Chapter 10 -- Building a Secure Solution
In Part II, "Technologies and Trade-Offs," we looked at some of the technologies used to build secure solutions as well as some of the trade-offs required to solve real business problems. Now let's turn our attention to the steps required to build a comprehensive solution that uses end-to-end Kerberos authentication and Microsoft Windows 2000 access control mechanisms throughout. This solution, based on the Exploration Air example discussed in Chapter 2, "A Process for Building Secure Web Applications," can be used as the basis for your own security solution. Once you have this example running, you can apply many of the trade-offs discussed in Chapter 8, "Practical Authentication and Authorization," and Chapter 9, "Practical Privacy, Integrity, Auditing, and Nonrepudiation," to map more closely to your requirements.
The chapter is divided into three major sections:
- Putting together a secure solution
- Speed vs. security trade-offs
- Configuration checklists
We assume in this chapter that you have a certain level of administration knowledge for Microsoft Windows 2000. You must know how to install Windows 2000 and how to set up Active Directory, Dynamic Host Configuration Protocol (DHCP), Domain Name System (DNS), and Windows Internet Naming Service (WINS). You can learn more about Windows 2000 network administration in the Microsoft Windows 2000 Server Resource Kit (Microsoft Press, 2000) or by referring to the Windows 2000 online help and taking a look at the checklists concerning DHCP, DNS, and WINS. Finally, we also assume you understand how to install Microsoft SQL Server and perform basic SQL Server administration.
Before looking at the steps required to configure the security solution, let's look at the overall application model, which we determined in Chapter 2 and which is shown in Figure 10-1.
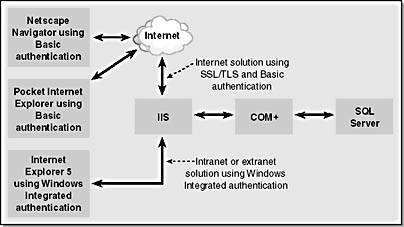
Figure 10-1. A high-level view of the solution.
Figure 10-2 shows a more detailed view of this model.
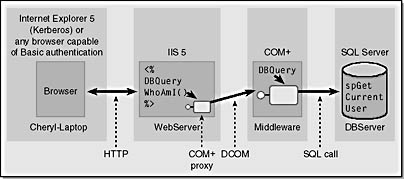
Figure 10-2. A more detailed view of the solution.
In this solution, the browser can be either Microsoft Internet Explorer 5 (or later) using Windows Integrated authentication or virtually any other browser supporting Basic authentication and Secure Sockets Layer/Transport Layer Security (SSL/TLS). These browsers will allow Kerberos identity to pass to the back-end database, SQL Server.
EAN: N/A
Pages: 138