Architecture
COM+ 1.0 security is articulated around the interaction between a client and a COM+ 1.0 application: a client performing a method call against one of the application components, as shown in Figure 7-2.

Figure 7-2. A COM+ method call.
Note that from a COM+ 1.0 perspective the application components are the objects of the client request—that is, the resources requiring protection.
To make component authorization meaningful, it is necessary to authenticate the client. Furthermore, the server identity might also need to be authenticated to alleviate client concerns. Finally, the method call itself requires protection against information disclosure and data tampering—the confidentiality and integrity protection that is paramount in a distributed setting when the method call is carried over DCOM.
The goal of COM+ 1.0 security is to provide mechanisms that address these concerns and simplify the programmer's task. As with the other COM+ 1.0 services, this is accomplished by providing a declarative model—to cover the proverbial 80 percent case—in which both authorization and authentication are configured.
To address more elaborate scenarios—for example, the delegation scenario in which the COM+ application needs to perform work under the client authority—this configuration paradigm is supplemented by programmatic controls to express the few idioms required to support those scenarios.
Authorization Overview
For authorization, applications control access with roles, which represent application-specific categories of principals. In COM+ 1.0, these principals are Windows 2000-authenticated principals. Protection is configured to restrict access to method calls or programmed to restrict access to private application resources. In addition, COM+ 1.0 supports the Windows 2000 impersonation-style access control when the application accesses resources on the client's behalf, as shown in Figure 7-3.
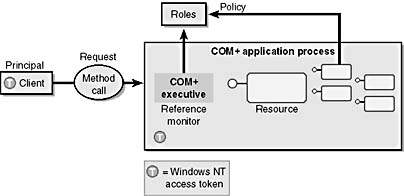
Figure 7-3. COM+ 1.0 authorization overview.
Now let's turn our attention to another critical aspect of security: authentication.
Authentication Overview
For authentication, COM+ 1.0 relies completely on Windows 2000. This means, as noted in the previous section, that COM+ 1.0 principals are Windows 2000 principals. In addition, COM+ 1.0 uses the authentication services provided by Windows 2000. This is accomplished through various mechanisms, such as the layering of DCOM over Microsoft remote procedure call (RPC), which in turn relies on the various Windows 2000 Security Support Providers (SSPs)—for example, Kerberos and NTLM—to offer authentication, confidentiality, and integrity services. Figure 7-4 gives an overview of COM+ 1.0 authentication.
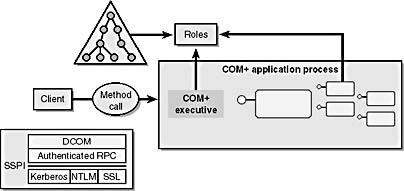
Figure 7-4. COM+ 1.0 authentication overview.
COM+ 1.0 provides a thin configuration layer that controls various authentication settings. This authentication control, as we'll see in "Configuring Authentication" can be applied administratively at various levels of configuration granularity and, in the rare cases in which it's needed, programmatically.
EAN: N/A
Pages: 138