Speed vs. Security Trade-Offs
The example application we outlined in the previous section is secure and uses Kerberos authentication throughout. Only one set of authentication and authorization procedures is followed—all security policy is performed and enforced by the operating system, not by custom security code. There are times, however, when you might not want to use such a solution; or perhaps you'll supplement this base example with your own schemes. Note that you can gain some performance benefit from not using authenticated connections throughout, most notably in the areas of database connection pooling and the cost of delegating, which we'll look at next.
Database and Connection Pooling
We've already alluded to connection pooling previously in this book. Essentially, authenticated connections to a database defeat connection pooling. But you can relax the authentication requirements a little to prevent this. Rather than impersonating the user in the COM+ application before accessing the SQL Server database, the component identifies the user and uses that identity as an argument to a SQL statement or stored procedure to access SQL Server. Using this model, you need allow only one account access to SQL Server, and the COM+ application identity and connection pooling works!
Figure 10-15 shows the two scenarios. The first scenario is the complete end-to-end impersonation and delegation model. The COM+ request to SQL Server is performed only after impersonating Alice. In the second scenario, Alice is not impersonated; rather, the COM+ application identifies Alice and uses her name as an argument to a SQL Server request. In this case, SQL Server thinks that the COM+ application process, AppAccount, is making the call. Because of the single user account between COM+ and SQL Server, database connection pooling works.
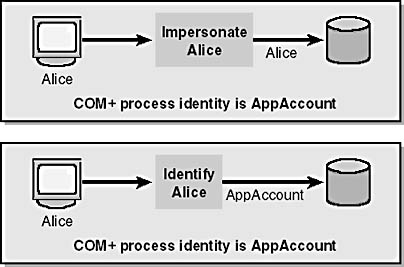
Figure 10-15. Impersonating vs. identifying a user before making a SQL Server call determines whether database connection pooling works.
The Cost of Identifying, Impersonation, and Delegation
Delegating a user account is much more expensive time wise than impersonating or identifying a user. However, speed differences are difficult to quantify owing to the numerous contributing factors. Nevertheless, you can expect delegation to be twice as costly as not delegating. Impersonating and identifying the user occur at the same speed, and impersonating or identifying is negligibly slower than an anonymous connection. This doesn't mean delegation is slow. It's not; it's just relatively slower than impersonation.
In Web sites with extremely high throughput, you might consider impersonation over delegation; but of course, delegation won't work! At least you have the option!
EAN: N/A
Pages: 138