of successful attacks and mitigate the extent of damage should an attack occur. Figure 1 shows the scope of the guide and its three-layered approach: securing the network, securing the host, and securing the application.
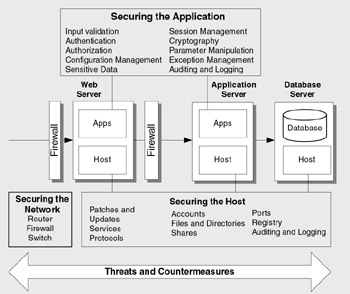
Figure 1: The scope of the guide
The guide addresses security across the three physical tiers shown in Figure 1. It covers the Web server, remote application server, and database server. At each tier , security is addressed at the network layer, host layer, and application layer. Figure 1 also shows the configuration categories that the guide uses to organize the various security configuration settings that apply to the host and network, and the application vulnerability categories, which are used to structure application security considerations.
EAN: 2147483647
Pages: 613